-
Notifications
You must be signed in to change notification settings - Fork 485
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Try out scorecard action #1074
Comments
|
FYI @azeemsgoogle |
I would personally remove the notes entirely -- I don't think they have much value to the user (who could maybe go see a list of checks anyway on Scorecard), and I think it makes the important stuff less visible.
I like it long, don't like link chasing.
Is this the title? If so is it canonical to have the title be the action of the check, or something indicating it's wrong, e.g. difference between "Determines if..." and "Check failed: Project workflow does not follow" |
|
This looks great. Some comments:
|
|
Thanks both of you for the feedback!
the description is set to the long description atm. It does not support links. Maybe we should remove it? Note that the description is also used by GH next to the line with the rule ID https://github.com/ossf/scorecard/security/code-scanning/2865?query=ref%3Arefs%2Fheads%2Fmain so it's redundant. I have not tested what happens when there are multiple file locations reported.
Looks like nobody likes it :-)
in the making, yes. |
|
note: if a check has multiple findings (e.g. multiple binaries found in repo), GH only shows the first finding... which is not ideal. There's not much I can do about it though...:( |
Interesting. Any reason there can't be multiple findings from a single check? |
|
Unless I've broken something again, you should see severity levels in the scanning alert tab for our GitHub action https://github.com/ossf/scorecard/security/code-scanning |
It is lot better 👏 |
|
Are specific permissions needed to see https://github.com/ossf/scorecard/security/code-scanning ? I receive a 404 @laurentsimon |
You need write permission to view a summary of all the alerts for a repository on the Security tab. |
|
@tom--pollard thanks for the interest in trying it out! You can easily test it out on a repo you own:
The workflow currently supports cron triggers and push triggers for the main/master branch only. I suggest you try the push trigger on the main branch as configured in our workflow yaml file. As a simple verification test, I created a few dummy Let me know if you encounter problems. |
|
@asraa @priyawadhwa would you be interested in trying out the action on sigstore, envoy and tekton repos? |
|
@laurentsimon What's the latest on this? Love seeing the scorecard integrate with Actions and the code-scanning tab. Let me know if you need any connection to get that into the code scanning actions list in the security tab. |
|
Thanks, Also what is the process to get it verified https://docs.github.com/en/developers/github-marketplace/github-marketplace-overview/about-marketplace-badges? |
Thanks Justin. Is this the same as being published on the market place? (We'd love to do that). What's a typical timeline to have an action published? |
|
@laurentsimon There are a couple of places you can get this listed including the marketplace and the code scanning tab (eg https://github.com/ossf/scorecard/security/code-scanning/setup). We'd be happy to work with you on this. Let me tag my colleague @josepalafox who can follow-up on the process bits? |
Thanks! |
|
When you make a release of the action there's a checkbox for admins to "publish to marketplace" assuming you have the right permissions you should just see this, else TO-DO is get the permissions or find someone with them that can publish to marketplace: Next please make a PR using the security starter workflow template here: Ignore parts of the prompt that are not applicable like "are you a part of the parter program?". The major pieces will be the full SHA, logo, 140 char discription, and the workflow.yml file. I would like to float some additional development ideas for this action that I think could be really helpful if there's a committee meeting I can attend to share a few ideas let me know. |
|
Thanks for the info. We'll start looking into this. |
|
@laurentsimon I wonder if it would be possible to run it on PRs to analyze diffs to make sure new alerts or regressions aren't introduced? While running it on push events is helpful I think it would be even better if PRs with new alerts didn't make it to repositories in the first place. |
|
yes, we have a working prototype that runs on PR already. GitHub takes care of de-deduplication using the SARIF format, so we (scorecard) need not worry about diff ourselves, which is really helpful. |
Good to know. Thanks! Just to be sure, does that mean that I can in theory start using it in my experimental fork? I took a look at the config at https://github.com/ossf/scorecard/pull/1073/files#diff-4341708db212df7d9bb86a51df68dc97ff9a262aec1eacddff2552a363b08c9f. Is my understanding correct that to turn on just the "token-permission" check I should add something like ? What happens if I turn on another check where the score is, say, 5 and it stays the same when a PR with new issues is opened? |
|
@laurentsimon I ran the action and noticed that the "binary artifacts" alerts I complained a lot about were classified as "(Test)": so it seems #1270 could be put on hold in a way. Anyway, is that a GitHub feature? If so, I wonder how it's implemented? It would help to solve #1256 |
|
I think it's a GitHub feature, yes. I suspect they look for test in path. @josepalafox do you know? |
|
