Introducing AI-powered investigation in Chronicle Security Operations
Chris Corde
Director Product Management, Google Cloud Security
Spencer Lichtenstein
Product Manager, Chronicle Security Operations
Leveraging recent advances in artificial intelligence (AI) and large language models (LLM), Google Cloud Security AI Workbench sets out to address three of the biggest challenges in cybersecurity: threat overload, toilsome tools, and the talent gap. These could not be more relevant for security operations.
At the RSA Conference 2023 in San Francisco today, we’re excited to announce AI-powered capabilities in Chronicle Security Operations that can transform threat detection, investigation and response for cyber defenders, simplifying complex data analysis and security engineering, and elevating the effectiveness of each defender.
Thoughtful application of generative AI
We know how difficult it is to be the defender. Detecting nuanced signals within ever-increasing volumes of data can be extremely challenging. Chronicle focuses on an outcome-oriented view, designed to provide helpful, actionable intelligence and automation required to help improve your day to day life and tip the advantage back to the defenders.
Working with AI is no different. We believe there is tremendous potential for how AI can supercharge the capabilities of a security analyst, but it needs to be applied in a thoughtful manner. AI needs to be used in the places that require a high degree of specialization or a high degree of manual effort.
Google has been on the forefront of AI research and it can be transformative when it comes to security operations. Recent advances, particularly in large language models (LLMs), have opened up new avenues of practical application for security teams of all sizes and skill levels.
