
The Hack In The Box (HITB) SecConf 2014 was held from the 13 to the 16 of October, in Kuala Lumpur, Malaysia. More than 500 people from around the world participated in the event. Unfortunately, 2014 was the final round of this nice event.
The event is made up of four main elements: Technical training sessions, a security conference, Capture the Flag ‘Live Hacking’ Attack & Defense Competition, Developer Hackathon (HackWEEKDAY) and A CommSec Village & Technology Showcase Area.
Although there were many interesting presentations at the conference, I have too little space here to introduce all of them, so let’s take a look of three of them.
Filippo Valsorda gave a presentation entitled “Exploiting ECDSA Failures in the Bitcoin Blockchain”. Elliptic Curve Digital Signature Algorithm (ECDSA) is an EC-based signature scheme as implemented in TLS, DNSsec and PS3. He pointed out that ECDSA might not be as secure as it is believed to be.
Haroon Meer, Marco Slaviero and Azhar Desai picked up the topic of “sockpuppet”- a false online identity adopted for deceptive purposes – in their presentation. They demonstrated mass-posting, mass-voting and mass-down-voting at some forums, with the help of only one line of bash script. The presentation was entitled “Weapons of Mass Distraction: Sock Puppetry for Fun & Profit”.
Mike Ryan’s “The NSA Playset: Bluetooth Smart Attack Tools” presentation introduced a series of tools used by the NSA and demonstrated keyboard hijacking via Bluetooth using some of the tools.
For those who are interested, the presentation materials are available at the official web site of HITB2014.
The CTF session was also quite interesting. Let’s take a look at Challenge 2.
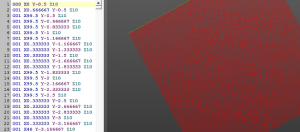
As a problem to solve, a pcap file was provided. It was a capture of some network traffic.
Inspecting the file, you could find that ICMPv6 packets contain unknown strings that start with “G01”. In fact, the strings are G-codes, computer numerical control commands (for industrial hardware, 3D printers, etc.). If is it run using emulator software, a string is displayed – this is the answer to the problem.
In my opinion, CTF is a good exercise for IT engineers, because it gives the chance to learn technologies that are not familiar to you.
In the closing session, the event organizers announced the end of HITB KUL and the beginning of a new event “HITB GSEC“. This is planned to take place in Singapore in October 2015.
I hope the new HITB GSEC will be as fantastic as HITB KUL and I’m looking forward to meeting great security specialists there again!!




























Hack In The Box 2014 KUL