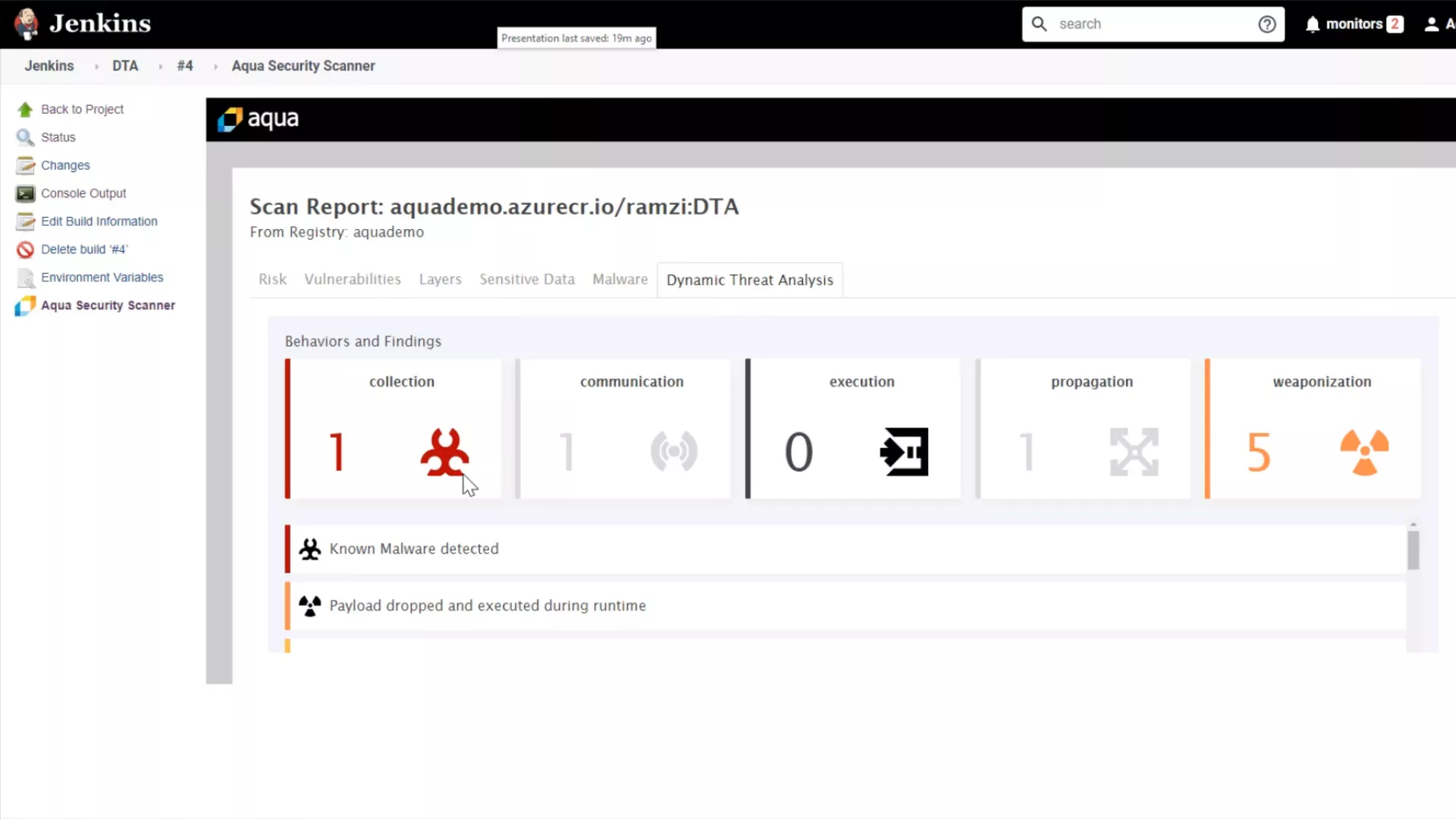
Aqua Tracee: Runtime eBPF threat detection engine
Detect known and unknown attacks with the most comprehensive eBPF-based threat detection engine
Get TraceeThe most powerful, accurate and reliable eBPF-based detection engine
Tracee has used eBPF since inception and collects 330 syscalls (and other non syscall events) right out of the box. Unlike solutions built on kernel modules, eBPF is safe and fast. And Tracee uses cutting edge eBPF features to prevent evasion by attackers.