Conversationally search, analyze, and investigate security data
We’re making investigation and response radically simpler and more powerful in Chronicle. AI makes it easier for Chronicle users to interact with and drill down into their security events. Simply enter your question in natural language and Chronicle AI will do the work for you. Chronicle AI can generate the query, present initial information, and make it possible to modify and iterate on your results.
Also, AI can deliver the boost analysts need to speed investigations by providing security insights and trends that pull together and analyze data from these security events, entity insights, and behavior anomalies. Refining and analyzing the data becomes a conversational investigative experience that reduces mean time-to-respond but helps quickly determine the full scope of events. Ultimately, this can help teams better use their resources.


Create detections with AI
Crafting detections can be complex, making it difficult for those without specialized skills to choose the right approach. We have a strong belief in delivering an outcome-oriented platform which handles the detection engineering heavy lifting. We started this journey by launching Curated Detections in Chronicle, and are now going further by giving users the ability to use natural language AI to generate detections. Provide your parameters and let Chronicle write the rule. And don’t stop there, iterate on your creation, apply risk scores and further refine the results.

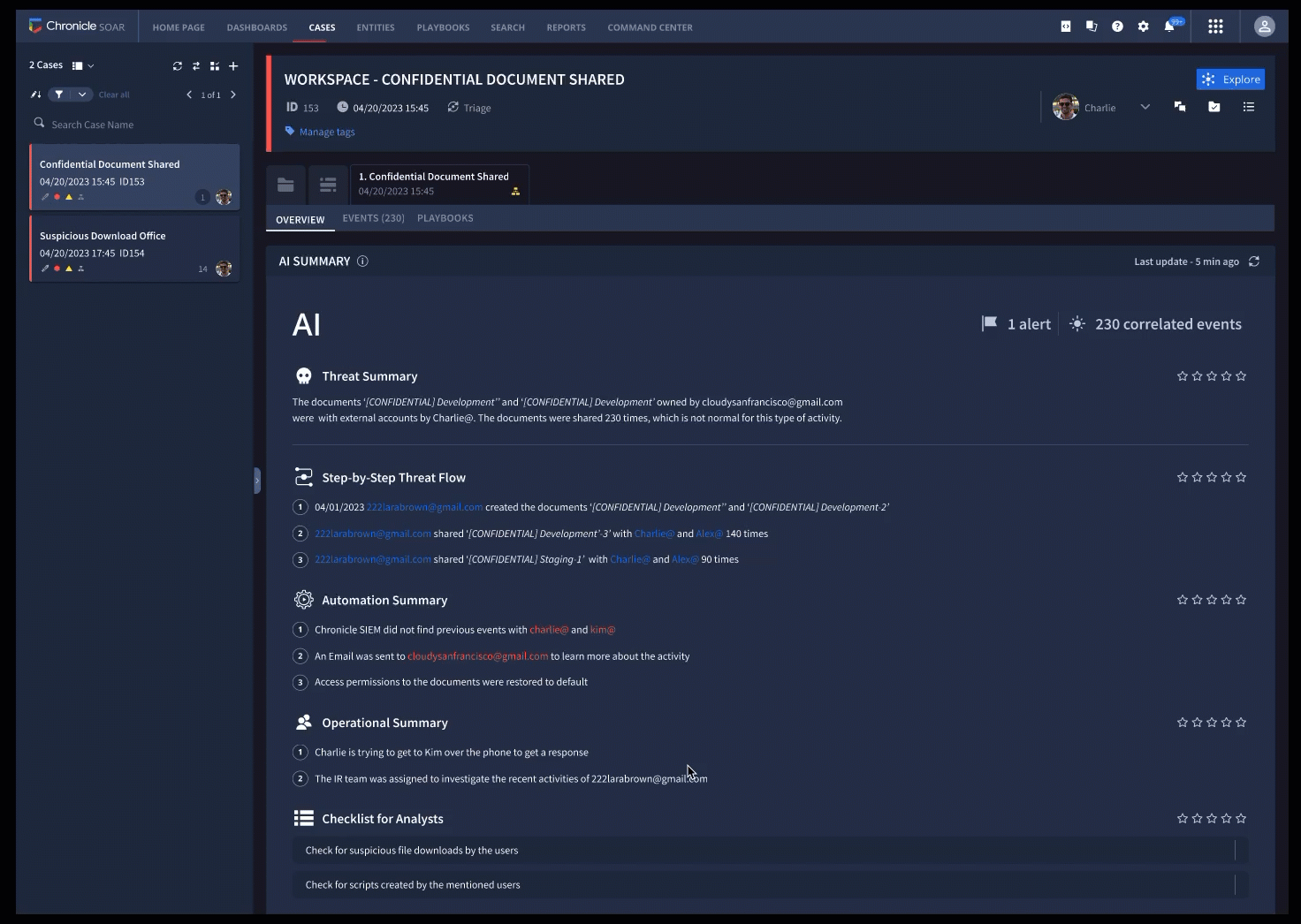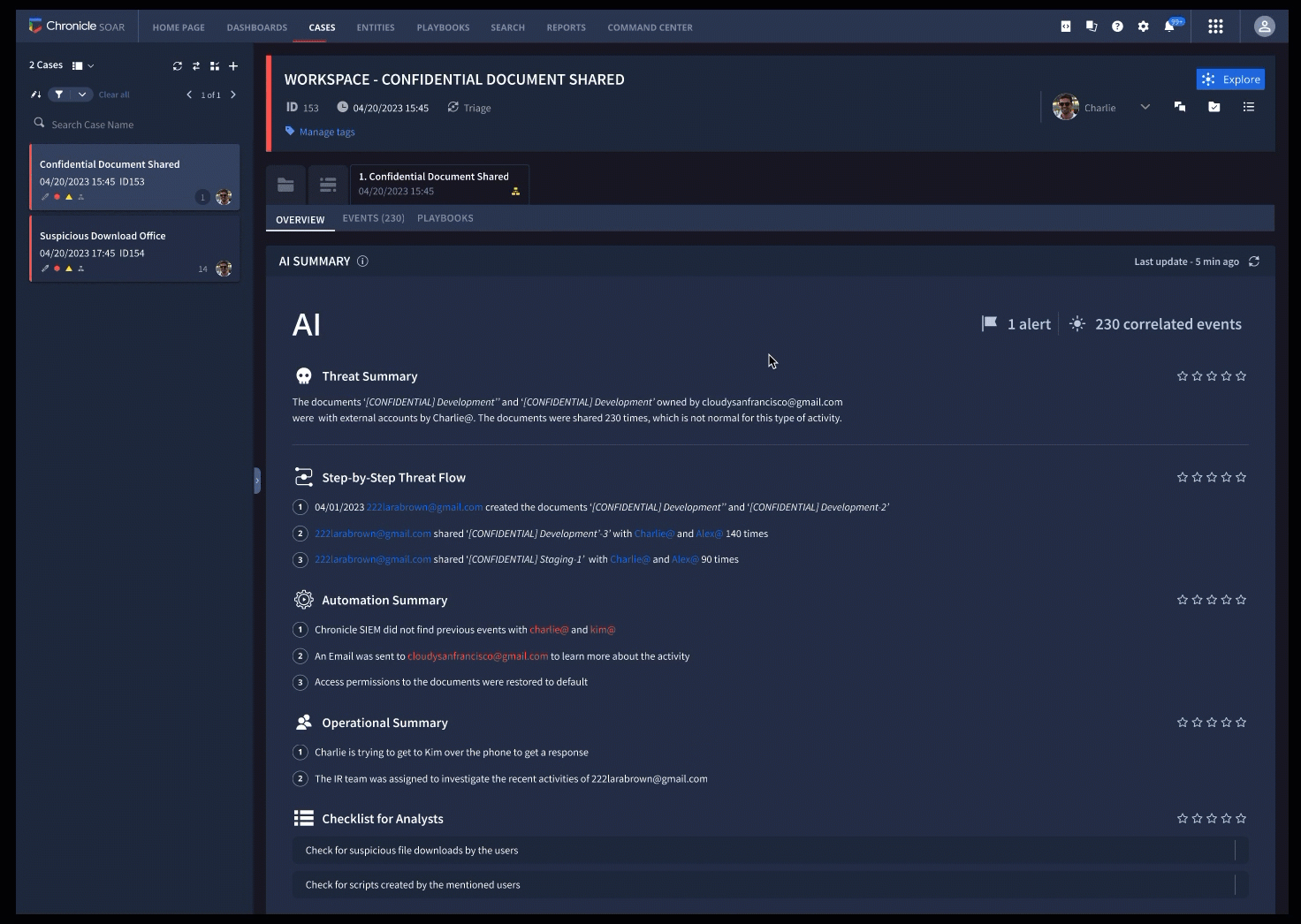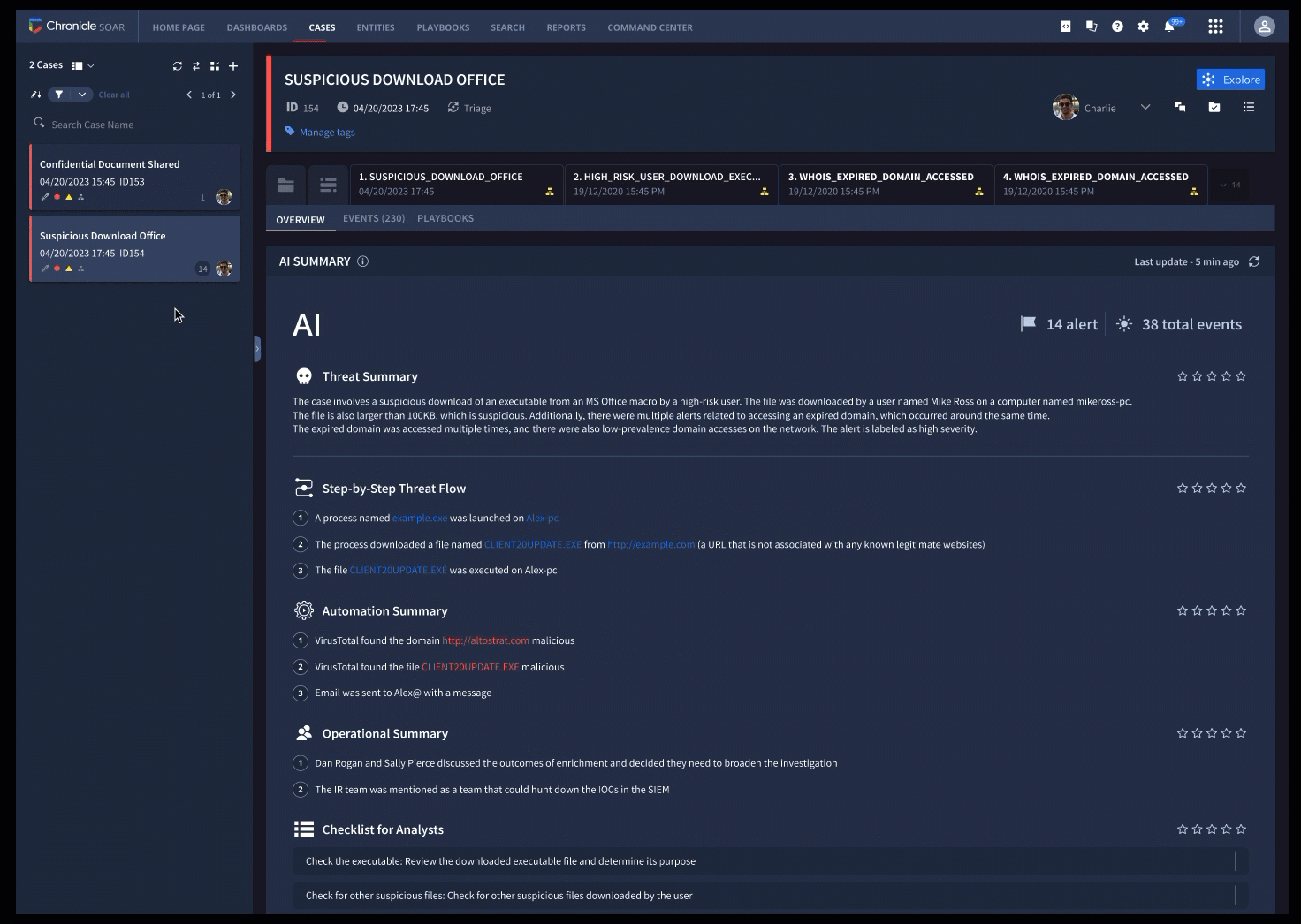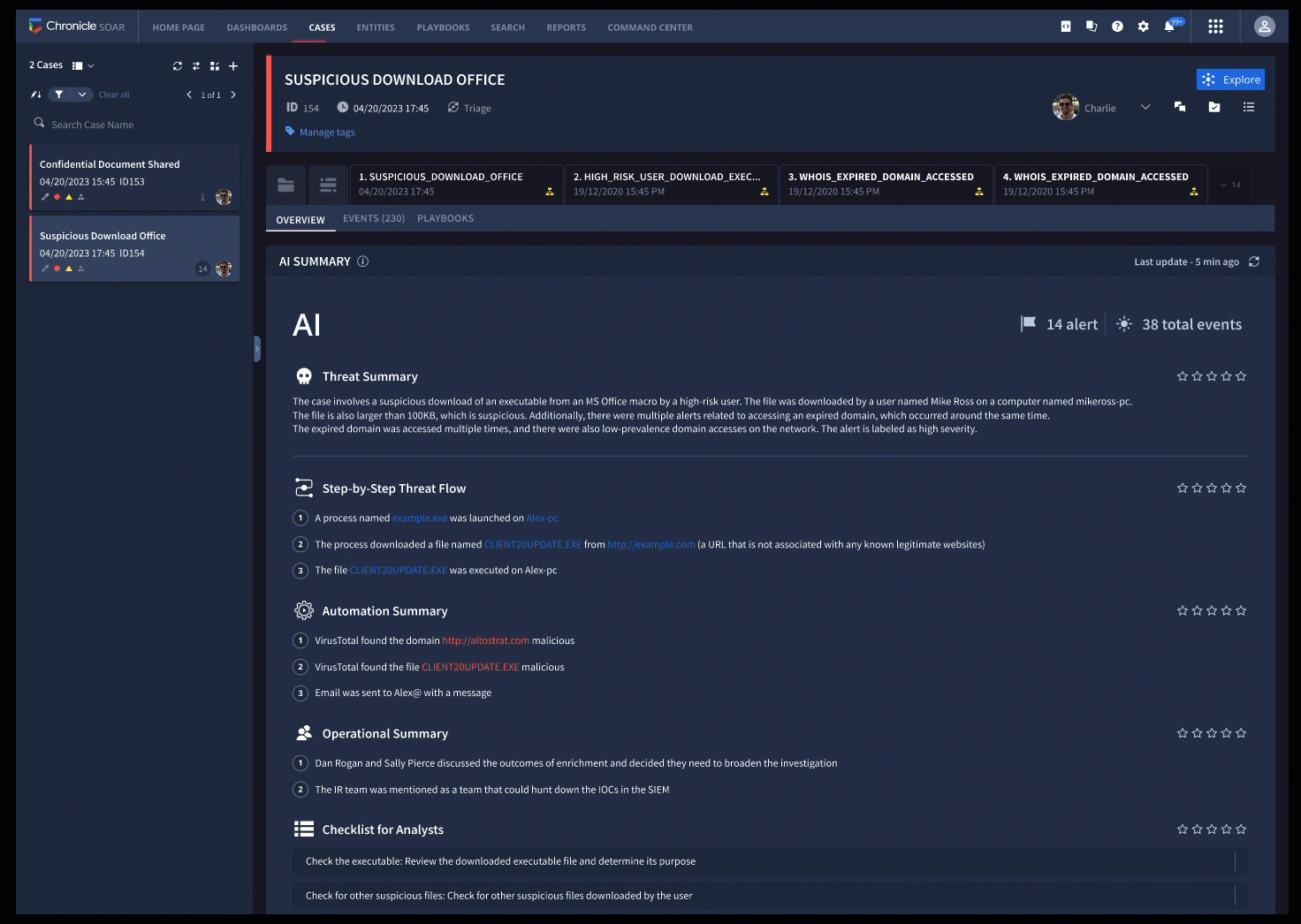
Make better and faster decisions with AI-generated summaries
