This README documents the process and configuration needed to connect Puppet Enterprise to Google Cloud Directory as an external directory for managing RBAC. While this configuration has been validated there are caveats, Puppet Enterprise only officially supports Active Directory or OpenLDAP and you'll be required to configure stunnel to handle encryption and authentication of your PE console services to Google's LDAP frontend due to Google's requirement for certificate based client authentication not currently supported in Puppet Enterprise for LDAP external directories.
A request to support client certificate authentication in the Puppet Enterprise console's external directory configuration has been submitted but the feature has not yet been roadmapped.
-
Setup and create a client certificate for Google Cloud Directory
- Begin specifically with the items indicated as 1, 2, 3, and 5 in the linked support article
- After finishing the previous process Puppet Enterprise requires you to provision Access credentials
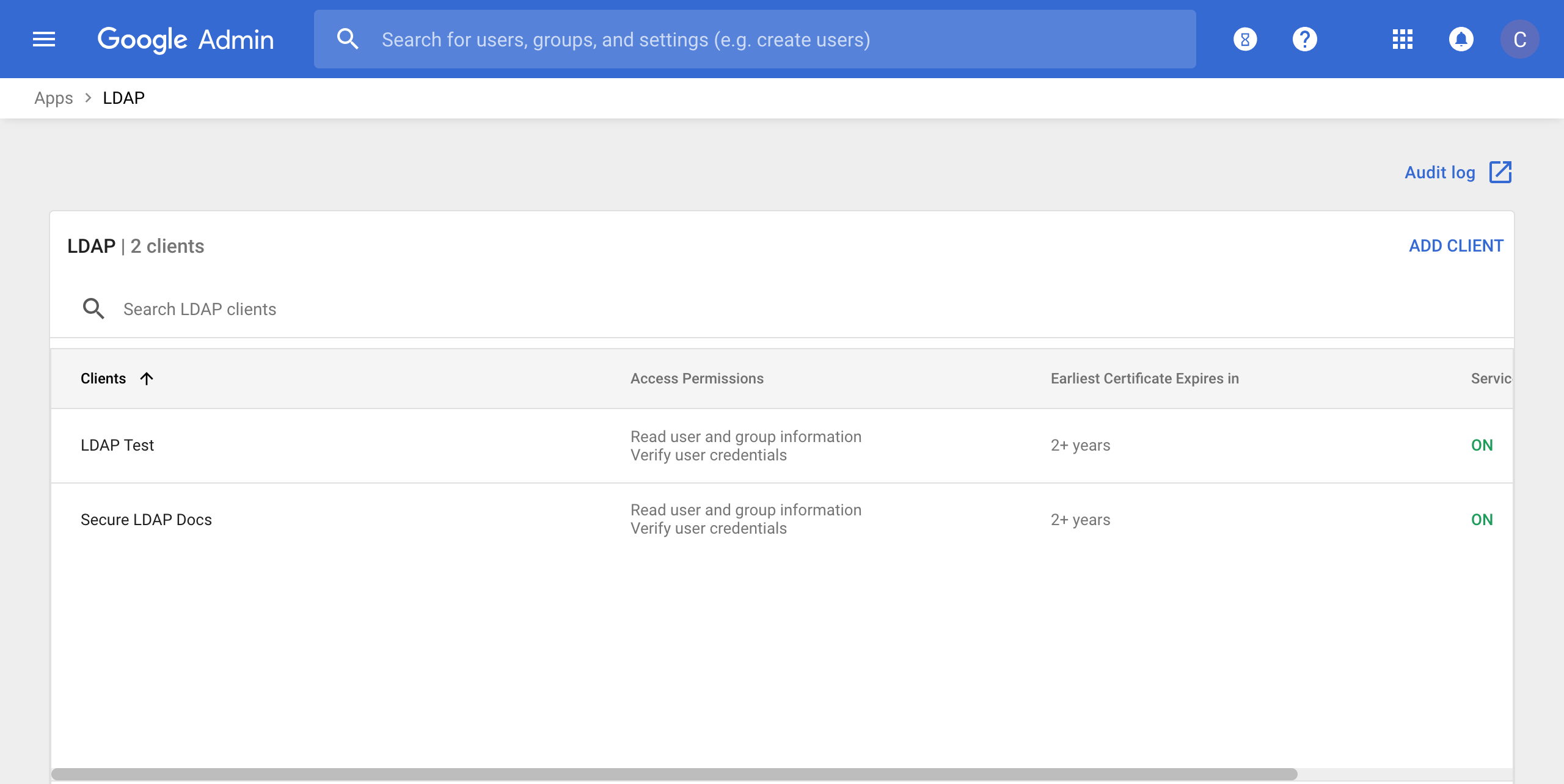
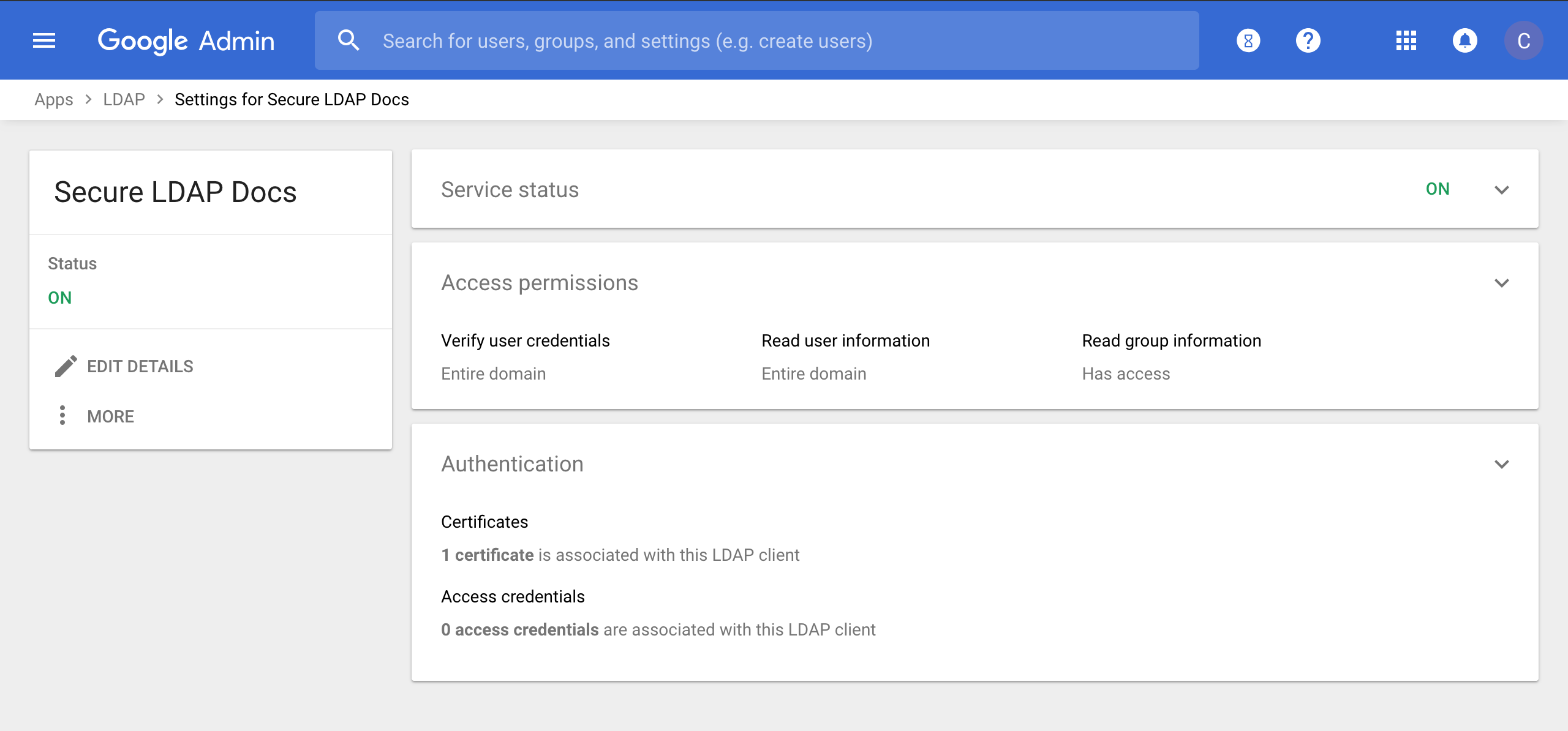
- Return to the LDAP app that lists the clients that you've provisioned and select the client you previously provisioned for the use with PE, in my example I named mine Secure LDAP Docs
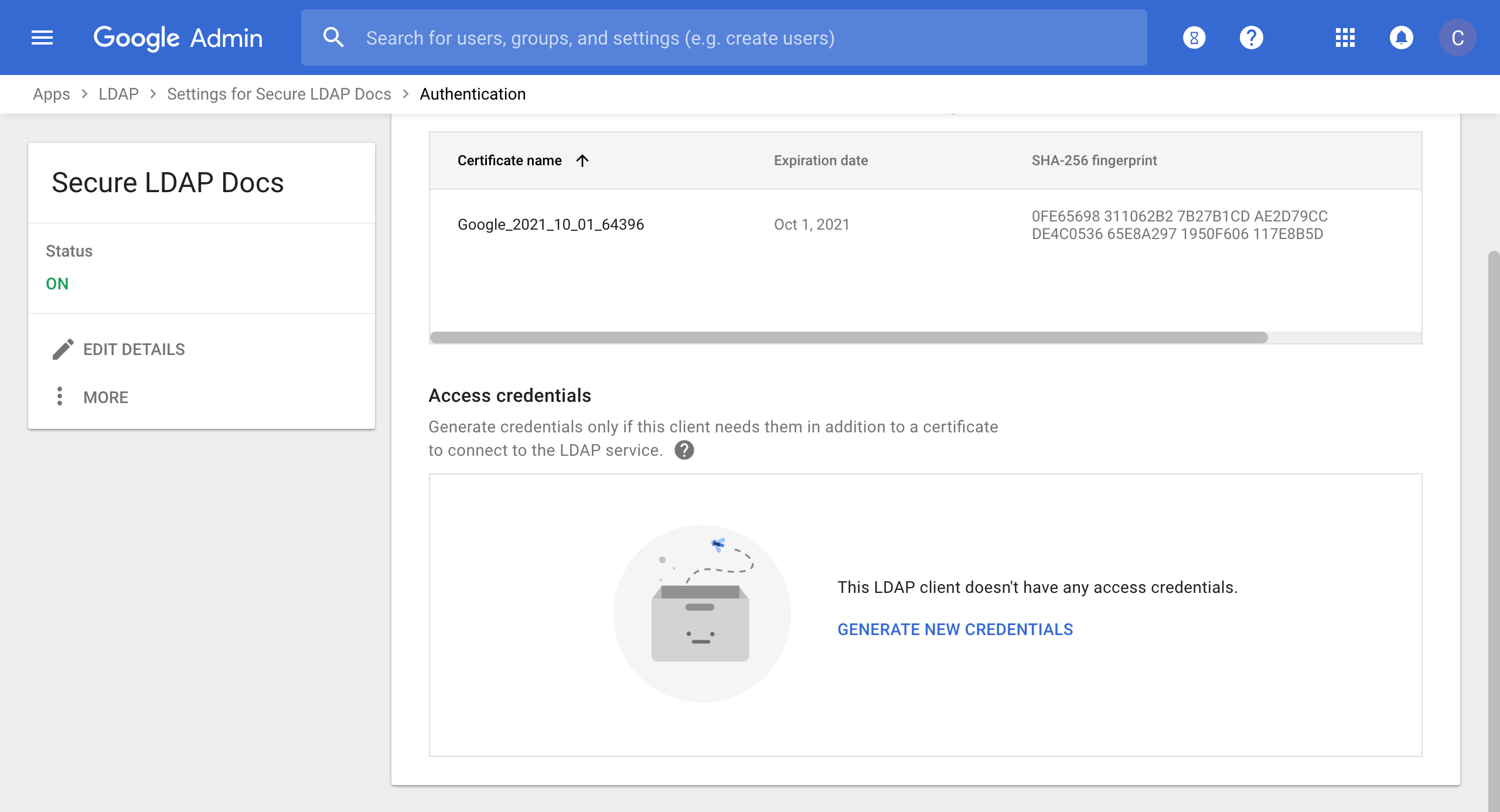
- This'll open the client's settings pane which should near the bottom have panel Authentication that lists 1 certificate and 0 access credentials, click on Access Credentials
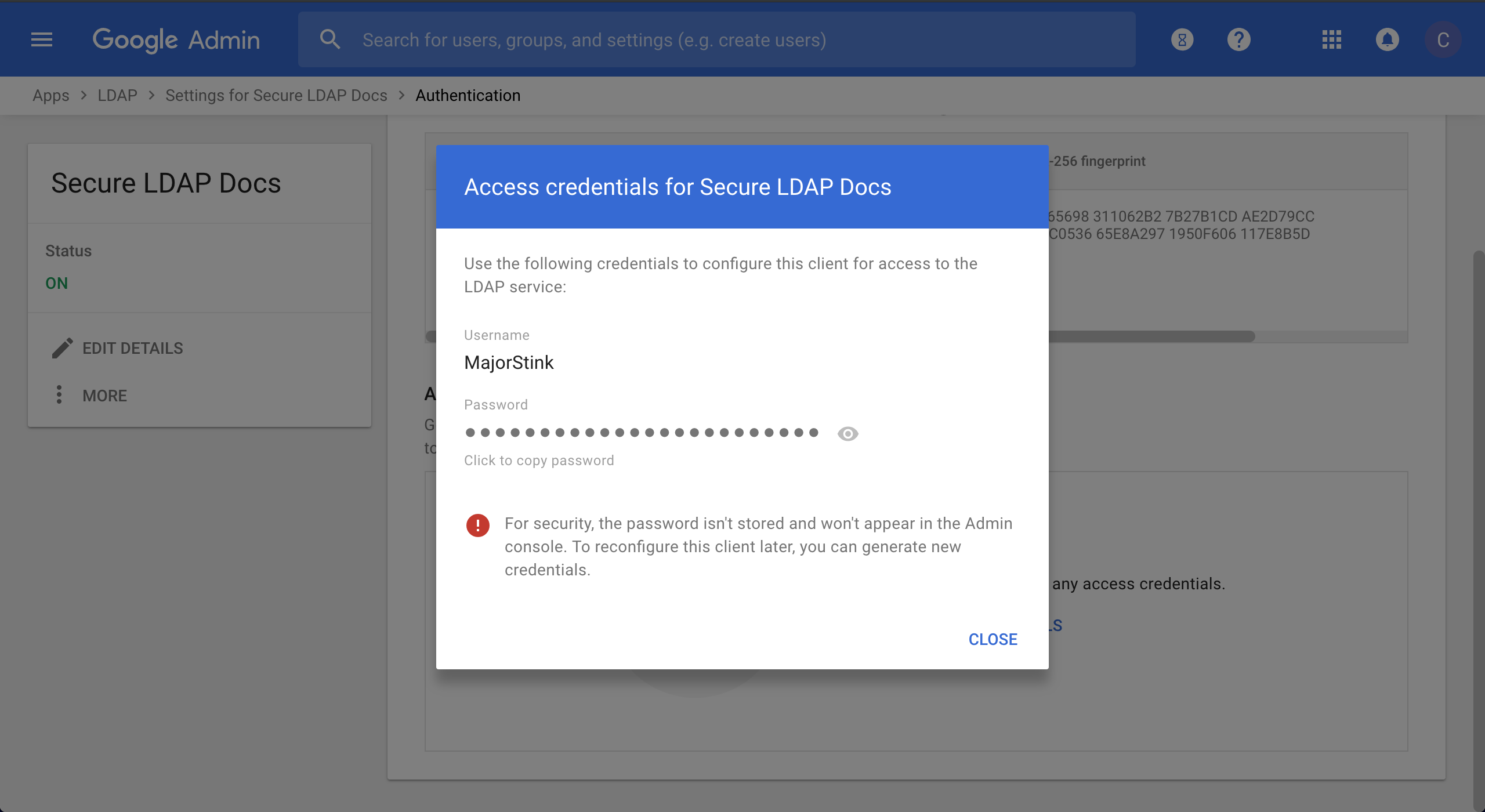
- Scroll down the new pane and click GENERATE NEW CREDNTIALS and a new random user name and password will be created
- Save the credentials provided in the resulting popup pane, you won't be able to retrieve after dismissing the pane
-
Setup Puppet Enterprise to your liking if you haven't already done so
- Package installation
apt install stunnel4
- Create the configuration file /etc/stunnel/google-ldap.conf with the following contents (change the ldap-client.key and ldap-client.cert to reflect the name of the certificate downloaded during Google Cloud Directory setup and client certificate creation)
