This writing contains many points that are important information for fellow friends and the mentioned public services to be aware of being abused by this malware infection session. So I wrote this as fast as possible and leaving payload binary analysis and exploit analysis in a rain check. To anyone who can help to contact the related abuse, is very highly appreciated.
Infection Source:
First of all. The source of infection is the malware infection code/scripts that was implemented in the below IP and domain,
located in OVH network, in France, I really hope to have help from France friends to clean this IP from any malware infector toolkits installed:

Secondly, the infector, is starting from Japan's IP under domain: shortening .biz

This needs to be cleaned up too, yet I think there are more infectors exist..
The background
It started when checking a suspicious URL, accessed it in the browser as per below:
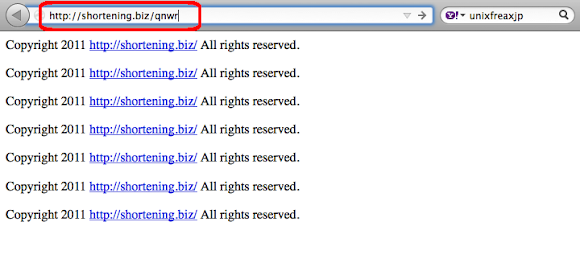
I regenerated with the separate scheme to record the below log (for the source of infection details purpose), just to make sure that we had everything in our hands:
--2014-02-24 02:40:02-- h00p://shortening .biz/qnwr Resolving shortening.biz... 59.106.171.55 Caching shortening.biz => 59.106.171.55 Connecting to shortening.biz|59.106.171.55|:80... connected. : GET /qnwr HTTP/1.1 Host: shortening.biz HTTP request sent, awaiting response... : HTTP/1.1 301 Moved Permanently Date: Sun, 23 Feb 2014 17:40:03 GMT Server: Apache/1.3.42 (Unix) mod_ssl/2.8.31 OpenSSL/0.9.8e Location: http://shortening.biz/qnwr/ Keep-Alive: timeout=5, max=19 Connection: Keep-Alive Transfer-Encoding: chunked Content-Type: text/html; charset=iso-8859-1 : 301 Moved Permanently Registered socket 4 for persistent reuse. Location: http://shortening.biz/qnwr/ [following] Skipping 302 bytes of body: [ 301 Moved Permanently Moved Permanently The document has moved (A HREF="h00p://shortening .biz/qnwr/")here(/A) Apache/1.3.42 Server at shortening.biz Port 80 ] done. : --2014-02-24 02:40:03-- h00p://shortening .biz/qnwr/ GET /qnwr/ HTTP/1.1 Host: shortening.biz : HTTP/1.1 200 OK Date: Sun, 23 Feb 2014 17:40:03 GMT Server: Apache/1.3.42 (Unix) mod_ssl/2.8.31 OpenSSL/0.9.8e Last-Modified: Thu, 23 Jan 2014 14:54:18 GMT ETag: "1135-52e12d1a" Accept-Ranges: bytes Content-Length: 4405 Keep-Alive: timeout=5, max=19 Connection: Keep-Alive Content-Type: text/html : 200 OK Length: 4405 (4.3K) [text/html] Saving to: ‘sample.mmd’ 100%[=======================================================>] 4,405 --.-K/s in 0.009s 2014-02-24 02:40:03 (459 KB/s) - ‘sample.mmd’ saved [4405/4405]Back to the browser, in the short while the browser's address bar flickering to the redirection URL as per below:

And this act is confirmed by the series of the html tag meta refresh code grepped below:

What happened next? I was being forwarded into a page with video of "a lady in the bed" as per captured below:

I just about to praise on how fortunate I am.. but the video soon got stopped and the warning message came up with popping the download of the Flash Player Setup.. as per shown below:

The Path to Payload
Back to the shell, I simulated the download page for evidence:
And that was giving me the below script actually:

And now we know why I got that redirection, the dropboxusercontent.com (the very bottom link) is serving the infection landing page and I was redirected into it. Will explain this later on. And there are other conditions for another redirection, for the mobile access and Opera browser in the GOO.GL short URL. Anyway if we extract those Short URL for Mobile and Opera browser we'll find the better image:

(I will have to leave other friends to check those two links deeper..)
The further research in the blacklisted URL found the below Amazon AWS abused account (sorted by history) by the same threat:

And this is the malware file downloaded if you are matching to the desired condition:

Now this payload is well detected by AV industry as per shown in VirusTotal result here-->>[link]
If you run the payload you will get the query and response in HTTP as follows:

And this payload is downloading a "config" with the info on hash and URL of another malware, as per shown here:

Here's that "guncel.exe" malware download session in my shell..a simple wget will do..This could be the updates or sort of.

This is the VirusTotal report of the "guncel.exe", is the same file as original payload, it is also as an evidence explaining that the origin of the payload is wjetphp.com (46.105.55.251)-->>[link], the detection rates as the VBA basis Trojan Downloader is not so bad after all, good work.
Below is interesting trace of what this malware did in the memory:

This is just some traces of VBA calls used..(during the creation of registry key)

Quick analysis that might help fellow researchers and infected victims:

The payload will download the background.js JavaScript w/URL planted in the binary, as per traffic below:

Which is having the script as I pasted here-->>[link]
↑You can see clearly the malicious traffic redirection scheme and access URL to the landing page (origin of the infection), in that script..
The next traffic will explain how this background.js is called, the file manifest.json was downloaded, it contains the script to show how background.js is executed by setting several security privileges for the execution of the script itself..

You can see the effort to fake "Google Shockwave Player" (any such product??) upon the execution of background.js above? Things are starting to make much sense on why so many Google related "images" are used here.
PS: I will add some more reversing notes later on, but shall we move on a bit..too little time..for there are more important parts to cover..
What happened if we simulate the landing page access in shell is something like this:
GET /s/pwuh8wdutwot4dg/rezillik.html HTTP/1.1 Host: dl.dropboxusercontent.com : HTTP/1.1 200 OK accept-ranges: bytes cache-control: max-age=0 Content-Type: text/html; charset=utf-8 Date: Sun, 23 Feb 2014 21:01:55 GMT etag: 2n pragma: public Server: nginx x-dropbox-request-id: ecd60af812734360278c876a87176a00 X-RequestId: 6f612d52e7e3c0e526aa4b355328e047 x-server-response-time: 202 Content-Length: 6841 Connection: keep-alive : ---response end--- 200 OK Registered socket 4 for persistent reuse. Length: 6841 (6.7K) [text/html] Saving to: ‘sample4.mmd’How I got the payload being downloaded then?? Let's see the code inside the page. Well..It seems like I got hit by the timer function stated by this code:

The Google short URL is again being used to hide the real malware payload URL which is served in the Google Code SVN download!!

The download log can be seen in the follow up section..
Well..the bad guy behind this is really trying hard to convince victim about the Google kind of application is installed :-)
Some reversing & investigation notes
I used recent sample in an abused Google Code SVN here:

The sample is in VT here-->[link]
Straight to the point: A reversing effort showing the CNC masked in binary strings:

Maybe we'll need these later, just in case, noted:
"key": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDQcByy+eN9jzazWF/DPn7N "key": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCtl3tO0osjuzRsf6xtD2SKxPlTfuoy7AWoObysitBPvH5fE1NaAA1/2JkPWkVDhdLBWLaIBPYeXbzlHp3y4Vv/4XG+aN5qFE3z+1RU/NqkzVYHtIpVScf3DjTYtKVL66mzVGijSoAIwbFCC3LpGdaoe6Q1rSRD "key": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDoVDPGX6fvKPVVgc+gnkYlGqHuuapgFDyKhsy4z7UzRLO/95zXPv8h8e5EacqbAQJLUbP6DER "key": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDNuYLEQ1QPMcc5HfWI/9jiEf6FdJWqEtgR "key": "MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDqOhnwk4+HXVfGyaNsAQdU/js1Na56diW08oF
Next. Following the trails of that CnC URL, to find the junk used:
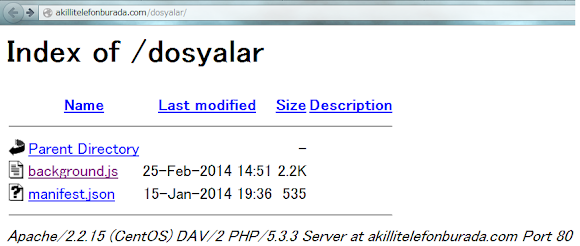
Now we can see the code clearly, instead of the PCAP data :-D
See the dates well, the crook was recently modifying the background.js malicious script.
It has the background.js and manifest.json code snipped below:

As per explained way up above, the JSON is used for execution of background.js. We didn't have a a chance to disclose background.js clearly before, so this is it, a fresh one. First, the beautified full code of the bakcground.js is:

