Confidential VMs - a security breakthrough for medical device software
Shawn Dragann
CEO, Idea Evolver
Jerry Valentine
Senior Director, Business Development New Technologies at AstraZeneca
Editor's note: This is a guest blog by Idea Evolver and AstraZeneca
As of June 16, 2022, Confidential VMs are generally available on general purpose N2D machine types and compute optimized C2D VM families. Learn more here.
As of Feb 16, 2023, Confidential GKE Nodes are generally available on general purpose N2D and compute optimized C2D VM families. Learn more here.
Delivering better healthcare is increasingly dependent on technology. Recently, there has been movement towards self-managed healthcare via remote technology – a trend that accelerated during the COVID-19 pandemic. Examples of this are initiatives that directly empower consumers to obtain preventive therapies without a physician’s prescription. AstraZeneca, a global, science-led, biopharmaceutical company, is currently recruiting for the Technology-Assisted Cholesterol Trial in Consumers (TACTiC). TACTiC is a Software as a Medical Device (SaMD) application designed to ensure that only the candidates in the trial with an appropriate level of risk are eligible to access the appropriate medicine.
Two of the most interesting challenges for medical device software products like this are the security requirements and software quality testing mandates. Since the application will process personal health information, care must be taken to ensure the confidentiality of this data. In-memory encryption, also known as confidential computing, is an important security enhancement for this type of application.
Idea Evolver partnered with AstraZeneca to build a medical device software product using Google Cloud products and services. We accepted an early invitation from Google Cloud to take advantage of their Confidential Virtual Machine offering that allows for encryption of data while in use, and couldn’t wait to implement it.
Confidential Computing
A Confidential Virtual Machine (Confidential VM) is a type of N2D Compute Engine VM running on processors using AMD’ Secure Encrypted Virtualization (SEV).
Confidential VMs offer high performance, while keeping memory encrypted with a dedicated per-VM instance key that is generated by hardware and resides solely within the processor. These keys are not accessible by Google and allow customers to keep sensitive code and confidential data secure during processing.
Implementing Confidential VMs is fast and easy
With that in mind, here’s how we at Idea Evolver chose to deploy the Confidential VMs on the AstraZeneca project:
The VMs are part of a node pool used in a GKE cluster
The GKE cluster is regional since we only offer this product in the US, and can thus increase availability
The GKE cluster is private to help ensure confidentiality
We manage our Idea Evolver infrastructure using Terraform, so the implementation was incredibly simple. All we had to do was change our existing cluster definition that used standard nodes and VMs to include the confidential node configuration, specifying that the cluster should use confidential nodes and one of the supported n2d machine types. It was that easy!
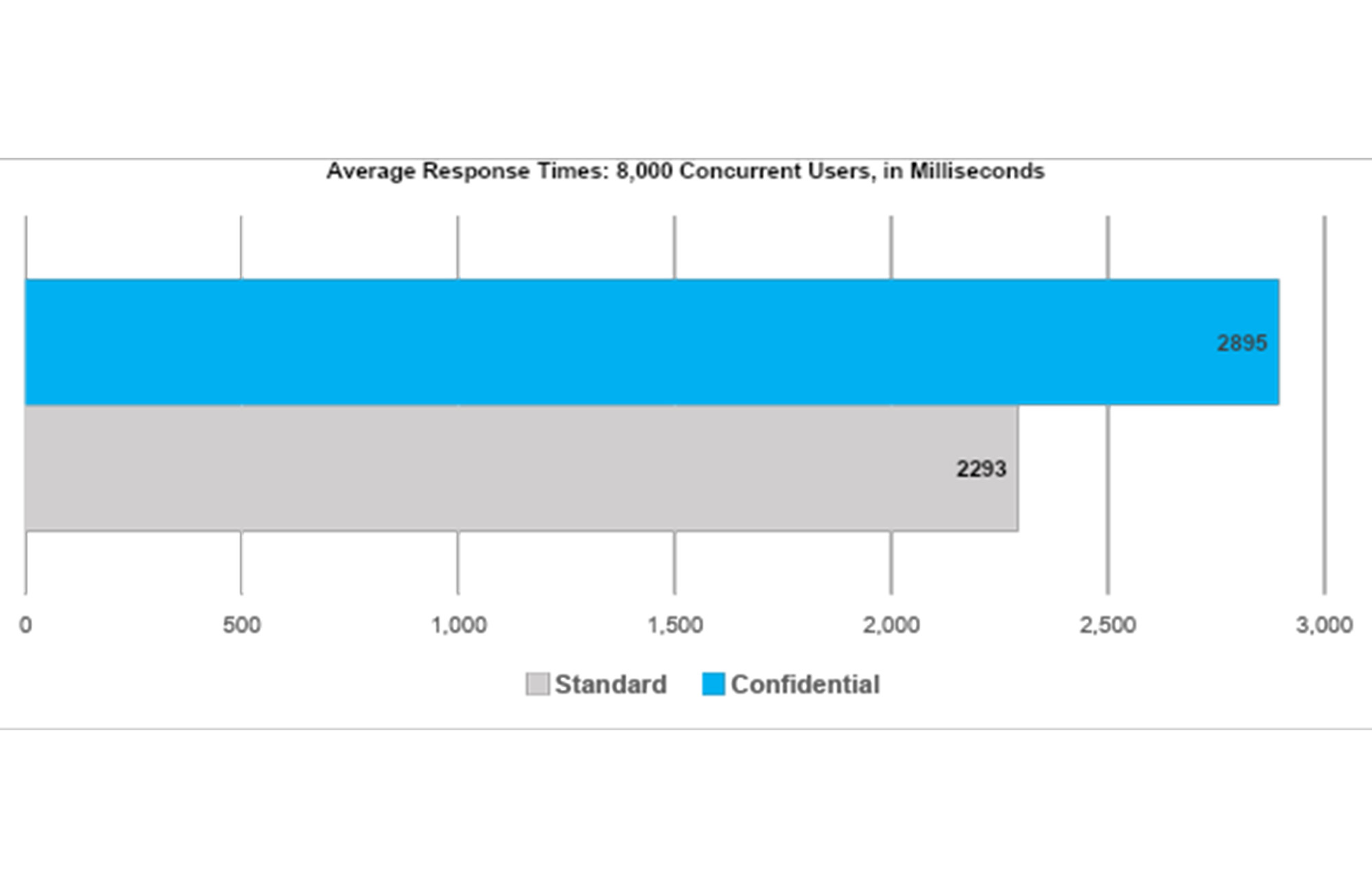
Negligible Performance Degradation
As with any application, performance was important. The confidential VM implementation held up very well during our performance testing and showed almost no degradation in overall performance, despite now being fully encrypted.

Summary and overall value
The overall implementation experience with confidential VMs was faster and easier than expected. The implementation process was straightforward, and the performance results exceeded our expectations.
We all know how important it is to implement every security measure that is reasonably possible, but in the Software as a Medical Device industry, it is that much more important.
Processing data that contains highly confidential and sensitive information in a regulated environment makes implementing confidential VMs an easy decision. In fact, in many ways, it will be transformational for our SaMD projects and the clients we serve. We are now able to offer encryption of sensitive data in transit, at rest, and while in use.
Notes from Google Cloud
You can learn more about Google Cloud’s Confidential Computing options through the following documentation:
To get started creating a new Confidential VM instance, see the Quickstart: Creating a Confidential VM instance guide.
For in-depth instructions see Creating a Confidential VM instance.