Strong Data Encryption Protects Everyone: FPF Infographic Details Encryption Benefits for Individuals, Enterprises, and Government Officials
Today, the Future of Privacy Forum released a new tool: the interactive visual guide “Strong Data Encryption Protects Everyone.” The infographic illustrates how strong encryption protects individuals, enterprises, and the government. FPF’s guide also highlights key risks that arise when encryption safeguards are undermined – risks that can expose sensitive health and financial records, undermine the security of critical infrastructure, and enable interception of officials’ confidential communications.
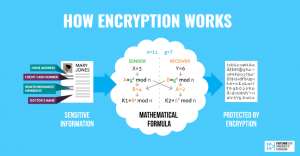
Encryption is a mathematical process that scrambles information; it is often used to secure or authenticate sensitive documents. Each use of encryption generates a very long number that is the mathematical solution to the formula and can unscramble the protected sensitive information. This “key” must be kept a secret or anyone who has it will be able to access the information.
Strong encryption employed by online services and connected devices protects sensitive communications and stored data. Strong encryption protects individuals when they use a smartphone, browse the web, bank online, or send electronic messages to family and colleagues. Encryption can also help authenticate credentials, preventing criminals from impersonating users, viewing confidential email and photos, emptying bank accounts, or taking control of power plants and vehicles.
Strong Data Encryption Protects Everyone demonstrates how encryption technologies protect data transmitted by smart medical devices, classroom records stored by teachers, and communications between soldiers. The infographic cites concrete examples of the ways individuals, schools, and military officers routinely use strong encryption to protect sensitive information.
FPF’s infographic highlights the protections provided by strong encryption as well as the risks presented by weakening encryption. Weakened encryption creates risks to health, safety, and privacy, and increases the possibility that criminals will infiltrate systems or intercept data. Encryption can be weakened by unintentional software flaws or by intentional decisions to provide some entities with exceptional access. There is no practical way to distinguish between public sector vs. private sector encryption; government officials typically use the same commercial software and hardware employed by corporations and individuals.