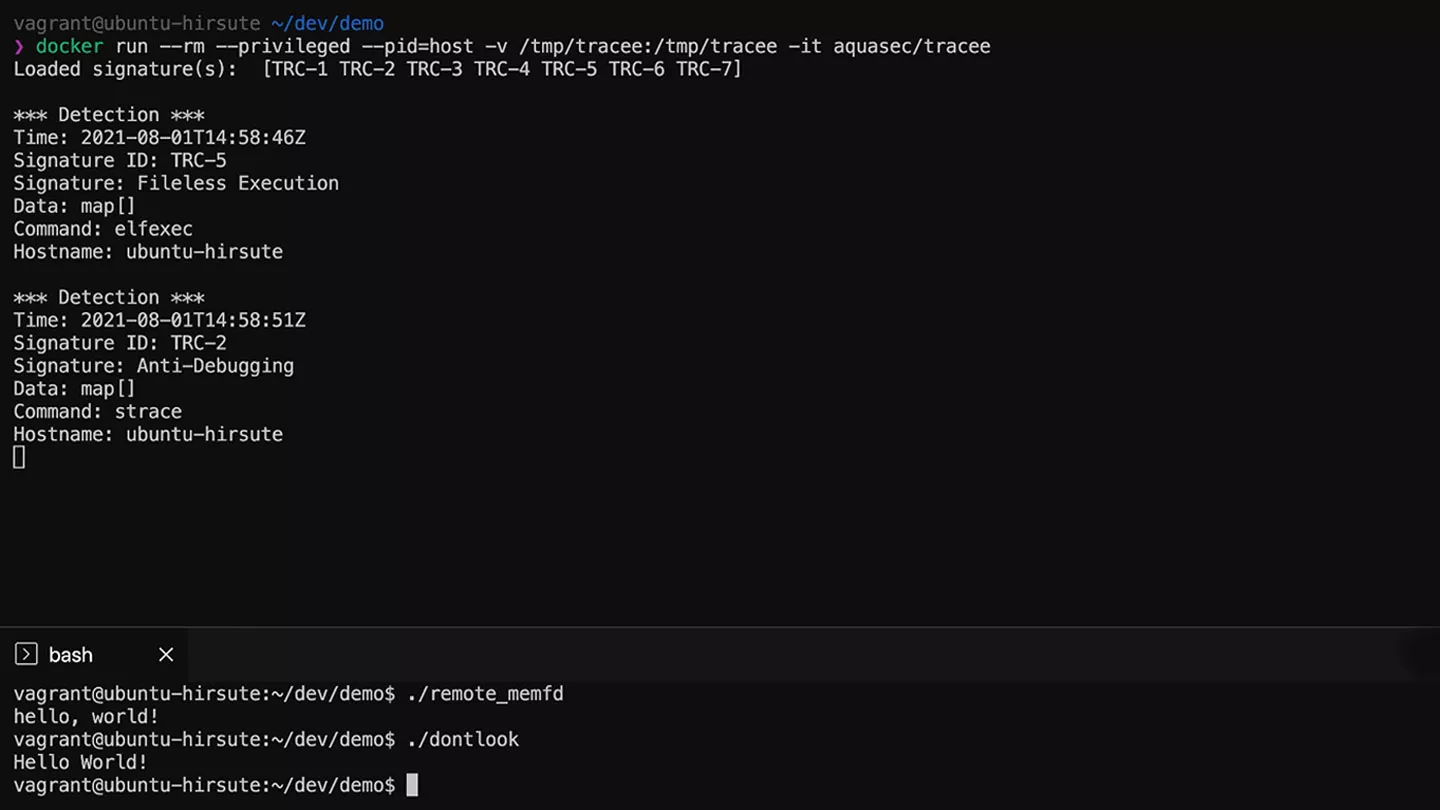
Detect suspicious behavior patterns with Tracee Rules
Curated behavioral indicators identify defense evasion techniques, as defined in the MITRE Att&CK framework, based on the events collected by the Tracee’s eBPF engine. Indicators include activity such as fileless execution, anti-debugging and kernel module loading.
