Session hijacking is a type of cyber attack where an attacker gains unauthorized access to a user session. This typically involves stealing or manipulating a session token or session identifier, which is a piece of data used to identify and authenticate a user’s session with a web application.
Here’s a step-by-step breakdown of the process:
- Session Establishment: When you log into a web application, the server creates a session for you and sends a session token to your browser, often stored in a cookie.
- Session Management: Each time you make a request to the server, the session token is sent along with it, allowing the server to verify your identity and maintain your session state.
- Session Hijacking: An attacker intercepts or obtains the session token, which can then be used to impersonate you and gain unauthorized access to your session.
Simplified Demonstration
For simplicity, let’s consider a basic web application where a session token is stored in a cookie.
Scenario: Basic Session Hijacking
- Setting Up:
- Victim: Logs into a web application (e.g., https://demo.testfire.net/login.jsp) and receives a session token, such as
abc123, which is stored in their browser cookie.
- Victim: Logs into a web application (e.g., https://demo.testfire.net/login.jsp) and receives a session token, such as

- Attacker: Wants to hijack the victim’s session.
- Session Token Theft:
- Method 1: Network Interception (e.g., Man-in-the-Middle Attack)
- The attacker monitors network traffic, perhaps on an unsecured Wi-Fi network, and captures the session token when the victim’s browser sends it to the server.
- Method 2: Cross-Site Scripting (XSS)
- If the web application is vulnerable to XSS, the attacker injects a malicious script into the site that reads the victim’s session cookie and sends it to the attacker.
- Method 1: Network Interception (e.g., Man-in-the-Middle Attack)
- Using the Stolen Token:
- The attacker obtains the session token
abc123and uses it to make requests toexample.comas if they were the victim. - The attacker’s browser now includes the stolen token in requests, and the server believes the attacker is the victim, granting access to the victim’s account.
- The attacker obtains the session token
For demo purpose, We will inspect the website source code and navigate to application and grab the session cookies.

Stolen Cookie:
Attacker stolen cookie was “74F2BA691165ACD139BF173518C74DD4” and attacker uses his own web browser edge here.
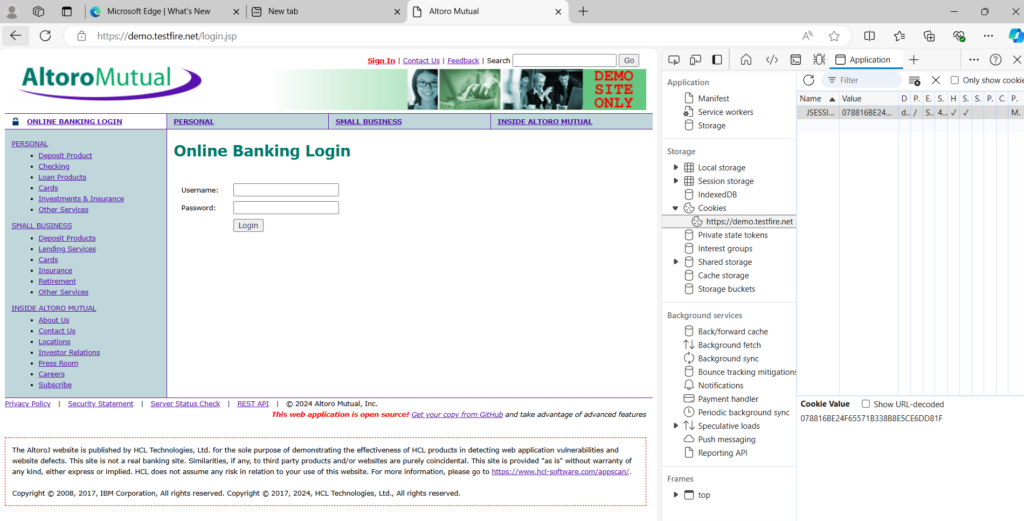
Attacker will navigate to login page and inspect the application to view the cookie, Right now he will use the stolen cookie and press enter and refresh the page and navigate to “MY ACCOUNT” in the web page.

Attacker has logged in using the stolen session cookies. The majority of sites today are not hacked through password brute force attacks, but rather through session hijacking threats.
Use Case: Mitigating and Detecting Cookie Session Hijacking
1. Overview In this use case, an organization aims to protect its web application from session hijacking attacks by implementing both preventative measures and detection mechanisms. The goal is to ensure that user sessions remain secure and any potential hijacking attempts are promptly identified.
2. Actors
- User: Interacts with the web application and uses cookies for authentication.
- Web Application: Manages user sessions and authentication.
- Security Team: Implements and monitors security measures.
- Attacker: Attempts to hijack user sessions by stealing or manipulating cookies.
3. Preconditions
- The web application uses cookies for maintaining user sessions.
- Users are authenticated and have valid session cookies.
4. Goals
- Mitigation: Prevent session hijacking by using secure cookie practices.
- Detection: Identify and respond to potential hijacking attempts.
5. Mitigation Strategies
a. Use Secure and HttpOnly Flags
- Secure Flag: Ensure cookies are only sent over HTTPS connections, preventing them from being exposed during non-secure transmissions.
- HttpOnly Flag: Prevent JavaScript access to cookies, reducing the risk of XSS (Cross-Site Scripting) attacks.
b. Implement SameSite Attribute
- SameSite Attribute: Set the SameSite attribute to “Strict” or “Lax” to mitigate CSRF (Cross-Site Request Forgery) attacks by controlling when cookies are sent with cross-site requests.
c. Use Short-Lived and Rotating Cookies
- Short-Lived Cookies: Reduce the lifespan of session cookies to minimize the window of opportunity for an attacker.
- Session Rotation: Implement periodic session ID rotation to limit the impact of a stolen session ID.
d. Implement Multi-Factor Authentication (MFA)
- Require MFA for sensitive actions or login attempts to provide an additional layer of security.
e. Monitor and Enforce IP Address and User Agent Validations
- IP Address Validation: Check if the IP address associated with the session matches the IP address of the request.
- User Agent Validation: Validate that the User Agent string of the request matches the User Agent string associated with the session.
6. Detection Strategies
a. Log and Monitor Session Activity
- Activity Logging: Log user session activity, including IP addresses, User Agent strings, and timestamps.
- Anomaly Detection: Use security information and event management (SIEM) tools to analyze logs for unusual patterns, such as multiple logins from different IP addresses in a short time frame.
b. Implement Session Anomaly Detection
- Behavioral Analysis: Employ machine learning or rule-based systems to detect deviations in user behavior that could indicate session hijacking.
c. Use Web Application Firewalls (WAFs)
- WAF Rules: Configure WAFs to detect and block suspicious requests that may indicate session hijacking attempts.
d. Implement Real-Time Alerts
- Alert Mechanisms: Set up real-time alerts for suspicious activities such as sudden changes in session attributes or unusual login patterns.
7. Post-Attack Measures
a. Session Termination
- Invalidate Sessions: Upon detection of a hijacking attempt, immediately invalidate the compromised session and prompt the user to re-authenticate.
b. User Notification
- Inform Users: Notify affected users of the potential breach and provide guidance on securing their accounts.
c. Incident Analysis
- Forensic Investigation: Analyze the attack to understand the method of hijacking and improve defenses.
8. Conclusion By implementing a combination of preventive measures and detection mechanisms, the organization can significantly reduce the risk of cookie session hijacking and respond effectively if such an attack occurs. Continuous monitoring and updating security practices are essential to adapting to evolving threats.
This use case outlines a comprehensive approach to securing session cookies and responding to potential threats, helping maintain the integrity and security of user sessions.



































