You can now enroll in a private preview to use GitHub-owned storage when migrating repositories to GitHub Enterprise Cloud using GitHub Enterprise Importer (GEI). This means that you no longer need to provide GEI with access to a customer-owned storage account via shared access keys to perform repository migrations. Instead, migrations can now be performed with repository archives uploaded directly to GitHub.com.
Once enrolled in the preview, repository migrations can be initiated to use GitHub-owned storage via the gh gei and gh bbs2gh command line extensions by passing in the --use-github-storage flag.
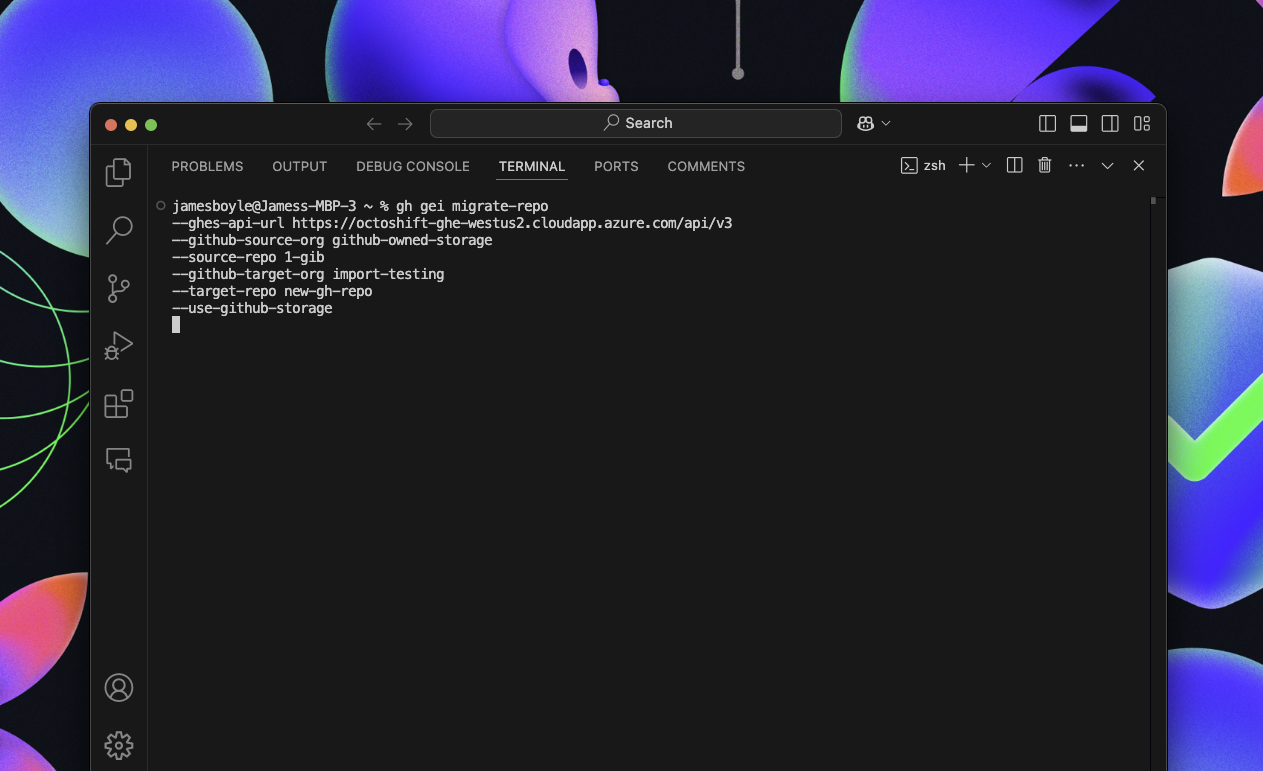
If you’re interested in participating in this private preview, please reach out to your GitHub account manager or contact our sales team to have this feature enabled for your enterprise. For additional technical details, instructions for running repository migrations with GitHub owned storage, or to provide feedback on this feature, please check out our community discussion post.