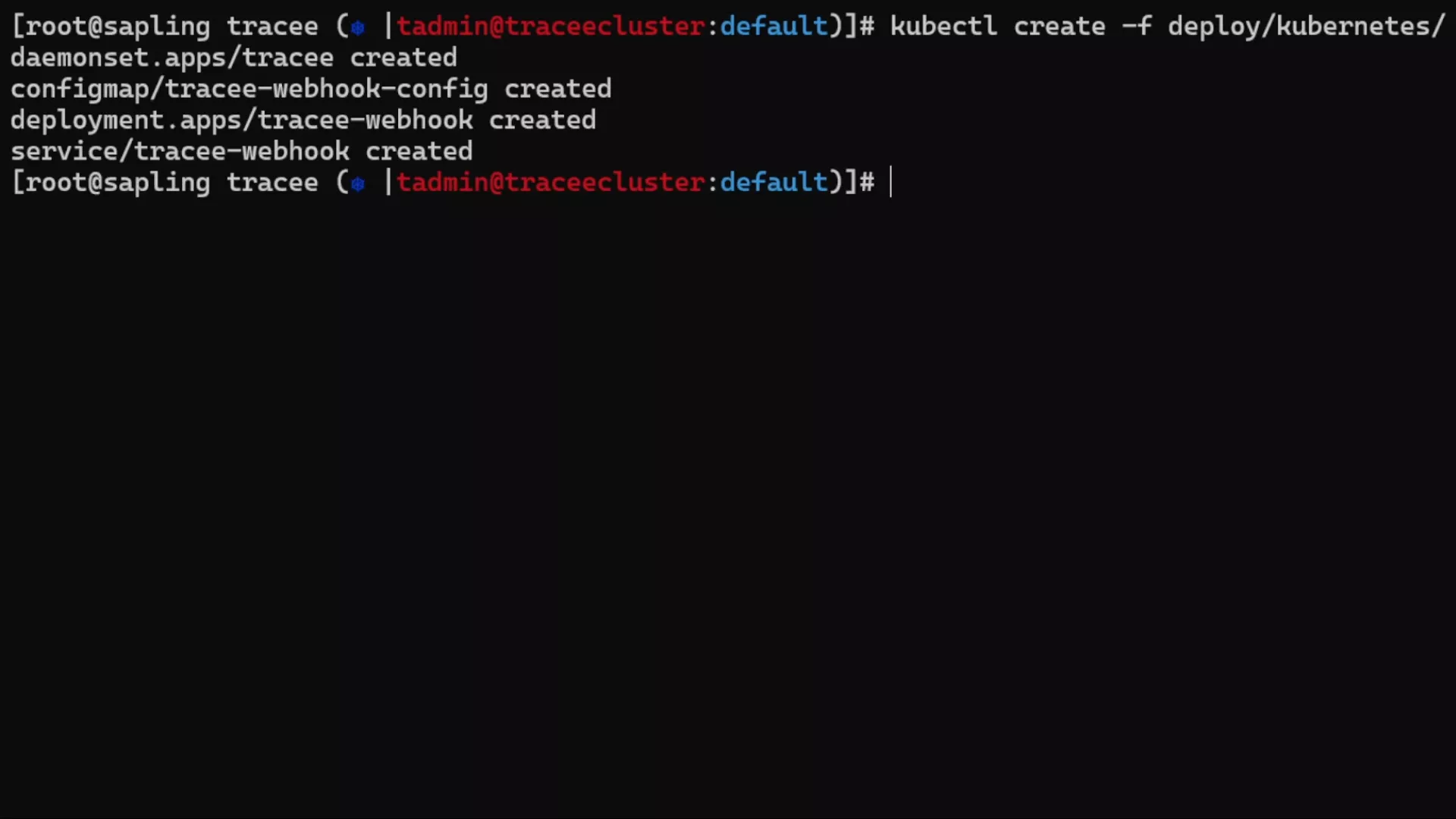
Easy deployment, maximum portability and easy integrations
Deploying Tracee with Kubernetes and Docker is a simple “kubectl create” or “docker run” command. Run Tracee with and without BTF support and enjoy maximum portability for different Linux versions using CO:RE mode. Send Tracee data to external notification tools such as Slack or GitHub Actions via projects such as Postee.
Customize and filter intel by relevance and priority
Use filters to customize where to look for events within specific clusters, containers and hosts. Capture artifacts such as network packets and executables for further analysis only from the most meaningful locations. View insights easily from output templates ranging from JSON files to a GO template for customization.

Relied on for industry-leading threat detection
Tracee is the eBPF engine behind industry-first commercial capabilities of the Aqua Platform such as Dynamic Threat Analysis (DTA), the container sandbox, and Cloud Native Detection and Response (CNDR). DTA, CNDR and Tracee are the only solutions in the industry to combine behavioral indicators from a dedicated cloud native security research team, Nautilus, with eBPF events for real-time threat detection in runtime.