Advancing Autonomic Security Operations: New resources for your modernization journey

Iman Ghanizada
Global Head of Security Operations Solutions, Google Cloud
Anton Chuvakin
Security Advisor, Office of the CISO, Google Cloud
We launched our Autonomic Security Operations solution with a mission to accelerate the world's adoption of more modern threat management strategies. Ultimately, the goal is to shift the industry away from a product-centric approach to detection and response to a more principled approach focused on modernizing your Security Operations workflows, personnel, and underlying technologies to achieve an autonomic state of existence – where your threat management function can scale with your business - and with the threats you face. This effort is grounded in research of Google’s own practices, as well as methodologies like DevOps, SRE, and Agile that have helped to modernize the toil-heavy software development lifecycle (SDLC).
We’re thrilled to highlight our latest initiatives below.
New Solutions
Modernizing the U.S. Federal Government’s Approach to Cyber Threat Management with Autonomic Security Operations – our latest prescriptive guidance offers a path for Public Sector agencies to meet the White House cybersecurity analytics requirements of OMB M-21-31 and Executive Order 14028 with Chronicle, Security Command Center and Siemplify. Read the whitepaper now.
Community Security Analytics – an open-source, community-contributed analytics repository to help Security Operations teams get started with analyzing Google Cloud logs to detect potential threats to your workloads. We’ve partnered with the MITRE Engenuity’s Center for Threat-Informed Defense, Fishtech Group, and a variety of customers to develop a sample set of analytics, mapped to MITRE ATT&CK® TTPs, and kick start the development of the community. Join the collaboration with security researchers now.
Network Telemetry and Monitoring – A blueprint designed to capture network data in Google Cloud using Packet Mirroring, transform the packets into Zeek logs, and store the logs in Cloud Logging, where they can be natively ingested in Chronicle or forwarded to your SIEM of choice. Now available on the Google Cloud Architecture Center.
Research with the MITRE Engenuity’s Center for Threat-Informed Defense
Late last year we joined the Center for Threat-Informed Defense as a Research Sponsor. We’ve sponsored two research initiatives that are currently underway and planned for public release in the coming months.
Mapping Google Cloud security capabilities to the MITRE ATT&CK® framework and ATT&CK® Navigator.
Researching the top Cloud TTPs to help defenders prioritize their development of cloud analytics.
We’re thrilled to continue our research with the Center to help advance our Autonomic Security efforts.
Expanding Partnerships
We’ve expanded to nearly a dozen global partnerships with Global and Regional Systems Integrators (GSI/RSIs), Individual Software Vendors (ISVs), Managed Security Service Providers (MSSPs), Managed Detection and Response Providers (MDR), Research Partners and more. We’re continuing to expand our partners worldwide to support our mission of bringing Autonomic Security to all organizations regardless of where they are on their journey.
With our GSI and RSI partners, we’re collaborating with customers worldwide who run in-house Security Operations programs, helping them structure their transformation journey and partnering with their detection and response teams on the adoption of the ASO approach, the implementation of our Cloud-native technologies, and realizing the strategic vision of their organization’s security operations objectives.
With our MSSP and MDR partners, we're expanding ASO across the most capable organizations, equipping them with our modern technology stack and continuing to raise the bar on the quality of services provided – so our customers can focus on their line of work.
With our ISVs, we’re finding unique areas to partner and provide shared value. After all, most organizations have over 20 security tools in place across their Security Operations function. From developing new integrations, expanding on existing integrations, minimizing operational overhead or finding unique signals to curate – we continue expanding our support of various ISVs on the ASO stack to help organizations realize value faster.
With our research partners, we’re investing in research and development initiatives to help drive the adoption of Autonomic Security as a principled approach to security operations and help organizations get on a path to proactive threat management – regardless of whether they are Google customers or not. We’re continuing to expand on joint research initiatives across the industry.
