Even the Battlefield: Know More About Your Attack Surface Than the Adversary
Mandiant
Written by: Tim Gallo
Adversaries have a giant attack surface to discover when they target and attack your organization. To defend against these increasingly sophisticated threat actors, organizations must understand their digital footprint better than the adversary. This is easier said than done. It is a big challenge for defenders to know everything going on within the networks they’re charged with defending. Attackers know this and will seek out areas that commonly introduce risk, finding weaknesses to exploit that lead to compromise.
Understanding the full complexities of the attack surface is beyond the scope of a single blog post, so let’s focus in on three components and explore how they introduce risk into an environment:
- Digital Supply Chain
- Merger and Acquisition (M&A)
- Subsidiaries
If videos are more your speed, we hosted a discussion on assessing risk from mergers and acquisitions, subsidiaries and digital supply chain, so be sure to watch the on-demand webinar for more information.
Targeting the Digital Supply Chain
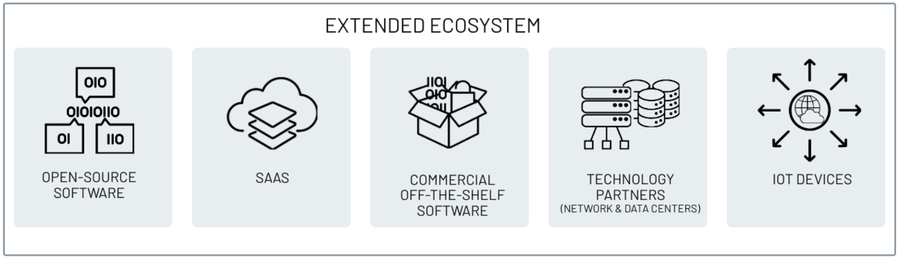

Figure 1: Example categories that make up the digital supply chain
Assessing risk from third-party software includes taking inventory of the technologies leveraged around the organization and evaluating how the software is deployed. Suppose you are following the traditional software deployment model on your own systems. In that case, you need to have a complete understanding of the full number of additional packages and libraries necessary for that software to run. Information technology infrastructure operations (ITIO) often install library dependencies as part of their deployment methodology for the software. However, if your team is actively writing public-facing applications, you now must deal with the Open Source and other third-party libraries introduced as part of said application. This includes database middleware, application plugins, and microservices, web content distribution services, and other items included in the DevOps process. You also need to consider all the network devices themselves sitting out in front of the services you provide. So, you’ll need an accurate understanding of every domain, IP address, and software version exposed to the internet when you think about how an adversary will perform reconnaissance against you.
What about all the open API endpoints you may have for your clients to interact with your service? Those, too, are areas where an adversary may attempt exploitation. Or the GitHub repositories and accounts your dev team uses when publishing software—those also are potential means of adversary recon.
To effectively measure the underlying risk to your business, you need to factor in all the technologies, and their dependencies whether deployed on premises or in the cloud. One would assume that your configuration management database (CMBD) or your vulnerability management tool can handle this; however, both tools provide a point-in-time view, often needing to be updated in the case of CMBDs or, specifically, target known systems in the case of vulnerability management.
Continuous discovery and maintenance of the catalog of software in use sounds simple in theory, but in practice, it is something that has plagued us in the industry for decades. Finding the “unknown unknowns” is something that requires vigilance and repetitive technical tasks evaluating the attack surface of your organization by using all of the information available to your team and expanding upon the knowns through inference or extrapolation. But it shouldn’t stop there. As unknowns become known, they need to be evaluated further for more context and content.
Acquiring Companies, Acquiring Risk
Another thing to consider is the risk posed to your business by the companies you acquire. For example, when you are evaluating another organization for acquisition, questions that are frequently asked by the operations team are: When can they start connecting the newly acquired organization to the network? And, how can we get them access to the resources necessary to work within our larger network? The big factor in determining the ‘when’ and ‘how’ is identifying what risk will be introduced by enabling those connections to the trusted network.
No matter how much information you get up front, things can and will be overlooked. And sometimes, the expected state of the acquired IT infrastructure does not meet the reality. Not to mention the fact that the security team may only have been asked to participate in the security evaluation of the acquisition target once the deal is closed. You’ll need a better way to understand the risk this inclusion will pose and find ways to better demonstrate how to mitigate the risk. Penetration tests conducted by third-party firms are often used during mergers and acquisitions. However, those also are point-in-time assessments and only cover the agreed-upon scope of the penetration test.
Using something like an external attack surface management tool not only complements penetration tests but helps you better identify all of the internet-facing resources that the acquired company has but may not have been included in the initial reporting. From my personal experience, the missing information is not an insignificant amount of elements nor an insignificant amount of risk. Strategically using attack surface discovery tools enable you to perform an external analysis of the company before the acquisition, such as easily finding publicly available information about its internet presence.
Once the acquisition has been completed, you can perform a deeper evaluation of their external and internal infrastructure to uncover the “unknown unknowns” and use this information to create an effective operational plan, including the development and enforcement of technical requirements the acquired organization must meet before getting connected to the larger corporate infrastructure. The operational plan or technical requirements can include things like ensuring they are using corporate GitHub or other code repository management functions, applying patches to internet-facing assets, purging rogue cloud developer accounts, standardizing on specific known third-party libraries, and the like.
