Expanding Google AI in Workspace with new zero trust and digital sovereignty controls
Yulie Kwon Kim
VP, Product - Workspace
Andy Wen
Senior Director, Product Management, Workspace
Try Google Workspace at No Cost
Get a business email, all the storage you need, video conferencing, and more.
SIGN UPSecurity, confidentiality, and compliance continue to be top of mind for commercial and public sector organizations. And for good reason: last year cybersecurity attacks grew 38%, with each data breach costing organizations an average of $4.35M. The sheer scale of modern attacks and the sophistication of motivated adversaries are something that legacy productivity solutions can’t keep pace with. There is a better way — a cloud-native architecture rooted in zero-trust principles and augmented with AI-powered threat defenses. This is how we architected Google Workspace, resulting in real-world benefits for our customers:
- 0 known exploited vulnerabilities vs. 40+ in a legacy productivity suite (The U.S. Cybersecurity and Infrastructure Security Agency, 11/2021 - 8/2023)
- 41% fewer security incidents on average than other email solutions (At-Bay, Ranking Email Security Solutions, 2/2023)
- Up to 50% savings on cyber security insurance premiums (At-Bay, Ranking Email Security Solutions, 2/2023)
In security, the job is never done, which is why we’re unveiling new zero trust, digital sovereignty, and threat defense controls powered by Google AI to help organizations keep their data safe.
Enable safer work from anywhere with AI-powered zero trust controls
The zero trust security model has become an essential part of reducing security risks for a distributed workforce. Workspace provides built-in controls, such as data loss prevention (DLP) and context-aware access (CAA), to help organizations accelerate their zero trust adoption and meet industry frameworks, such as CISA’s Zero Trust Maturity Model.
Roche is one of many customers that has been using zero trust capabilities in Workspace to enable safer work: “Our organization has been striving to break away from VPN and office network connections for years,” said Tim Ehrhart, Domain Lead, Information Security, Roche. “Context-Aware Access (CAA) has helped us manage our risks by not making access a binary choice, but allowing for more flexibility in access policies and allowing them to be applied to the right people, applications, and data. Since using CAA, we've been able to allow our users to use more of Google Workspace for a broader set of scenarios with more confidence in the safety of that work.”
Today, we are introducing new capabilities to provide IT and security teams with more granular controls over data use and access, including:
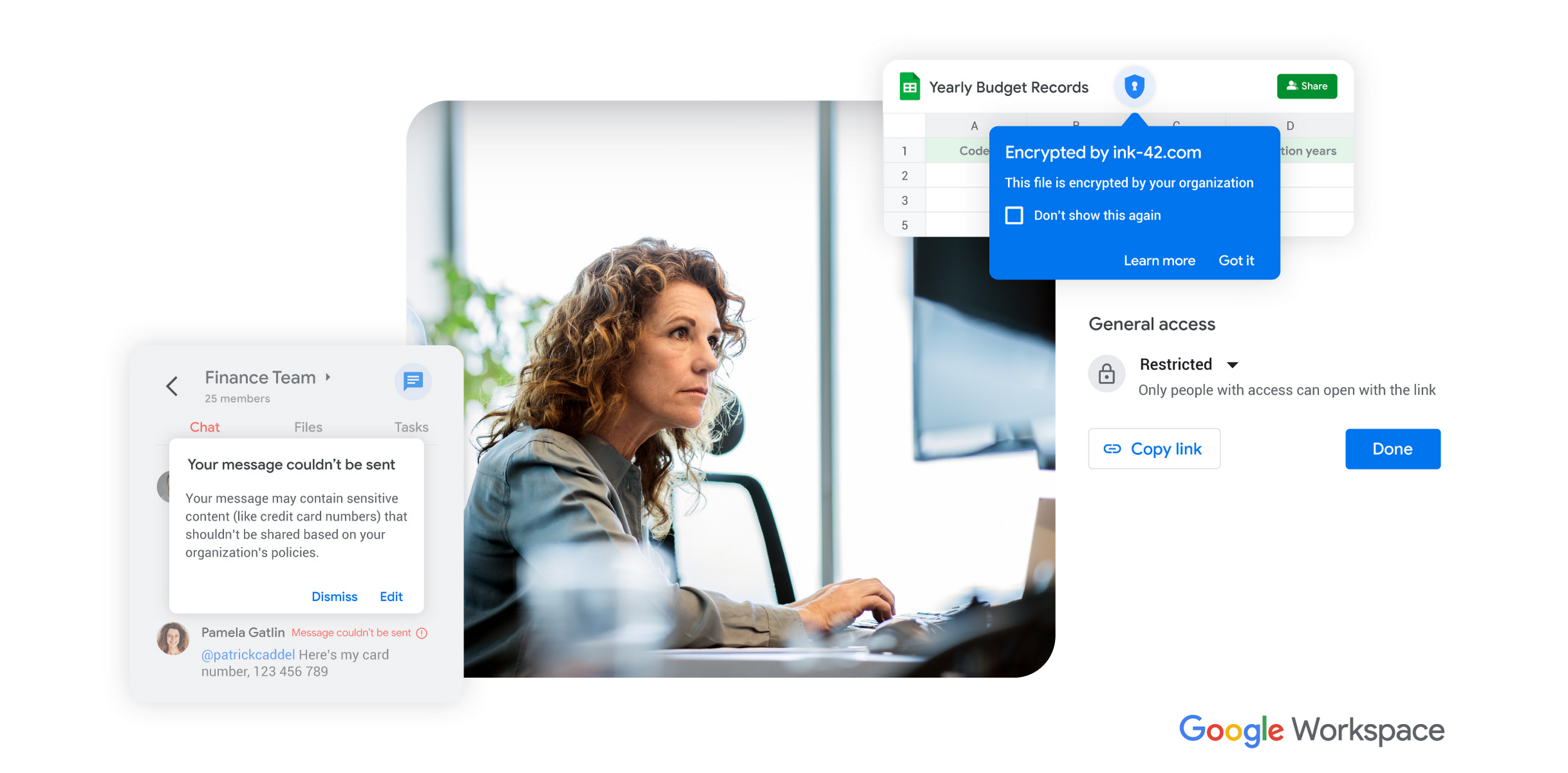
- Leveraging Google AI to automatically and continuously classify and label data in Google Drive to help ensure data is appropriately shared and protected from exfiltration: Administrators can now use confidentiality-preserving AI models, customized uniquely for their organization, to automatically classify and label new and existing files in Drive. Data protection controls, such as DLP or CAA, can then be applied based on the security policy. This is now available in preview.


Enforcing context-aware DLP controls in Drive: Workspace admins can set criteria, such as device location or security status, that must be met in order for a user to be able to share sensitive content in Drive. This new capability provides more granular controls to help prevent unintended data loss and will be available later this year in preview.
Extending enhanced DLP controls to Gmail: Already available in Google Chat, Drive, and Chrome to help security teams control sharing sensitive information inside and outside the organization, enhanced DLP controls are coming to Gmail and will be available in preview later this year.
