The Ascon family is specified in NIST SP 800-232 (initial public draft): "Ascon-based Lightweight Cryptography Standards for Constrained Devices: Authenticated Encryption, Hash, and Extendable Output Functions".
The original authenticated encryption (AEAD) and hashing schemes (Hash, XOF) Ascon as submitted to the LWC project are specified in the Journal of Cryptology article, the NIST submission, and the CAESAR submission. Additionally, pseudorandom functions (PRF) and message authentication codes (MAC) are specified in the CT-RSA 2024 paper.
NIST's draft standard is similar, but not identical to the submission. Changes include the selection of a subset of schemes (with new names and IV constants); changing the mode to little-endian bit order; adding a customizable hash variant; and other flexible implementation options. Below, we provide a brief overview of the standardized schemes. For full details including the round constant and IV values, the little-endian bit ordering, padding rules, or the almost identical decryption mode, we refer to NIST SP 800-232.
Ascon's Permutation
All Ascon family members use the same lightweight permutation. This permutation iteratively applies an SPN-based round transformation for up to 16 rounds; the standardized modes of operation use 12 rounds in Ascon-p[12], and 8 rounds in Ascon-p[8]. The round transformation consists of the following three steps which operate on a 320-bit state divided into 5 words S0, S1, S2, S3, S4 of 64 bits each:
- Addition of Round Constants: xors a round-specific 1-byte constant to word S2.
- Nonlinear Substitution Layer: applies a 5-bit S-box 64 times in parallel in a bit-sliced fashion (vertically, across words).
- Linear Diffusion Layer: xors different rotated copies of each word (horizontally, within each word).

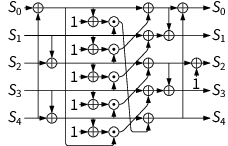
Ascon's permutation: ⊕ denotes xor, ⊙ denotes and, ⋙ is rotation to the right.
Authenticated Encryption with Ascon-AEAD128
Ascon uses a duplex-based mode of operation for authenticated encryption. The key, tag and nonce length is 128 bits. The sponge operates on a state of 320 bits, with message blocks of 128 bits. The encryption process is split into four phases:
- Initialization: initializes the state with the key K and nonce N.
- Associated Data Processing: updates the state with associated data blocks Ai .
- Plaintext Processing: injects plaintext blocks Pi into the state and extracts ciphertext blocks Ci .
- Finalization: injects the key K again and extracts the tag T for authentication.
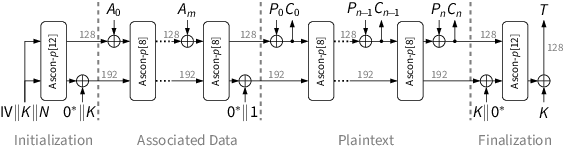
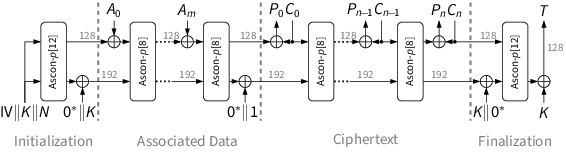
After each injected block (except the last plaintext block), the core permutation Ascon-p[8] is applied to the complete state. During initialization and finalization, a stronger permutation Ascon-p[12] with more rounds is used.
| Cipher | Bit size of | Rounds | |||||||
|---|---|---|---|---|---|---|---|---|---|
| key | nonce | tag | rate | capacity | p[12] | p[8] | |||
| Ascon-AEAD128 | 128 | 128 | 128 | 128 | 192 | 12 | 8 | ||
Hashing with Ascon-Hash256 and Ascon-(C)XOF128
The Ascon family includes the hash functions Ascon-Hash and the extendable output functions Ascon-XOF128 with its customizable variant Ascon-CXOF128. The hashing modes use the same lightweight 320-bit permutation as the authenticated encryption modes. All variants use similar sponge-based modes of operation and provide 128-bit security when using a hash size of at least 256 bits.
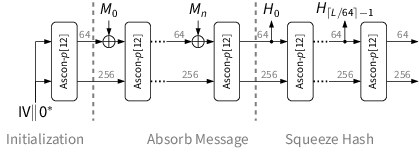
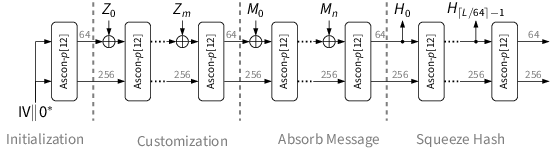
The hashing modes absorb the message M in 64-bit blocks Mi and finally squeeze the hash value H in 64-bit blocks Hi . The customizable variant additionally absorbs a customization string Z in 64-bit blocks Zi before the message M. After each absorbed or squeezed block, the permutation Ascon-p[12] is applied to the state.
| Algorithm | Bit size of | Rounds | ||||
|---|---|---|---|---|---|---|
| hash output | rate | capacity | p[12] | |||
| Ascon-Hash256 | 256 | 64 | 256 | 12 | ||
| Ascon-XOF128 | arbitrary | 64 | 256 | 12 | ||
| Ascon-CXOF128 | arbitrary | 64 | 256 | 12 | ||