Protecting businesses against cyber threats during COVID-19 and beyond
Neil Kumaran
Group Product Manager, Gmail Security & Trust
Sam Lugani
Product Lead, Confidential Computing & Confidential AI
No matter the size of your business, IT teams are facing increased pressure to navigate the challenges of COVID-19. At the same time, some things remain constant: Security is at the top of the priority list, and phishing is still one of the most effective methods that attackers use to compromise accounts and gain access to company data and resources. In fact, bad actors are creating new attacks and scams every day that attempt to take advantage of the fear and uncertainty surrounding the pandemic.
It’s our job to constantly stay ahead of these threats to help you protect your organization. In February, we talked about a new generation of document malware scanners that rely on deep learning to improve our detection capabilities across over 300 billion attachments we scan for malware every week. These capabilities help us maintain a high rate of detection even though 63% of the malicious docs blocked by Gmail are different from day to day.
To further help you defend against these attacks, today we’re highlighting some examples of COVID-19-related phishing and malware threats we’re blocking in Gmail, sharing steps for admins to effectively deal with them, and detailing best practices for users to avoid threats.
The attacks we’re seeing (and blocking)
Every day, Gmail blocks more than 100 million phishing emails. During the last week, we saw 18 million daily malware and phishing emails related to COVID-19. This is in addition to more than 240 million COVID-related daily spam messages. Our ML models have evolved to understand and filter these threats, and we continue to block more than 99.9% of spam, phishing, and malware from reaching our users.The phishing attacks and scams we’re seeing use both fear and financial incentives to create urgency to try to prompt users to respond. Here are some examples:
Impersonating authoritative government organizations like the World Health Organization (WHO) to solicit fraudulent donations or distribute malware. This includes mechanisms to distribute downloadable files that can install backdoors. In addition to blocking these emails, we worked with the WHO to clarify the importance of an accelerated implementation of DMARC (Domain-based Message Authentication, Reporting, and Conformance) and highlighted the necessity of email authentication to improve security. DMARC makes it harder for bad actors to impersonate the who.int domain, thereby preventing malicious emails from reaching the recipient’s inbox, while making sure legitimate communication gets through.
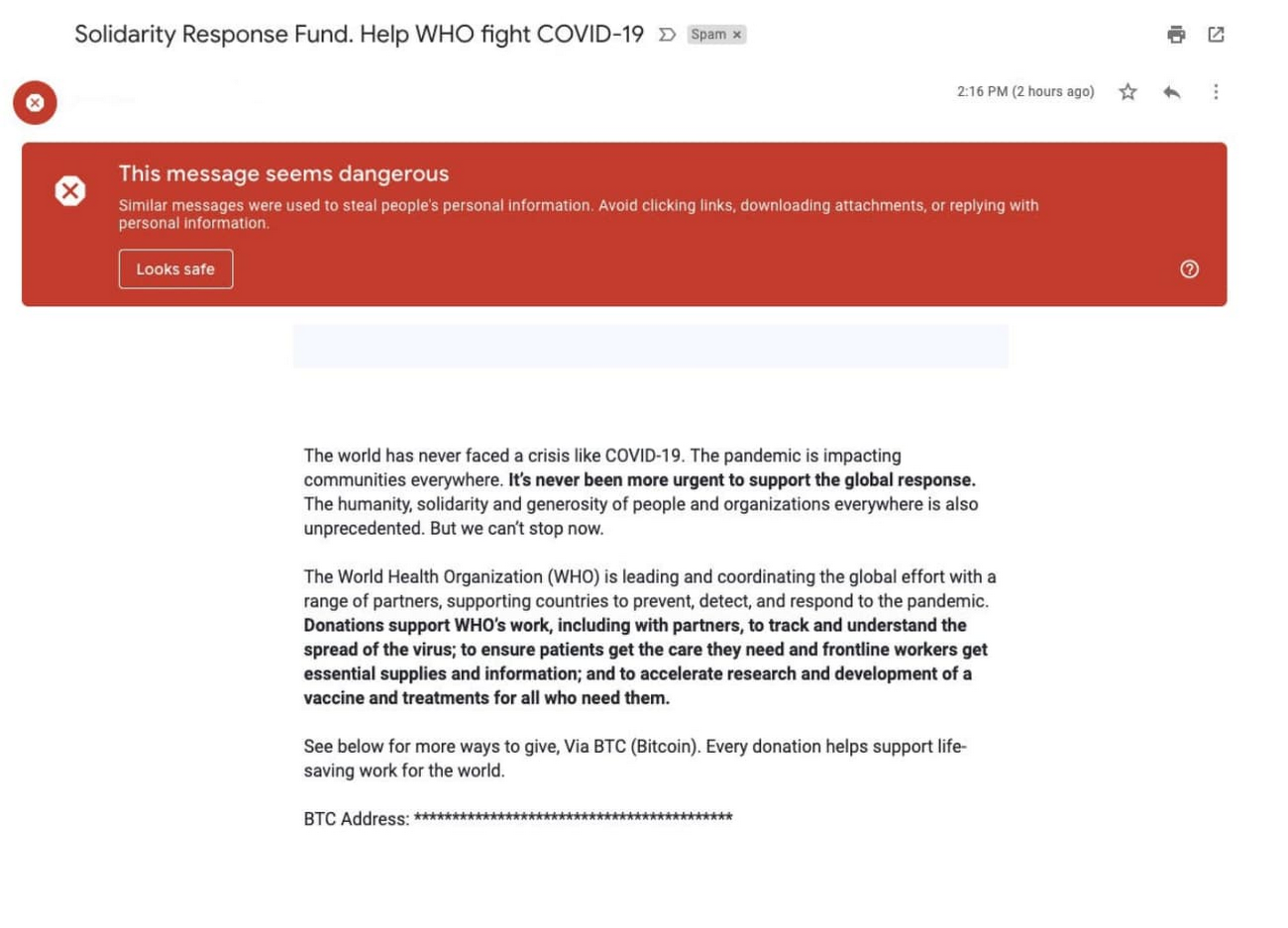