Subsidiaries Expand the Attack Surface
Extended portfolio risk applies to organizations that have a series of independent or semi-independent subsidiaries. You need to fully understand the risk to the whole of the conglomerate; however, you may not want to nor have the ability to manage the infrastructure and security controls at each subsidiary. Using a product like Mandiant Advantage Attack Surface Management, you can equip each organization to independently monitor and manage its own attack surface scope, all centralizing visibility for the parent organization. This gives you, at the top of the organizational structure, the ability to see the risk posed by each of the subsidiaries and still allows them to maintain operational independence. In addition, through a series of policy-based enforcements, you can require specific controls and use this to quantify the entire organization's risk.
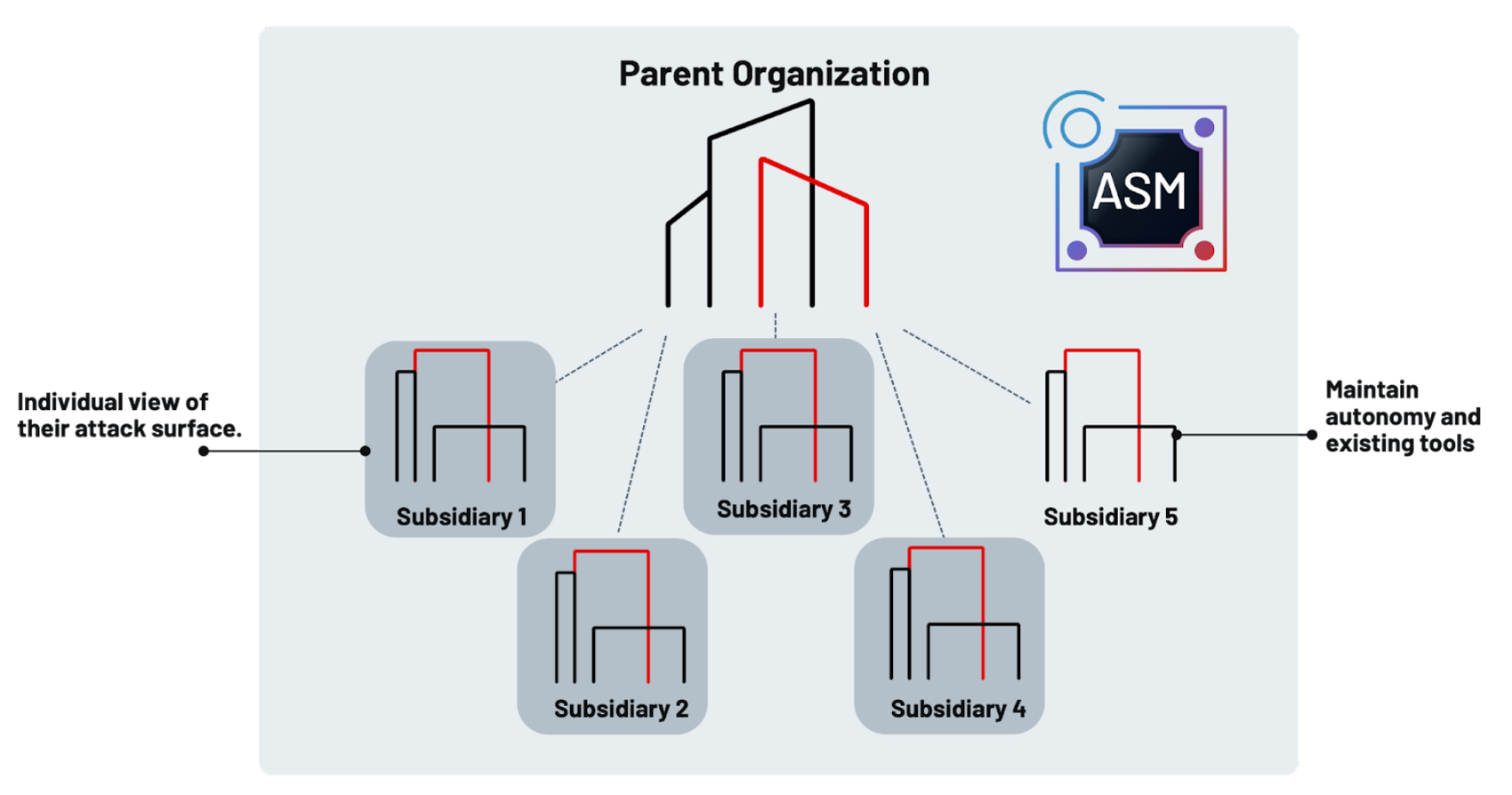

Figure 2: Mandiant Advantage Attack Surface Management centralizes subsidiary monitoring while enabling each subsidiary security team to manage their attack surface autonomously
These are a few scenarios where knowing more about what is happening across your organization can help you to make risk-based decisions when defending your organization. This means there are fewer unknowns and more knowns, which on the whole allows you to create a more secure environment for your employees, partners, and customers. Increased visibility ensures you have your most critical eyes on the resources most likely to be leveraged by an adversary when they attempt to infiltrate your organization. Knowing is half the battle. We need to have continuous rigor and discipline in our efforts to thwart adversaries. Tools such as Mandiant Attack Surface Management help you with not only knowing, but enforcing that continuous discipline to effective analysis of your risk posture, and making the necessary changes to be better at thwarting the adversary.
Identify who’s targeting your organization and what assets are exposed on the internet, get started with Mandiant Advantage Threat Intelligence and Attack Surface Management.