[ldap]
client = yes
accept = 127.0.0.1:1636
connect = ldap.google.com:636
cert = /etc/stunnel/ldap-client.crt
key = /etc/stunnel/ldap-client.key
-
Upload LDAP client certificate and key obtained previously to the machine running your Puppet Enterprise console services and place them into the /etc/stunnel directory
-
Enable stunnel, edit /etc/default/stunnel4 so that ENABLED=1
-
Start/restart stunnel
systemctl restart stunnel4
- In the following example configuration you'll see a need for Lookup user and Lookup password, these were provisioned and provided to you as Access credentials once you completed the additional Google Cloud Directory setup.
- From within Puppet Enterprise, SSL functionality for communicating with LDAP has been disabled in order to make it possible to leverage stunnel to do the certificate based authentication that is required by Google Cloud Directory; credentials are encrypted by stunnel is this configuration
| Name | Example Google Cloud Directory settings |
|---|---|
| Directory name | Google Cloud Directory (example.com) |
| Login help (optional) | https://example.com/docs/google-puppet-login |
| Hostname | 127.0.0.1 |
| Port | 1636 |
| Lookup user (optional) | ExampleCloudDirectoryUser |
| Lookup password (optional) | the_secure_ldap_provisioned_password |
| Connection timeout (seconds) | 30 |
| Connect using: | Plain text (insecure connection) |
| Validate the hostname? | No |
| Allow wildcards in SSL certificate? | No |
| Base distinguished name | dc=example,dc=com |
| User login attribute | uid |
| User email address | |
| User full name | displayName |
| User relative distinguished name (optional) | ou=Users |
| Group object class | groupOfNames |
| Group membership field | memberUid |
| Group name attribute | displayName |
| Group lookup attribute | cn |
| Group relative distinguished name (optional) | ou=Groups |
| Turn off LDAP_MATCHING_RULE_IN_CHAIN? | No |
| Search nested groups? | Yes |