If you see what I see, the attacker is aiming Google Chrome browser, by abusing its API (chrome.tabs) to interact with the browser's tab system. You can use this API to create, modify, and rearrange tabs in the browser. Anyway, what he did is on "devtools://" index/tab, he programmed to execute remote script via chrome.tabs.executeScript command to www.saatlikrapor .com/ext/s.php, which this was BAD (gone now-->link and link) in . Either this crook loves Google so much or hates Google that much.. since now we know he is aiming Google chrome browser's end user too.
PS: The saatlikrapor.com domain is hidden behind cloudfare:
;; QUESTION SECTION: ;www.saatlikrapor.com. IN A ;; ANSWER SECTION: www.saatlikrapor.com. 300 IN CNAME saatlikrapor.com. saatlikrapor.com. 300 IN A 141.101.116.106 saatlikrapor.com. 300 IN A 141.101.117.106 ;; AUTHORITY SECTION: saatlikrapor.com. 3600 IN NS "jeff.ns.cloudflare.com." saatlikrapor.com. 3600 IN NS "lisa.ns.cloudflare.com." ;; ADDITIONAL SECTION: jeff.ns.cloudflare.com. 384 IN A 173.245.59.124 lisa.ns.cloudflare.com. 371 IN A 173.245.58.131This is the domain information, a shiny brand new one:
Domain Name: SAATLIKRAPOR.COM Registrar: DOMAINSITE, INC. Whois Server: whois.domainsite.com Referral URL: http://www.domainsite.com Name Server: JEFF.NS.CLOUDFLARE.COM Name Server: LISA.NS.CLOUDFLARE.COM Status: clientTransferProhibited Updated Date: 25-feb-2014 Creation Date: 25-feb-2014 Expiration Date: 25-feb-2015 Registrar: DomainSite, Inc. Registrar IANA ID: 466 Registrar Abuse Contact Email: [email protected] Registrar Abuse Contact Phone: +1.17202492374 Resellser: Domain Status: addPeriod Domain Status: clientTransferProhibited Registrant Name: Whois Agent Registrant Organization: Whois Privacy Protection Service, Inc.And how about the CnC used? akillitelefonburada.com ; SAME pattern! :-) behind cloudflare..
;; QUESTION SECTION: ;akillitelefonburada.com. IN A ;; ANSWER SECTION: akillitelefonburada.com. 300 IN A 108.162.197.162 akillitelefonburada.com. 300 IN A 108.162.196.162 ;; AUTHORITY SECTION: akillitelefonburada.com. 3600 IN NS "jeff.ns.cloudflare.com." akillitelefonburada.com. 3600 IN NS "lisa.ns.cloudflare.com." ;; ADDITIONAL SECTION: jeff.ns.cloudflare.com. 3462 IN A 173.245.59.124 lisa.ns.cloudflare.com. 3483 IN A 173.245.58.131And under below registration details:
Domain Name: AKILLITELEFONBURADA.COM Registrar: NICS TELEKOMUNIKASYON TICARET LTD.STI. Whois Server: whois.nicproxy.com Referral URL: http://www.nicproxy.com Name Server: JEFF.NS.CLOUDFLARE.COM Name Server: LISA.NS.CLOUDFLARE.COM Status: ok Updated Date: 12-jan-2014 Creation Date: 07-jun-2013 Expiration Date: 07-jun-2014We will have to deal with the Turkish law enforcement to nail this guy for good:
DOMAIN: AKILLITELEFONBURADA.COM CREATE DATE: 6/7/2013 11:59:57 AM UPDATED DATE: 1/12/2014 3:25:26 PM EXPIRATION DATE: 6/7/2014 11:59:57 AM RSP: URL: owner-organization:Whois Privacy Protection Service. owner-name:NicProxy owner-lname:Customer owner-street:Mecidiyekoy owner-city:Istanbul owner-state:Sisli owner-zip:34394 owner-country:Turkiye owner-phone:+90.2122132963 owner-fax:+90.2122132963 owner-email:[email protected]No, no, it is NOT a hacking site: (Pls don't give me that preach..)
$ curl akillitelefonburada.com naber? $ $ curl saatlikrapor.com naber? $ date Fri Feb 28 10:10:36 JST 2014 #MalwareMustDie!!
Updates
The domain of WJETPHP.COM which was informed in the top section as the "payload center" (red: CNC) also still alive now with the below details:
$ dig WJETPHP.COM any ; <<>> DiG 9.8.5-P1 <<>> WJETPHP.COM any ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 542 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;WJETPHP.COM. IN ANY ;; ANSWER SECTION: WJETPHP.COM. 299 IN A 46.105.56.61 WJETPHP.COM. 21599 IN NS "mary.ns.cloudflare.COM." WJETPHP.COM. 21599 IN NS "todd.ns.cloudflare.COM." WJETPHP.COM. 21599 IN SOA mary.ns.cloudflare.COM. dns.cloudflare.COM. 2014501676 10000 2400 604800 3600 ;; Query time: 277 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Sun Mar 09 04:12:37 JST 2014 ;; MSG SIZE rcvd: 137As you see, he is still hiding his service behind the cloud flare until now (read: cloud flare's customer).
Moreover, the ownership of the domains:
Domain Name: WJETPHP.COM Registrar: FBS INC. Whois Server: whois.isimtescil.net Referral URL: http://www.isimtescil.net Name Server: MARY.NS.CLOUDFLARE.COM Name Server: TODD.NS.CLOUDFLARE.COM Status: clientTransferProhibited Updated Date: 01-feb-2014 Creation Date: 24-may-2013 Expiration Date: 24-may-2014 >>> Last update of whois database: Sat, 08 Mar 2014 19:17:39 UTC <<< Domain Name: WJETPHP.COM Registry Domain ID: Registrar WHOIS Server: whois.isimtescil.net Registrar URL: http://www.isimtescil.net Updated Date: 24-Jul-2013 Creation Date: 24-May-2013 Registrar Registration Expiration Date: 24-May-2014 Registrar: FBS Inc. Registrar IANA ID: 1110 Registrar Abuse Contact Email: [email protected] Registrar Abuse Contact Phone: +902163299393 Domain Status: clientTransferProhibited URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/ >>>Last update of WHOIS database: 2014-03-08T19:18:12+0000Z<<< Registration Service Provided By: WWW.ISIMTESCIL.NET
Conclusion
How to conclude this matter generally? Obviously the public well-known internet services was targeted to spread this infection. Let me describe how many of those abused services spotted in this single case:
Number one, amazonaws.com (property of Amazon AWS) is utilised by this actor for the etc bad purpose scheme (see the mobile link and Opera browser link on the above explanation, whatever it is, is not a good thing), we'd better warn Amazon AWS for this link.
Number two is, dropboxusercontent.com (property of Dropbox, Inc) is also utilised to serve payload malware.
Is that all? No. Number three: see the domain in payload URL, googlecode.com, it is the abuse of Google Code's SVN facility.
More? Yes, the last one, number four, goo.gl service, the Google ShortURL is also abused to hide the URL of the malware payload.
The Google code is being abused to serve malware payloads of this threat's series for quite a while, you can view the reports posted by our friend @sarimura (twitter) to the Project Hosting on Google Code in Google groups-->[here]. It shows how persistent the malware actor to always create a new google project and to use its download URL to serve the malware payloads. On the other hand it shows that the bad actor(s) is leaving many traces in Google Code servers during uploading the payloads (account ID, IP addresses, etc).. a hint to follow isn't it?
Sample
I share all sample, under usual password, click the picture below to download:

Moral of the story: Our beloved internet and its services are badly abuse by malware. Stay safe please!
PS: Comments and additional are to be added in follow up section! And it looks like this threat is bigger than expected so I could't sleep again, gotta go to day work now!
Updates: How bad the abuse & this malvertisement is?
The bad actor is keep on changing users in AmazonAWS and Google code to serve the next malicious payload.The new abused AmazonAWS page is:
unluvideolari.s3.amazonaws .com/unlu.html URLQuery-->[link]
PoC of how bad the malware download is:

The recent Google Code SVN that's being abused:


Google set a good work-around by 401 authentication:

Now Emerging Threat is releasing a signature that can be used to identify this malware download:

Update Info Credit: @sarimura (twitter), signature: Emerging Threat & @node5 (twitter), test & checks: @urlquery (twitter), thank's to Google to keep on nuking down the bad accounts and nice stats of the sort URL.
Follow Up
Please help suspend user "buexe-x" of GoogleCode, he is spreading malware in via SVN - Attached=download log >@Google pic.twitter.com/FT8cXTFFkg
— MalwareMustDie, NPO (@MalwareMustDie) February 24, 2014To: @sakura_server 添付した画像に書いたサイトがマルウェア感染に悪用されているので、IPはさくらさんのVPSで、ご対応は可能ですか?そのURLから今大変な事になっていた→ http://t.co/D6wJsYHCQf pic.twitter.com/2168JDJyBN
— Hendrik ADRIAN (@unixfreaxjp) February 24, 2014Great follow, thank's for always fast in responses!
@unixfreaxjp ご連絡ありがとうございます。確認いたします。
— さくらインターネット開発の中の人(α) (@sakura_server) February 24, 2014@MalwareMustDie I have been reporting files on @googlecode and they have ignored the last report, apparently: https://t.co/SubFwB6Lc4
— Salim Sarımurat (@sarimura) February 24, 2014Thank's @EmergingThreats for releasing: 2018191 – ET CURRENT_EVENTS SUSPICIOUS .exe Downloaded from SVN/HTTP on GoogleCode (current_events)
— MalwareMustDie, NPO (@MalwareMustDie) February 27, 2014AwazonAWSとGooglecodeのSVN経由マルウェア感染仕組みが未だ続けている http://t.co/7pkuqYkx1Z
どうやっても止められなさそう、潰しても直ぐに出てくる。
国内にもご注意を!
— Hendrik ADRIAN (@unixfreaxjp) February 27, 2014#MalwareMustDie!