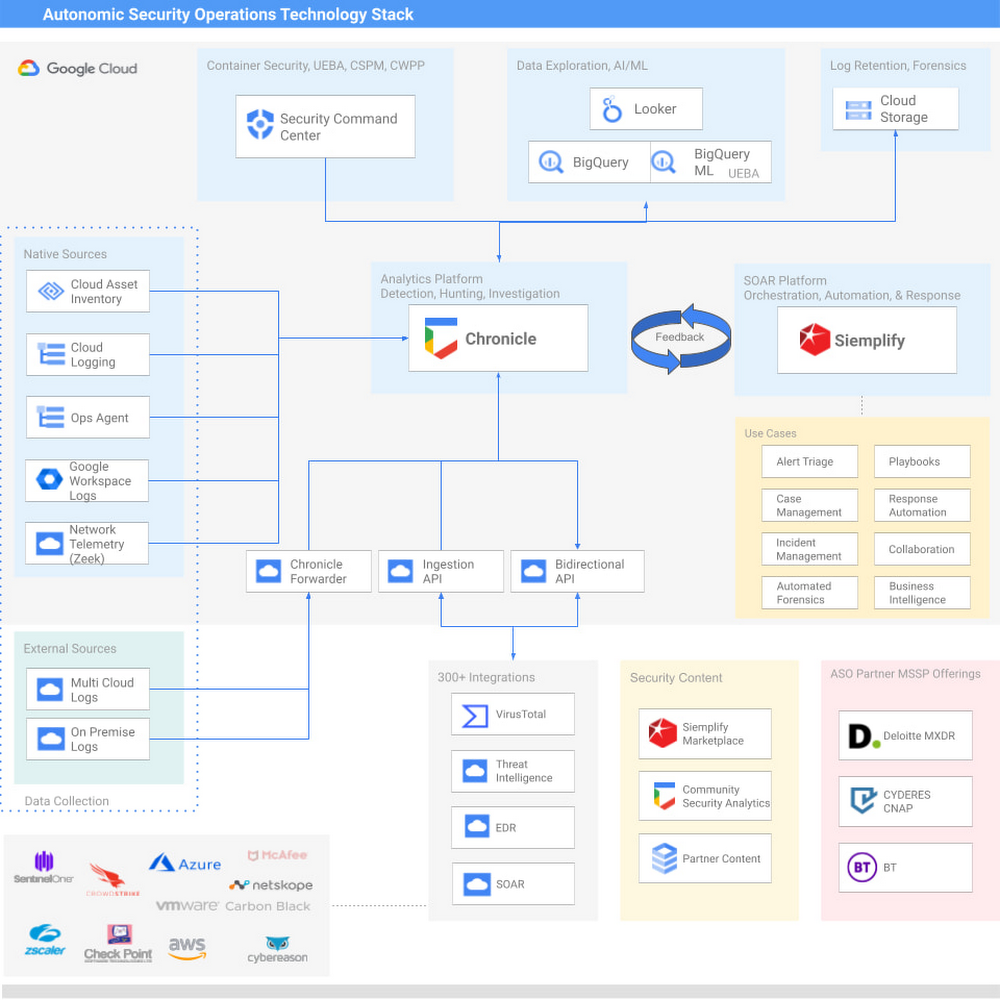
Expansion of our ASO technology stack
We’ve expanded the ASO technology stack to include Siemplify, Security Command Center, VirusTotal, and offer countless integrations with third-party products to take advantage of existing investments that align to the objectives of achieving Autonomic Security Operations. This updated ASO stack is fully modular, cloud-powered, supports multi-cloud workloads across Chronicle and Siemplify, and offers modern detection and response capabilities at a compelling price. Leverage these technologies in accordance with the principled approach of ASO, as we describe in our whitepapers and blog posts at the bottom of this page.

Our Latest Cloud Security Talk – featuring Robert Herjavec!
In our latest Cloud Security Talk today, we were honored to host a dynamic entrepreneur and long-time cybersecurity founder, Robert Herjavec (Founder, Herjavec Group), alongside Eric Foster (President, CYDERES) – where we discussed why all organizations need to pursue Autonomic Security Operations. Stay tuned!
Continuing our mission
We’re looking forward to cross-industry collaboration on advancing the state of threat management and driving towards a future of standardized practices and principles. For Public and Private sector organizations who are looking to get started on their journey of achieving Autonomic Security Operations, contact us to get started today.
Related posts:
“Autonomic Security Operations, 10X Transformation of the Security Operations Center”
“Achieving Autonomic Security Operations: Reducing toil”
“Achieving Autonomic Security Operations: Automation as a Force Multiplier”
“Modernizing SOC ... Introducing Autonomic Security Operations”