Security practitioners must quickly understand rapidly changing situations. With AI, Chronicle makes sense of data from cases and investigations for you. A case summary can automatically provide you with a clear look at what’s happening in your case, giving you guidance and interpretation on threats. Iterate on the results to get to the level of detail you need to make informed decisions.

Operationalize frontline intelligence to get ahead of threat actors
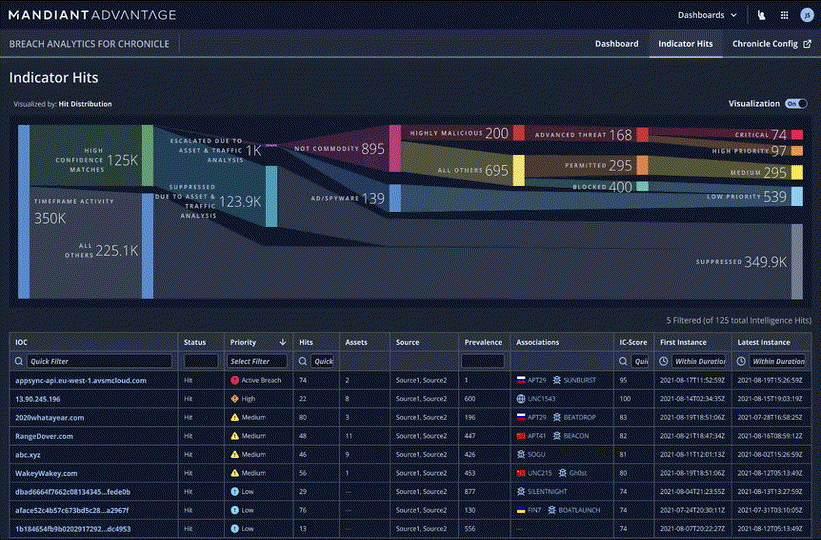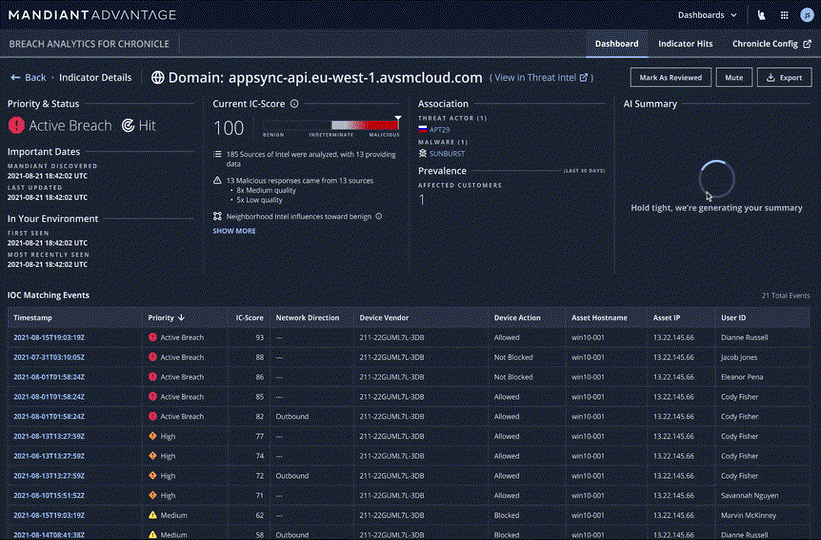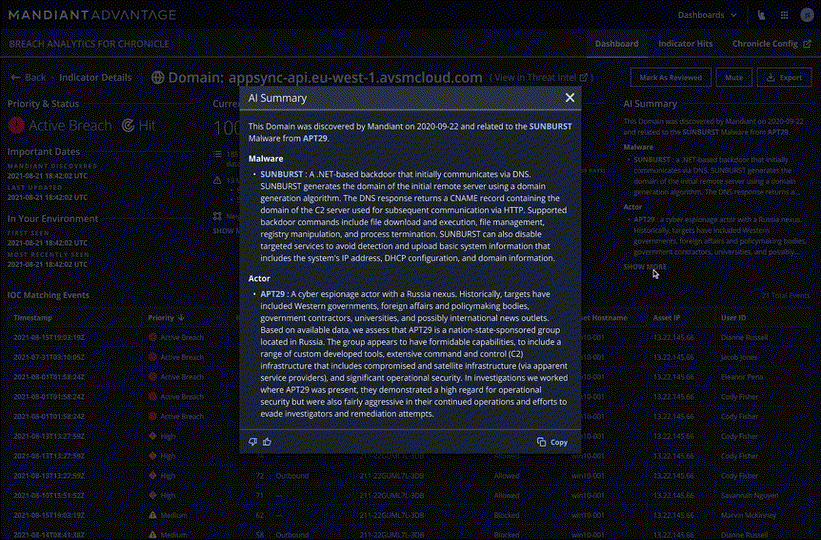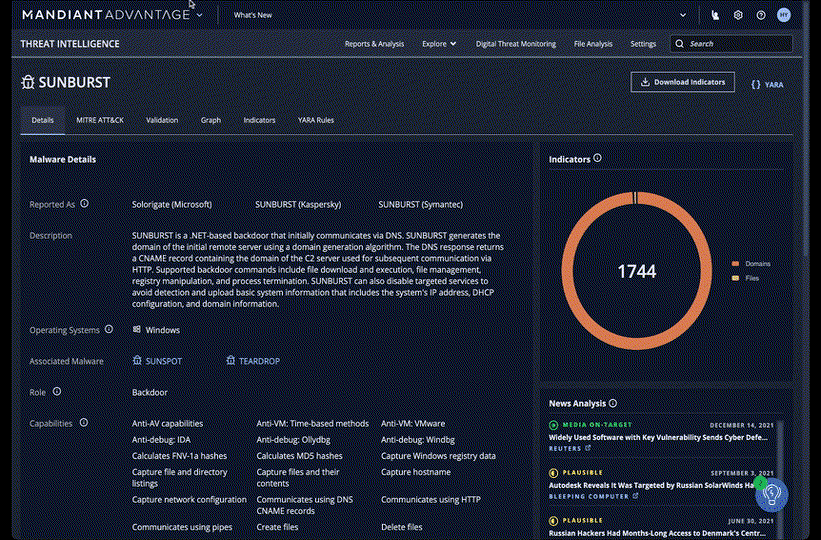
Our ability to apply threat intelligence from Mandiant and VirusTotal to event data in Chronicle can be a powerful way for our customers to detect, track, and combat threats. Using AI based models to curate and prioritize Indicators of Compromise (IOCs) that Mandiant actively tracks, Mandiant Breach Analytics provides a prioritized set of previously-undiscovered events that could be indicative of an active breach.
Mandiant Breach Analytics allows you to readily find and contain bad actors using novel techniques. The AI-based models curate and prioritize the matches to assign an Indicator Confidence Score (IC-Score), which indicates our confidence in their use in malicious activity.
We plan to integrate Breach Analytics into the Chronicle console, giving customers a direct source of alerts and threat actor attribution. The actor attributions are embedded into each Chronicle event, allowing your analysts to augment the out-of-the-box detections with additional context based on the IC-Score and threat actor associations.

What comes next
Later in the year we’ll be introducing the first wave of investigative AI capabilities in Chronicle Security Operations. To learn more about our Security AI, visit us at RSA, booth N6058 or go to cloud.google.com/security/ai.