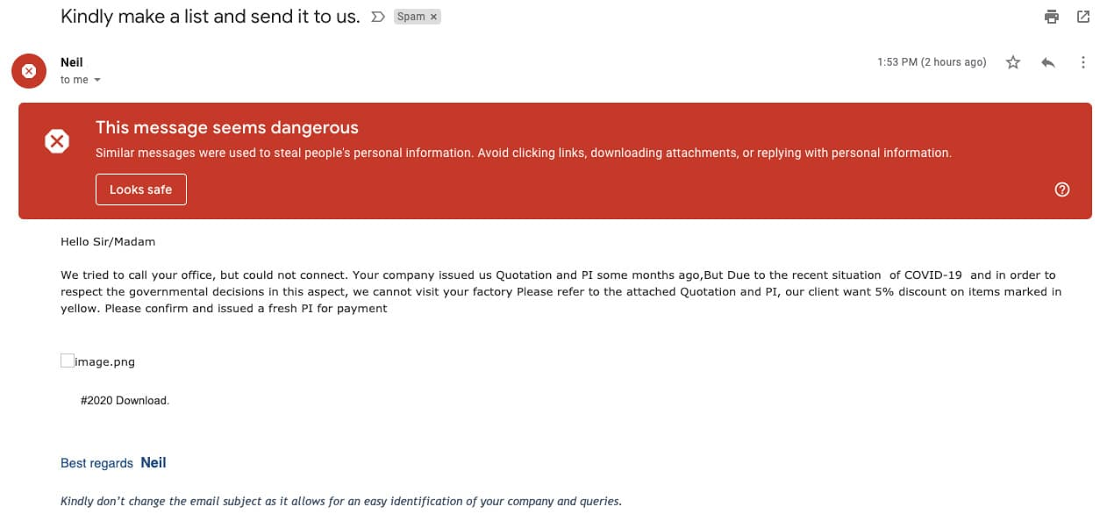
- This example shows increased phishing attempts of employees operating in a work-from-home setting.
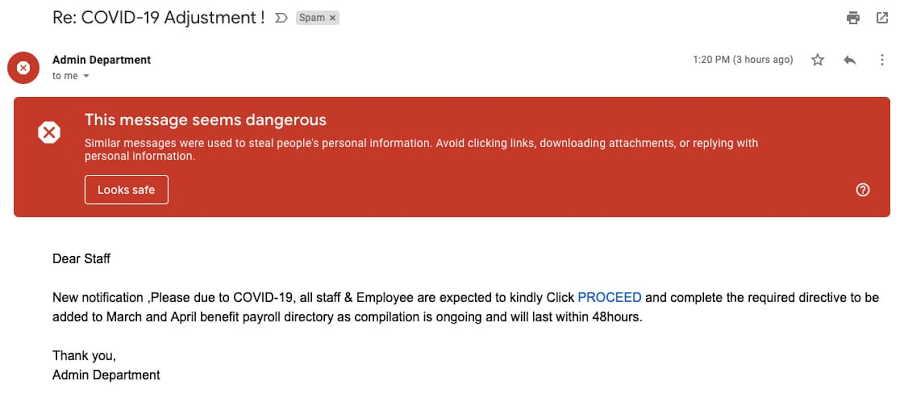