Go beyond data residency with digital sovereignty controls
Enterprise and public sector organizations recognize the importance of digital sovereignty, but often settle for data residency without fully understanding its limitations. Workspace can provide a step change in attestable digital sovereignty with secure-by-default infrastructure, technical data access controls, and industry certifications all in a single cloud instance.
PwC UK piloted Sovereign Controls in Workspace to help meet demanding regulatory requirements: "PwC UK participated in the CSE Gmail pilot and I observed first hand that Google understands the importance of technical data boundaries, not only for PwC and our requirements, but for that of our clients,” said Shaun Bookham, UK Operations and Technology Director, PwC UK. “Through influencing the development of these CSE and Access Management capabilities, I have confidence that Google will continue to adapt to rapidly evolving regulatory requirements, enabling us to transform the way we work whilst remaining at the forefront of sovereignty and compliance."
Today, we are introducing new capabilities to provide organizations with enhanced controls over their data that help with:
Preventing third-party access to sensitive data: Through the ownership of the encryption keys, client-side encryption (CSE) helps organizations add an additional layer of data protection and prevent third-party access from external entities such as Google or foreign governments. Today, we're introducing a number of CSE enhancements, including the support of mobile apps in Google Calendar, Gmail, and Meet (generally available), the ability to set CSE as default for select organizational units (available in preview later this year), guest access support in Meet (available in preview later this year), comments support in Docs (available in preview later this year), and the ability for users to view, edit, or convert Microsoft Excel files (available in preview).
Selecting the location of your encryption keys: Through strategic partnerships with a global security provider Thales, Stormshield, and Flowcrypt, we're enabling CSE customers to store their encryption keys with their trusted partner in the country of their choice to simplify set up and support local regulatory compliance.

Choosing where data is stored and processed: Today, organizations can choose the storage location of their data at rest. Available in preview later this year, organizations will be able to choose where their covered data is processed (EU or US). Organizations also have the option to store a copy of their Workspace data in a country of their choice.
Enforcing regional support personnel access: Today, customers worldwide can use Access Approvals to control Google support access for troubleshooting purposes, and can monitor Google actions with Access Transparency. Additionally, customers can use Access Management to limit approved access to US-based support. Available in preview later this year, customers will also be able to limit access to EU-based support.
Prevent cyber threats before they emerge
Social engineering attacks, such as phishing, are one of the most common entry points for data breaches. Threat defense controls in Workspace help customers prevent, detect, and respond to social engineering and other identity-based attacks before they emerge. Today, we’re introducing additional capabilities to help security teams defend against account takeovers, including:
- Making 2-Step verification (2SV) mandatory for select enterprise administrators: Compromised administrator accounts can have an outsized impact, and 2SV can result in a 50% decrease in accounts being compromised. Starting later this year, in a phased approach, select administrator accounts of our resellers and largest enterprise customers will be required to add 2SV to their accounts to strengthen their security.
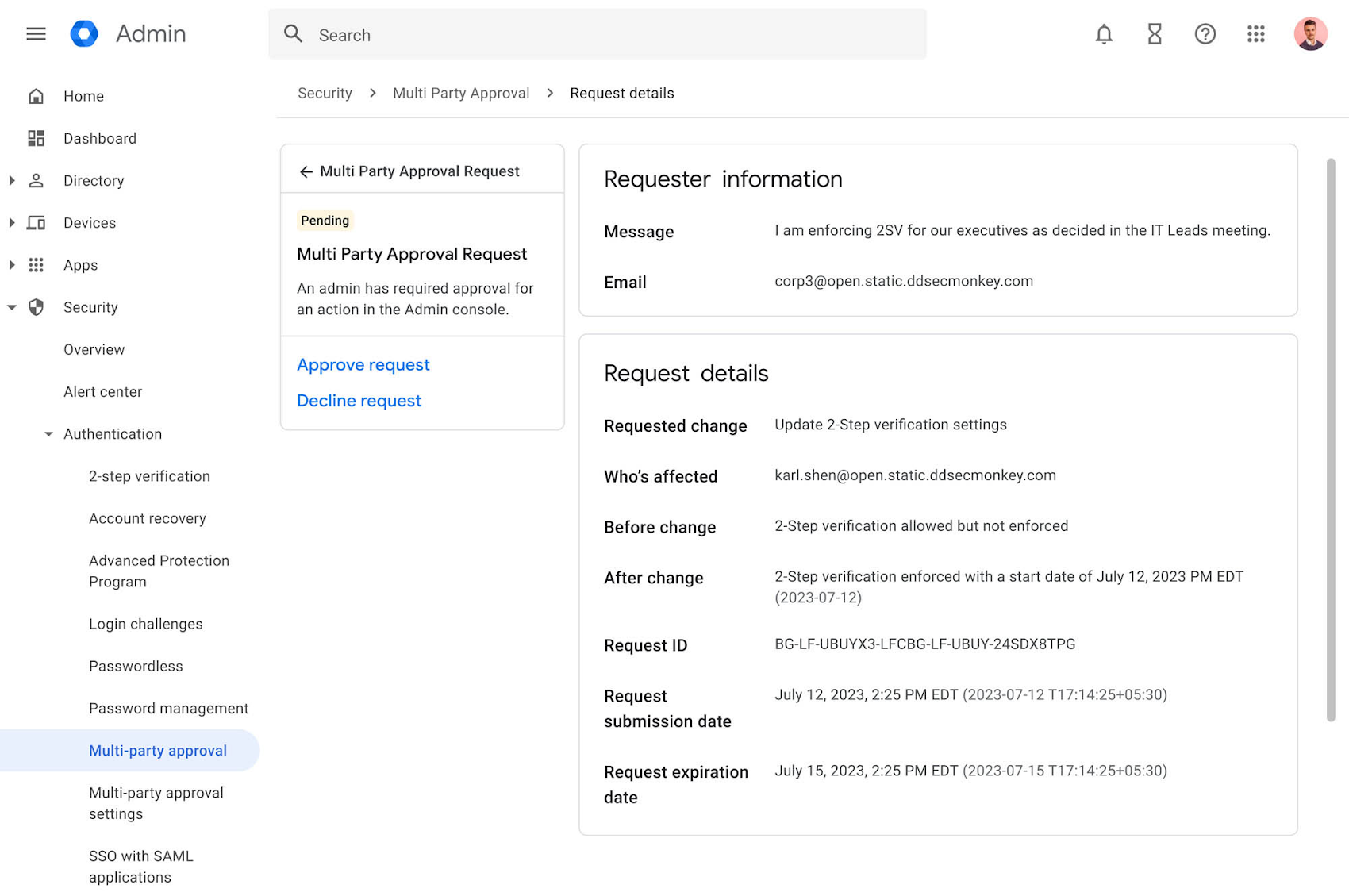
- Requiring multi-party approval for sensitive administrator actions: Workspace administrators can require additional approval by another administrator to complete a sensitive action, such as changing 2SV settings for a user, to provide an extra layer of defense against malicious actions. This will be available in preview later this year.

Protecting additional sensitive actions in Gmail: We are extending Google’s AI-powered defenses to provide automated protection for additional sensitive actions in Gmail, such as email filtering or forwarding. This protection is available in preview.
Exporting logs to Chronicle in just a few clicks: Workspace administrators can now export Workspace logs into Chronicle to identify anomalies and help improve their response time to threats. This integration is available in preview.
Getting started
We are constantly at work to help our customers — from small businesses and large enterprises to schools and governments — strengthen their security and compliance posture and keep their data safe. To learn more, get a no-cost trial, check out our technical documentation, attend our upcoming sessions at Next ‘23, and sign up for early access to try new capabilities.
For information on securing AI systems, check out Google SAIF, a conceptual framework to help practitioners collaboratively secure AI technology as it continues to grow.