@josepalafox thank you for the link! Unfortunately it isn't mentioned there how it's implemented. My guess would be that the code assigning labels to alerts came from LGTM and based on my experience with it it's pretty tuned so it would be great if it could be borrowed somehow. I opened #1263 a few days ago where I filtered out all the files containing @laurentsimon looks like some checks like "Fuzzing" and "CII-Best-Practices" shouldn't pop up when the action is run on forks (to be honest, I don't think "CII-Best-Practices" should pop up anywhere at all even though all the projects I more or less contribute to have it). Anyway, would it be possible for the action to avoid reporting some issues depending on where it's run. I of course can always add |
Interesting idea. Which checks would you like to keep in a fork? |
|
@laurentsimon initially I thought that "Fuzzing", "CII-Best-Practices", "Signed-Releases", "Branch-Protection" and "Packaging" should be excluded there and then I realized that some forks are used to keep "stable" branches of upstream projects that are used by downstream projects like various linux distributons and there "Signed-Releases", "Branch-Protection" and "Packaging" probably shouldn't be skipped. so it seems only "Fuzzing" and "CII-Best-Practices" can be safely turned off when forks are analyzed. The other checks I think should probably be configured via the config file and |
|
Regarding "CII-Best-Practices" I think it shouldn't affect the score at all and if it should be promoted for whatever reason it would make sense to make it informational. The problem is that all that check shows is that at some point in the past some projects followed the practices CII considers "best practices" and generally they aren't kept up to date so looking at a badge I can't be sure that whatever it says is up to date. For example, at some point the systemd project used only Coverity Scan and when it was down for almost half a year the badge kept saying a static analysis tool was used. When projects migrate from one hosting service to another they tend to lose a couple of jobs where code is covered with sanitizers for example and their badges don't reflect that. This static nature of the CII badges I think isn't exactly in line with |
|
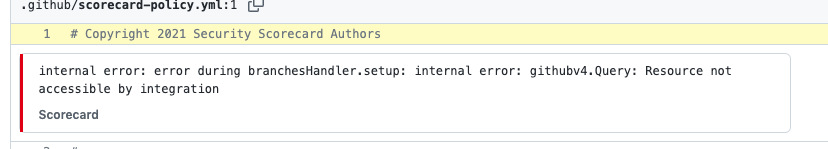
@laurentsimon trying to figure out why I got |
|
Also it doesn't seem to be possible to pass "--verbosity Debug" to |
We've seen this error before. Thanks for sharing. |
great point. I could do a debug build. Currently scorecard ignores Debug messages when creating SARIF output. I can hack something up temporarily to help you debug. I could add it to the description maybe for debugging? |
can you create a tracking issue for this? |
I think this feature should be permanent to make it easier for maintainers to dispute scorecard findings :-) It should be turned off by default probably though
Done: #1304 |
|
@laurentsimon I'm not sure the action can be used when PRs are opened until issues like #1268 (comment) keep affecting the checks unpredictably. Diffs will most likely trigger bogus alerts unrelated to PRs due to checks like SAST and CI-Test producing different scores depending on when they are run. |
|
these checks are not enabled on pull requests by default. The reasoning is that a pull request cannot fix them, so a developer would need to disable scorecard or change its config until the checks passes. We considered this a usability issue. In a nutshell, we only enable checks that a PR may have an effect on, i.e., those that only use source code and not GitHub APIs. It's indicated in the https://github.com/ossf/scorecard/blob/main/docs/checks/internal/checks.yaml#L21: |
|
Good to know. Thanks! I think that makes sense. I saw |
|
FYI, I'm going to be updating the repo of the scorecard action according to https://docs.github.com/en/actions/creating-actions/publishing-actions-in-github-marketplace#about-publishing-actions, so the scorecard action will break sometimes in the next few days. I'll post a message here when the transition is done. |
|
I'm doing some dogfooding. Given the issue #1415, I've created a second action to see if folks prefer the original one or the v2 one. This dogfoodv2 creates different result entries in the dashboard for all checks, including the Branch-Protection settings, Dependency-Update-Tool and SAST (those had a single entry in the dasboard in the previous version). For Dependency-Update-Tool, this mean one entry is created if dependabot is disabled and another one if renovabot is disabled. If at least one of the tools is configured, both dashboard results will be marked as "fixed" and will no longer show up. I wonder if you find this good or confusing. Essentially, every For SAST, it means you'd see one entry for For Branch-Protection, it's pretty simple: one entry for each (settings,branchname) pair. Here are the steps if you'd like to help me compare it to the previous version:
|
|
Closing this as we have been already using it. |
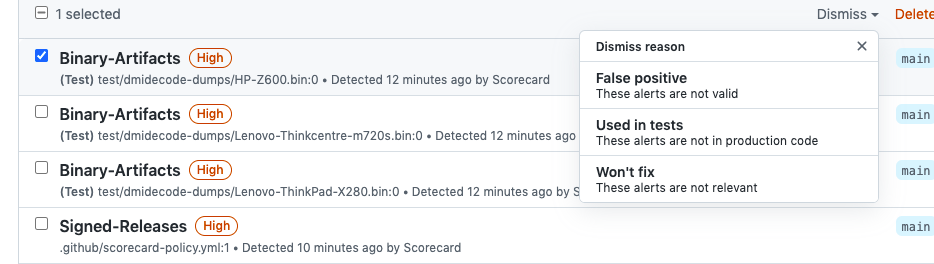
once #1073 is landed.
For each push, scorecard will run and the results will be available in https://github.com/ossf/scorecard/security/code-scanning
I would like some feedback about the results. I've already noticed some improvements needed:
note. Do we want to keep as-is or remove the notes entirely? Note that it may be useful to keep it in SARIF format in general, but remove it for GitHub actions only.The text was updated successfully, but these errors were encountered: