Security campaigns with Copilot Autofix are now in public preview. Available as part of GitHub Advanced Security, security campaigns rapidly reduce your backlog of application security debt. By using Copilot Autofix to generate contextual explanations and code suggestions for up to 1,000 historical code scanning alerts at a time, security campaigns help developers and security teams collaborate to fix vulnerabilities with speed and confidence.
Code scanning detection engines such as GitHub’s CodeQL are incredibly effective at automatically notifying developers about potential security vulnerabilities in their code in the form of code scanning alerts. Most developers fix these vulnerabilities with the help of Copilot Autofix when they’re flagged pull requests. However, in situations where these alerts aren’t remediated in a timely manner, security debt can build up and pose a serious risk to deployed applications. Using security campaigns, security teams and developers can easily collaborate to remediate and eradicate security debt at scale, with the help of Copilot Autofix.
A security campaign on GitHub can contain a large number of code scanning alerts, prioritized by your security team to be fixed within a chosen timeframe. When a campaign is created, Copilot Autofix automatically suggests fixes for all supported alerts, and developers who are most familiar with the code are notified. From there, they can review the fixes, open pull requests, and remediate the security debt.
Security teams can monitor the progress of the campaign and track the number of alerts that have been fixed. Using security campaigns, security and developer teams work together with Copilot Autofix to remove security debt in targeted efforts aimed at maximizing impact by focusing on the alerts that matter.
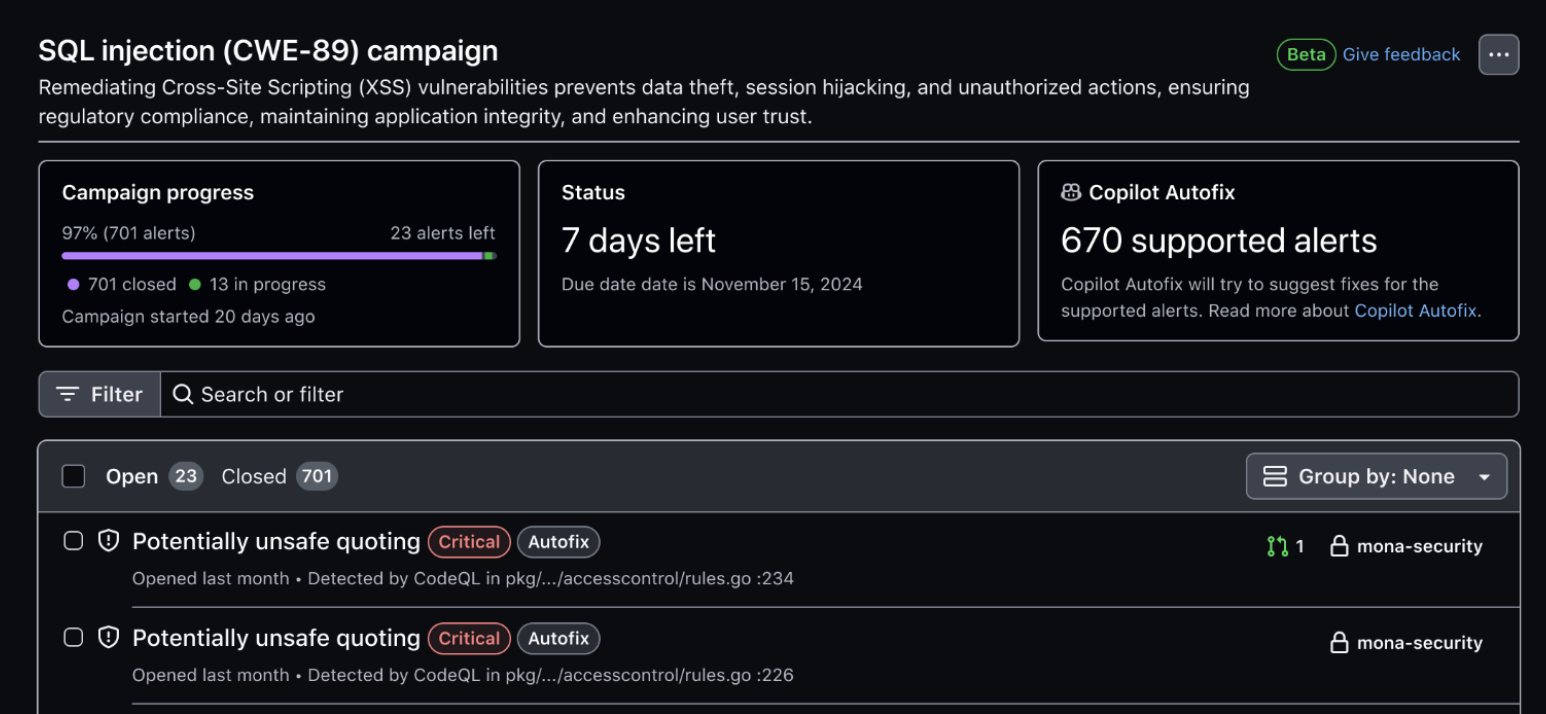
Security campaigns are available for users of GitHub Advanced Security on GitHub Enterprise Cloud. For more information about security campaigns, see About security campaigns in the GitHub documentation.
If you have any feedback on security campaigns: join the discussion in the GitHub Community.

