Improve your security posture with expanded Custom Org Policy
Akshay Datar
Product Manager, Google Cloud
When it comes to securing cloud resources, one of the most important tools for administrators is the ability to set guardrails for resource configurations that can be applied consistently across the environment, centrally managed, and safely rolled out.
Google Cloud's custom Organization Policy is a powerful tool that can help organizations safeguard cloud resources. Administrators can use custom organization policies to set granular resource configurations in order to enhance security posture, address regulatory requirements, and increase operational efficiencies, all without impacting development velocity.
Today, we are excited to announce that custom Org Policy is now adding support for more than 30 additional Google Cloud services.
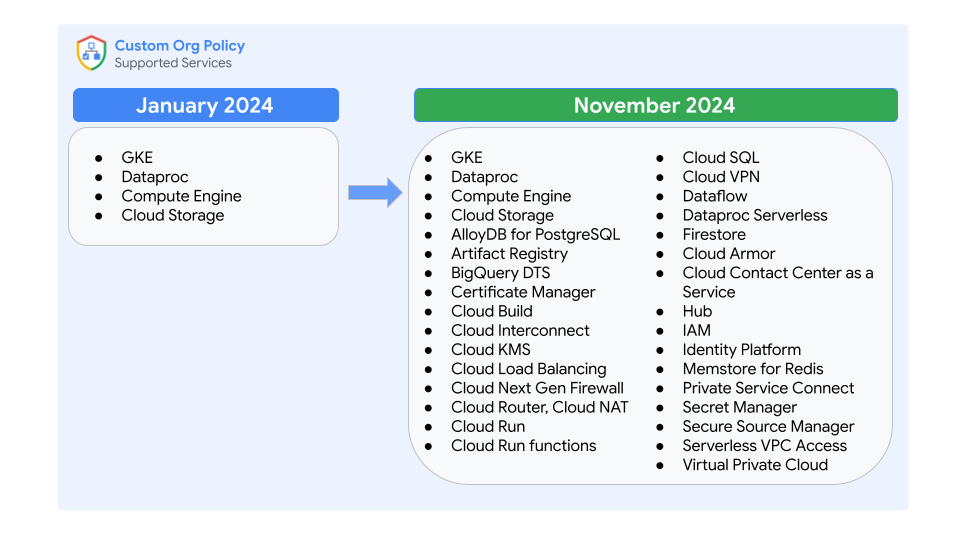

This expansion unlocks many new use cases and expands the scope of cloud governance.
Securely scale access control management with custom Org Policies
As cloud deployments grow, security teams can struggle to manage all the new access requests from across their organization. To scale effectively, organizations must establish an operational model for access control that balances developer empowerment with security and compliance.
The integration of custom Organization Policy with IAM policies can enable restrictions on IAM Policies at any desired level of the Google Cloud resource hierarchy (organization, folder, or project) and delegate subsequent IAM Policy management to developers, knowing that all policy changes in these environments will not violate the restrictions that have been put in place.
Using this capability, administrators can enforce conditional restrictions such as, “Only allow specific roles to be granted against resources in this project” or “Only allow specific members to be granted access via policies against this folder” or “Deny “allUsers” grant for any resources in this organization.”
These more coarse-grained restrictive policies let you explicitly prohibit access to certain resources regardless of existing Allow rules. Here are few custom Org Policy examples governing IAM policies:
Restrict specific roles to be granted against resources in this project
Restrict “allUsers” grant for any resources in this organization
In addition, custom Organization Policy extends Domain Restricted Sharing by allowing for principal level granularity in the policy configuration. For example, you can set policies to allow all users of your organization as well as specific partner identities, service accounts, or service agents. This increased flexibility can help administrators more effectively manage policies without adding identities.
Only allow members from either specific organizations or specific members
Establish strong data governance for Cloud SQL
Data platform teams often want to ensure that each application team is adhering to security best practices when using various SQL products. Custom Org Policy support for Cloud SQL can help you establish strong guardrails around SQL resources and address data governance requirements. Here are some common use cases illustrating the power of custom org policy together with Cloud SQL:
Ensure that each application team is using the latest database version for SQL instances
Ensure that all the database instances require complex passwords requirements
Enhancing security posture with custom Org Policy at Yahoo
Yahoo serves hundreds of millions of people globally, and cloud security teams at Yahoo actively use predefined Org Policy controls to meet their security and compliance requirements. However, each Yahoo property has different needs and infrastructure, so Yahoo’s security team needed the flexibility to build custom guardrails.
Since March 2023, Yahoo’s platform engineers and company's information security team, The Paranoids, have worked with Google Cloud to adopt custom Org Policies for Kubernetes and other cloud infrastructure.
“We’ve implemented 24 custom Org Policies to exceed industry-standard baselines, such as required secure boot for GKE nodes. In addition to taking advantage of the increased flexibility that custom Org Policy offers, these policies helped us scale security controls safely. Our engineers across the company didn’t have to actively worry about security requirements anymore, as these guardrails automatically took care of adhering to many of Yahoo’s Information Security policies. Our team is further enhancing these policies and planning to now cover Cloud SQL, CloudRun, and IAM. As new products and use cases roll out, Yahoo’s platforms team plans to lean into further adoption of custom organization policies. In short, this helped us to enhance our security posture at scale,” said Alex Verkhovtsev, senior software development engineer, Yahoo.
Get started with custom Org Policy
As Google Cloud continues to expand services that support custom Org Policy, you can expect greater control, flexibility, and efficiency to manage cloud resources.
To get started with custom Org Policies, check out our user guide and overview video. You can find more information on supported services by following the links here as well as a growing repository of ready to use samples here.