- This example attempts to capitalize on government stimulus packages and imitates government institutions to phish small businesses.
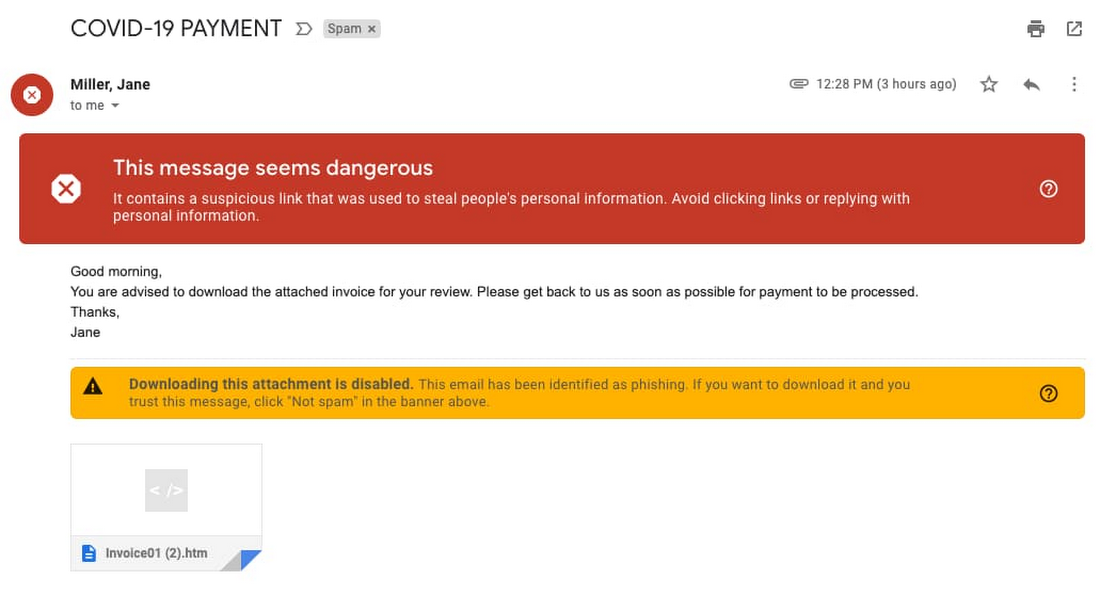

- This attempt targets organizations impacted by stay-at-home orders.

Improving security with proactive capabilities
We have put proactive monitoring in place for COVID-19-related malware and phishing across our systems and workflows. In many cases, these threats are not new—rather, they’re existing malware campaigns that have simply been updated to exploit the heightened attention on COVID-19.As soon as we identify a threat, we add it to the Safe Browsing API, which protects users in Chrome, Gmail, and all other integrated products. Safe Browsing helps protect over four billion devices every day by showing warnings to users when they attempt to navigate to dangerous sites or download dangerous files.
In G Suite, advanced phishing and malware controls are turned on by default, ensuring that all G Suite users automatically have these proactive protections in place.


These controls can:
Route emails that match phishing and malware controls to a new or existing quarantine
Identify emails with unusual attachment types and choose to automatically display a warning banner, send them to spam, or quarantine the messages
Identify unauthenticated emails trying to spoof your domain and automatically display a warning banner, send them to spam, or quarantine the messages
Protect against documents that contain malicious scripts that can harm your devices
Protect against attachment file types that are uncommon for your domain
Scan linked images and identify links behind shortened URLs
Protect against messages where the sender's name is a name in your G Suite directory, but the email isn't from your company domain or domain aliases
Best practices for organizations and users
Admins can look at Google-recommended defenses on our advanced phishing and malware protection page, and may choose to enable the security sandbox.Users should:
Complete a Security Checkup to improve your account security
Avoid downloading files that you don’t recognize; instead, use Gmail’s built-in document preview
Check the integrity of URLs before providing login credentials or clicking a link—fake URLs generally imitate real URLs and include additional words or domains
Avoid and report phishing emails
Consider enrolling in Google’s Advanced Protection Program (APP)—we’ve yet to see anyone that participates in the program be successfully phished, even if they’re repeatedly targeted
At Google Cloud, we’re committed to protecting our customers from security threats of all types. We’ll keep innovating to make our security tools more helpful for users and admins and more difficult for malicious actors to circumvent.