Announcing general availability of Custom Org Policy to help tailor resource guardrails with confidence
Akshay Datar
Product Manager, Google Cloud
Alok Jain
Group Product Manager, Google Cloud Security
Google Cloud’s Organization Policy Service can help you control resource configurations and establish guardrails in your cloud environment. And with custom organization policies, a powerful new extension to Organization (Org) Policy Service, you can now create granular resource policies to help address your cloud governance requirements. This new capability, now generally available, also comes with a dry-run mode that lets you safely roll out new policies without impacting your production environment.
Org Policy Service can help you establish security guardrails that only allow compliant resource configurations in your cloud organization. With Org Policy Service, you could select from the library of more than 100 predefined policies based on industry best practices. Custom org policies adds the ability to create and manage your own security and compliance policies that can meet and address changes to your organization's business requirements and policies.
How do Custom Org Policies work?
Custom org policies are customizable security guardrails for resource configurations that can be applied across your environment at any desired level such as at the organization, folder, or project. Security admins can quickly craft custom constraints tailored to their specific use case through Console, CLI, or API in a matter of minutes.
Custom org policies use the intuitive Common Expression Language (CEL) to specify conditions that must be met to allow resource creation or mutation, making it easy to enhance your security posture and enforce critical policies required for your environment.
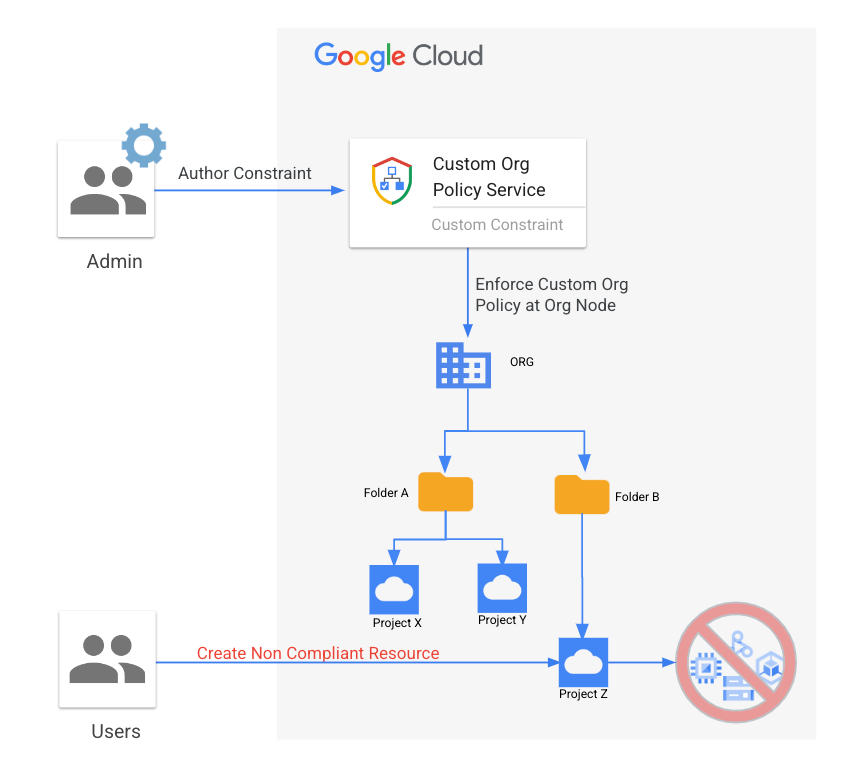

Figure: Custom org policies workflow overview
What are the key benefits of Custom Org Policies?
Custom org policies can enable organizations to centralize control and help security administrators set guardrails for their cloud environment. These guardrails allow developers to build applications within admin-defined boundaries. Custom org policies can help you gain visibility and enforce policies across all your cloud resources, making it easier for you to manage and improve your security posture.
Custom org policies also can help you to address compliance requirements based on your regulatory environment. You can craft custom policies that can help you meet regulatory obligations such as HIPAA, PCI-DSS, and GDPR, and your own organization’s compliance standards. Custom org policies can assist with creating and managing policies based on your organization's evolving security needs, and help you to mitigate risks. You can introduce proactive security and compliance measures that minimizes the risk of incidents and improves operational efficiencies.
“Staying true to our mission of safeguarding Snap’s production infrastructure, we are continuously evolving and looking for new opportunities to establish access and policy guardrails. We’re excited to see custom organization policies go GA as we plan to adopt this product to help us enforce, amongst other things, GKE constraints associated with CIS benchmarks,” said Babak Bahamin, production security manager, Snap.
Here’s a closer look at few use cases and the benefits of custom org policies:
Use case: Enforce GKE Auto upgrade with custom org policies
To ensure that all the nodes in your GKE cluster have the latest security fixes and reduce overhead to manually update nodes, you can mandate that all nodepools in your organization have auto-upgrade turned on. You can easily set up custom org policies using a custom constraint that allows you to resource configurations based on certain parameters.
In this scenario, an admin can set up a custom constraint with a condition like resource.management.autoUpgrade == true and enforce it across your resource hierarchy (Org, Folder, Project) as needed. Only nodepools create and update operations that enable autoUpgrade are permitted, ensuring compliance with the mandate. Custom org policies are not retroactive, so these policies are not applied on existing resources. This can help ensure that your existing workflows in your production environment are not disrupted.
Use case: Manage operations by restricting virtual machines
To limit the usage of specific virtual machines across your projects for cost or compliance reasons, a custom org policy can be deployed that mandates to only allow creation of specific VM types. For example, to restrict all VMs created to only use N2D machine types, you can set the condition as : resource.machineType.contains('/machineTypes/n2d'). This policy can be enforced centrally, and exceptions can be granted for approved use cases, allowing you to carefully manage costs and budget your cloud expenditure.
In addition to the use cases highlighted here, you can enforce many other security controls like restricting VMs to hardened images, blocking bad network routes for traffic or restricting permitted regions for resource creation.
How to deploy Custom Org Policies safely in your environment
Because it’s important to minimize disruption when introducing changes to custom org policies, we are pleased to also announce the general availability of dry-run for custom org policies. Dry-run allows you to deploy custom org policies in audit-only mode and compare Live versus dry-run outcomes of new resource actions without putting production workloads at risk.
Dry-run mode can help you quickly understand how a policy change would behave with your workloads before the change is enforced. Another component of our safe rollout strategy is Policy Simulator, currently in preview. Using Policy Simulation, you can preview existing resources that would be in violation of a new custom org policy when it is enforced. You now have a snapshot view of your resources compliant with custom org policies.
Together, these tools can give you a more holistic view of the impact of deploying a new custom org policy and provide an opportunity to make any tweaks before enforcing the policy. Once you confirm that the policy is working as intended, turning it to a live policy is as easy as flipping a switch.

Next steps
Please check out our Getting Started guide to learn how to define, deploy, and manage your custom policies. You can watch a demo of custom org policy in preview that we showcased at Google Cloud Next ’23. Whether you're a security architect, a compliance officer, or a developer, custom org policies can empower you to take control of your cloud resources and can help build a more secure and compliant environment.

