How Virgin Media O2 uses Privileged Access Manager to achieve principle of least privilege
Henry Tze
Head of DevOps, Virgin Media O2
Editor’s note: Virgin Media O2 provides internet and communications services to more than 48.5 million subscribers, and teams are also responsible for supporting more than 16,000 employees. Virgin Media O2 is committed to empowering customers with outstanding customer-centered products and essential connectivity — all powered behind the scenes by Google Cloud, the backbone of the company’s daily operations. In this guest blog, Henry Tze shares his DevOps insights.
From virtual machines to applications to storage assets, at Virgin Media O2 we have a huge cloud footprint, all hosted in Google Cloud. Google Cloud enables us to process vast amounts of data at scale and deliver cutting-edge customer services, using an array of cloud-first services, including BigQuery, Google Kubernetes Engine, and Compute Engine.
All told, we’re managing more than 11 million resources, including nearly 1 million BigQuery tables. Ensuring adherence to stringent security and compliance requirements is central to our mission — and no small feat.
Reducing identity sprawl to safeguard our cloud environment
We have a large, international team, and even though all of our employees are vital to our operations, they don’t all need access to the same information. To protect both our internal and customer data, we have to carefully configure our Identity and Access Management (IAM) infrastructure to ensure we’re compliant with the U.K.’s stringent data management regulations.
Part of our security journey has involved both our migration to the cloud and fully embracing Infrastructure as Code (IaC). We now refer to our infrastructure as “everything as code,” using GitOps to centralize our source of truth. Doing so helps us create a clear audit trail and version history record.
This centralization has helped us align developers, engineers, and compliance teams toward the same goals. Unfortunately, ensuring that these teams have access to the tools they need to accomplish those goals is complicated.
Since taking a GitOps approach means we’re focusing more on what we want our infrastructure to look like than how we get there, we have less insight into the specific tools or paths our teams need to take to get the job done. However, this led to permission sprawl as users gained access to applications or datasets for a specific purpose and retained that access after they were finished with their work.
As that sprawl expanded, it was difficult to track who had access to what which ultimately posed a challenge to our compliance and security goals. Balancing ease of access with security compliance is a complicated challenge, but we needed to find a simple solution.
With Google Cloud, we already had access to IAM conditions, which helped us customize time-based access controls. However, for us to scale we needed to automate provisioning and permissions management based on roles and responsibilities, and now we can with Google Cloud’s built-in Privileged Access Manager (PAM).
Improving compliance by centralizing and automating identity controls with PAM
Using PAM, our team can ensure we adhere to least-privilege standards to protect our assets but still automate access for appropriate users, all without needing an external agent or additional software tool. By providing just-in-time (JIT), time-bound, and approval-based access, our admin team can rest easy knowing that the only users who are actively using an application or other asset have access.
Our administrators can review access permissions in a single place and still customize permission controls from asset to asset. For example, developers may have predefined, role-based permissions for their day-to-day applications. However, if they’re assigned an ad hoc data project, they’ll need to request temporary access, and the approver is notified immediately.
This extra level of caution helps us mitigate risk by reducing the number of users who have blanket permissions and prevents access sprawl as we grow. Our compliance auditors are also satisfied because we have clear access permission histories which simplifies and centralizes the audit process.
Using Google Cloud’s PAM we created a self-service model at Virgin Media O2, that has helped us streamline access, boost productivity, and address compliance. Here are core tenets of our model:
Delegated approvals: Our Cloud Platform Security Team can delegate approval authority to Department and Product Administrators, which can enable them to manage privileges for their areas of expertise.
Built-in guardrails: Our Cloud Platform Security Team relies on predefined templates with embedded security controls, which can ensure that privileged access is granted securely, even with delegated approvals.
Self-sufficient teams: Our Department and Product administrators gain the autonomy to manage entitlements independently, so they can make changes swiftly and without the need to involve the security team.
On-demand access: Our customers can request permissions at any time, and adapt to evolving work requirements.
Compliance audits: Our Compliance Auditors have complete visibility into every action related to privileged access, from entitlement creation and grant requests to activation and termination.
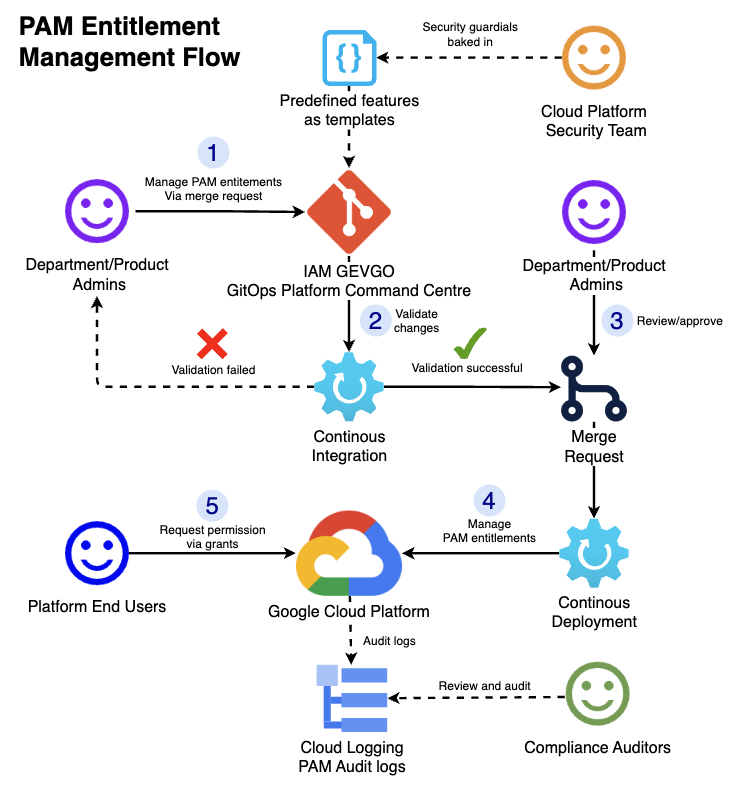

A sample workflow of access management with PAM at Virgin Media O2.
Using PAM to drive success
Since adopting PAM, we’ve successfully reduced longstanding IAM permissions that created potential vulnerabilities in our cloud and simplified access management across the organization. Most importantly, PAM has helped us achieve and maintain compliance with the stringent requirements imposed on our regulated organization.
We’ve also built a more sustainable and scalable access system that will grow alongside Virgin Media O2 as we continue to supercharge more customers across the UK.



