Zero Trust and BeyondCorp Google Cloud

Priyanka Vergadia
Staff Developer Advocate, Google Cloud
Zero Trust and BeyondCorp Google Cloud
Let’s say in 2021, you are organizing an in-person event. You need to make sure it’s COVID-safe for everyone attending, so you set up a system in which every person is tested and only allowed in if the results are negative. You had every invitee fill out a form where they shared their negative test results, but you don’t implicitly trust them because they might have been somewhere else in the meantime or come into contact with another infected person. So, you have them take a rapid test on-site before they can join.
As with this real-world scenario, in the online world implicit trust in any component of a system can create significant security risks. To mitigate these risks, the zero trust security model mandates that trust be established via multiple mechanisms and continuously verified. This approach can be applied to end-user access, the end-to-end process of running production systems and protecting workloads on your cloud infrastructure, and other processes and domains.
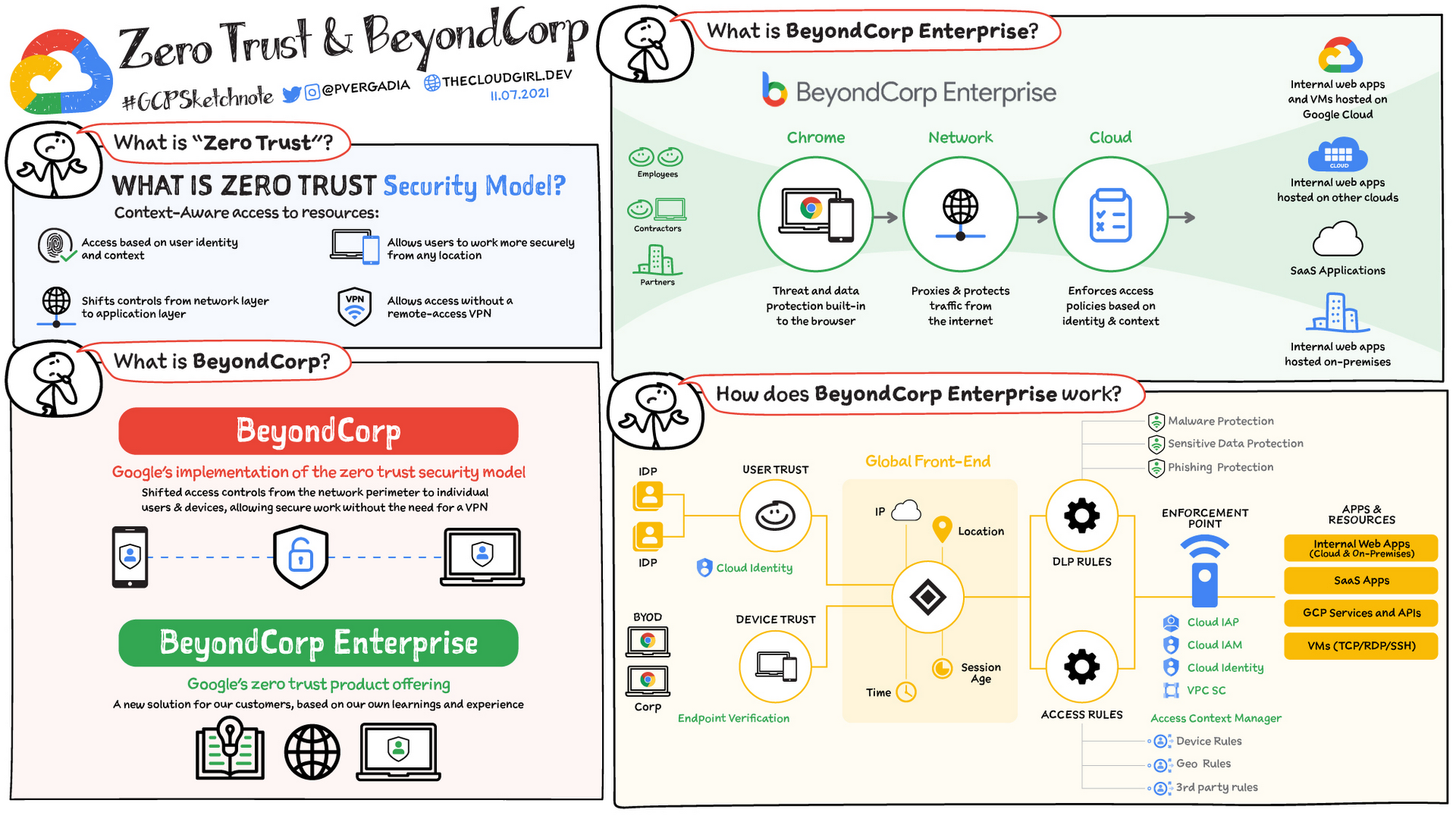

