 Positive Technologies experts conducted a study[1] of the Q3 2024 cybersecurity threatscape. The study revealed that IT professionals were the most frequent targets of attacks on individuals, and by targeting IT specialists, criminals were able to gain access to IT companies and launched supply chain attacks[2]. Hackers used malicious ads, malware, and even staged fake interviews to trick specialists into downloading malware.
Positive Technologies experts conducted a study[1] of the Q3 2024 cybersecurity threatscape. The study revealed that IT professionals were the most frequent targets of attacks on individuals, and by targeting IT specialists, criminals were able to gain access to IT companies and launched supply chain attacks[2]. Hackers used malicious ads, malware, and even staged fake interviews to trick specialists into downloading malware.
In Q3, attacks against individuals and organisations increased by 15% year-on-year. IT specialists were the primary targets among individuals (13%), and one of the most common methods of such attacks (72%) was malware. Malware was spread through package managers, public repositories, malicious ads, and even fake interviews.
Valeriya Besedina, Junior Information Security Analyst at Positive Technologies, commented: “Beyond financial gain, the surge in attacks on IT specialists can be explained by the attackers’ desire to target larger entities, such as the companies the victims work for. Moreover, by using IT specialists as a point of entry, cybercriminals can infiltrate software supply chains and cause irreparable damage to numerous organisations. Cybersecurity experts note that in 2024, such attacks occurred at least once every two days”.
Q3 saw continued growth in attacks against IT specialists involving remote access trojans (RATs). RATs, which are spread through package managers, public repositories, and malicious ads, give cybercriminals constant access to compromised systems. Cybercriminals created RAT-infected websites mimicking popular network scanning software and promoted them in search engines. A technique based on the PyPI policy relating to removed packages[3], dubbed Revival Hijack, was used by attackers to hijack 22,000 existing PyPI packages. Users weren’t warned about packages being removed and were updating them, unaware of the criminals’ actions.
According to the Positive Technologies study, the most common tools used in attacks on organisations were RATs (44%) and ransomware (44%). In 79% of successful attacks, computers, servers, and network equipment were compromised. The most popular tools were AsyncRAT[4], XWorm[5], and SparkRAT[6]. PT Expert Security Center experts detected phishing emails disguised as invoices used when targeting manufacturing companies, banks, the healthcare sector, and software developers in Russia, leading to infections by the XWorm trojan.
To spread spyware, cybercriminals used services that promoted malicious websites to the top of search results. In Q3, they managed to spread DeerStealer[7], Atomic Stealer[8], and Poseidon Stealer[9] using this tactic.
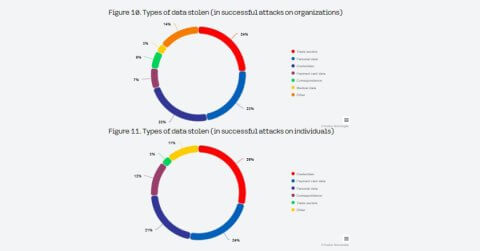
Social engineering remained a major threat to individuals (92%) and was used in 50% of attacks against organisations. Social engineering attacks against organisations and individuals were mainly conducted via email (88%) and websites (73%), respectively. Cyberattacks on organisations led to breaches of confidential data (52%) and disruptions to core business operations (32%).
Positive Technologies recommends that companies build result-driven cybersecurity. Result-driven cybersecurity helps create a comprehensive automated defence system against non-tolerable events—consequences of cyberattacks that could prevent an organisation from achieving its operational or strategic goals. To protect systems against malware, Positive Technologies recommends using sandboxes to analyse file behaviour in a virtualised environment, detect malicious activity, and act in time to prevent damage. The experts also recommend implementing an NTA system, such as PT Network Attack Discovery, which detects all modern cyberthreats, including the use of RATs, spyware, and ransomware. Companies should perform regular inventory and classification of assets, establishing data access control policies, and monitoring access to sensitive information. Positive Technologies recommends using MaxPatrol SIEM for continuous monitoring of cybersecurity events and rapid detection of cyberattacks. It’s also crucial to implement vulnerability management processes using tools like MaxPatrol VM, conduct penetration tests (including automated ones), and participate in bug bounty programs.
Due to the large number of attacks with malware delivered through legitimate services, software developers should pay close attention to the repositories and package managers used in their projects and deploy application security tools, such as PT Application Inspector. It’s also recommended to use web application firewalls (WAFs), such as PT Application Firewall, to strengthen the network perimeter. To protect against data breaches, organisations should focus on data protection measures. IT specialists should remain vigilant online and avoid opening suspicious links or downloading attachments from unverified sources.
[1] This report contains information on current global cybersecurity threats based on Positive Technologies own expertise (Positive Technologies Expert Security Centre), investigations, and reputable sources. This report considers each mass attack as one incident, not several.
[2] A cyberattack in which attackers infiltrate a company by compromising software or hardware suppliers.
[3] PyPI is a repository of software for the Python programming language.
[4] AsyncRAT is malicious software that encrypts and compresses data, then downloads additional components to boost its capabilities.
[5] XWorm is a remote access trojan targeting Windows operating systems. It disguises itself well and can perform various malicious actions, from remote desktop control to ransomware deployment and data theft.
[6] SparkRAT is an open-source tool written in Go and a versatile remote administration trojan that poses a threat to Windows, macOS, and Linux systems.
[7] DeerStealer is a malicious program designed to steal user personal data, sending all stolen information to hacker servers.
[8] Atomic Stealer is a malicious program designed to collect confidential information from infected devices, including passwords, session cookies, cryptocurrency wallet data, and system metadata.
[9] Poseidon Stealer is a malicious program designed to exfiltrate various types of confidential information from macOS devices.
Image Credit: Positive Technologies