What is BeyondCorp?
In 2011, Google came up with a new approach for enterprise access management: the BeyondCorp implementation of the zero trust security model. It started as an internal Google initiative to enable every employee to work from untrusted networks without the use of a VPN. BeyondCorp shifts access decisions from the network perimeter to individual users and devices, thereby enabling employees to work more securely from any location and transforming the way they work.

What is BeyondCorp Enterprise?
BeyondCorp Enterprise is Google Cloud’s commercial implementation of a zero trust access model. With this model, no one can access your resources unless they meet all the rules and conditions codified in per-resource access policies. Basically, we want to help your workforce access your applications and resources in a secure, yet simple way. How do we do that?

Employees use Chrome (or a Chromium-based browser) with built in threat and data protection as they would normally to access applications and resources. The Google network protects and proxies traffic to resources and enables organizations to help enforce context-aware policies (using factors such as identity, device information, location, time of day, the network the employee is using, and so on) to authorize access.
BeyondCorp Enterprise provide two essential capabilities:
Richer access controls help protect access to systems (applications, virtual machines, APIs, and so on) by using the context of an end-user's request to ensure each request is authenticated, authorized, and as safe as possible.
Threat and data protection brings security to your enterprise devices by working to protect users from exfiltration risks such as copy and paste, extending data loss prevention (DLP) into the browser, and helping to prevent malware from getting onto enterprise-managed devices.
How does BeyondCorp Enterprise work?


to only employees who are using encrypted devices. Coupled with IAM Conditions, you could increase the granularity of this access level by allowing access only between 9:00 AM and 5:00 PM.
Securing resources with IAP
IAP lets you apply IAM Conditions on Google Cloud resources and helps establish a central authorization layer for your Google Cloud resources accessed by HTTPS and SSH/TCP traffic. With IAP, you can establish a resource-level access control model instead of relying on network-level firewalls. Once secured, your resources are accessible to your employees, from their devices, on your network, as long as that employee, network, and device all meet the access rules and conditions.
Applying IAM Conditions
IAM Conditions enable you to define and enforce conditional, attribute-based access control for Google Cloud resources. With IAM Conditions, you can choose to grant permissions to principals only if configured conditions are met. IAM Conditions can limit access with a variety of attributes, including access levels. Conditions are specified in the IAP role bindings of a resource's IAM policy.
BeyondProd
Since a user's credentials can be captured by bad actors, a security model that focuses on the perimeter is inadequate. Likewise, any software that interacts with the larger world needs protection on many levels. That’s why it makes sense to apply a zero trust approach to how you operate your production environment, encompassing the way software is conceived, produced, managed, and interacts with other software. Google published a whitepaper on our BeyondProd model to explain how we protect our cloud-native architecture and to help organizations learn to apply zero trust security principles to this domain.
That was an overview of the zero trust security model and its commercial implementation in BeyondCorp Enterprise. For a more in-depth look into BeyondCorp Enterprise check out the documentation.

For more #GCPSketchnote, follow the GitHub repo. For similar cloud content follow me on Twitter @pvergadia and keep an eye out on thecloudgirl.dev

