Increasing trust in Google Cloud: visibility, control and automation

Jennifer Lin
Vice President of Product Management, Google Cloud
At Google Cloud, every data center we bring online, network cable we lay, and service we deploy is designed through the prism of security. And we are explicit in our commitment to our Cloud customers: you own your data, and we put you in control.
Today, we are announcing a variety of security tools to further bolster your trust in Google Cloud: to gain increased visibility into your environments, to detect threats, to speed response and remediation, to mitigate data exfiltration risks, to ensure a secure software supply chain, and to strengthen policy compliance. These will help you:
- Gain meaningful oversight over provider operations: Access Transparency (new GA and beta services, GA for G Suite) and Access Approval (beta)
- Prevent data exfiltration and risk: Data Loss Prevention (DLP) user interface (beta) and VPC Service Controls (GA)
- Centralize security management: Cloud Security Command Center (GA) with new Event Threat Detection (beta), Security Health Analytics (alpha), Cloud Security Scanner (new beta integrations) and Stackdriver Incident Response and Management (coming soon to beta)
- View the security status of your APIs: Apigee security reporting (alpha)
- Help secure the software supply chain: Container Registry vulnerability scanning (GA); Binary Authorization (GA); GKE Sandbox (beta); Managed SSL Certificates for GKE (beta); and Shielded VMs (GA)
- Control and protect G Suite data: G Suite data regions enhancements (GA); enhanced advanced phishing and malware protections (beta); Security sandbox (beta); security center and alert center admin collaboration and automation (beta)
- Gain insights with ML: Policy Intelligence (alpha)
- Stay safe on the web: Phishing Protection (beta) and reCAPTCHA Enterprise (beta)
Read on for a whirlwind tour of all the new and improved features and capabilities to help you simplify and streamline your security operations.
Trust through transparency
Running your business in the cloud shouldn’t mean taking a leap of faith. Last year, we announced Access Transparency for GCP, a first-of-its-kind service that creates logs in near-real-time when GCP administrators interact with your data for support. Access Transparency for G Suite is now generally available in G Suite Enterprise, providing visibility into access to covered G Suite data by Google Cloud employees. Within the G Suite Admin Console, we document each access and the reason why, including references to relevant support tickets. As a result, you can verify that Google is accessing your data only for valid business reasons, and you can use this information in support of audits as needed.
Building on Access Transparency, we announced Access Approval for GCP in December, which allows you to explicitly approve access to your data or configurations on GCP before it happens. Access Approval is now available in beta for Google Compute Engine, Google App Engine, Google Cloud Storage, and many other services. This marks the first time a cloud provider has offered controls of this nature that cover all of our employees.
Discover sensitive data and mitigate exfiltration and exposure risks
The first step to protecting sensitive data in the cloud is knowing where it resides. Today, we’re excited to offer enterprises a new way to discover and monitor sensitive data at cloud scale with the Data Loss Prevention (DLP) user interface, now available in beta. Through this new interface, you can run DLP scans with just a few clicks—no code required, and no hardware or VMs to manage. Get started today in the GCP console.
Your first line of defense for cloud deployments is your virtual private cloud (VPC). VPC Service Controls, now generally available, go beyond your VPC and let you define a security perimeter around specific GCP resources such as Cloud Storage buckets, Bigtable instances, and BigQuery datasets to help mitigate data exfiltration risks.
Surface threats to your GCP workloads all in one place
As you move workloads to the cloud, you need visibility into the security state of your GCP resources. You also need to be able to identify threats and vulnerabilities so you can respond quickly.
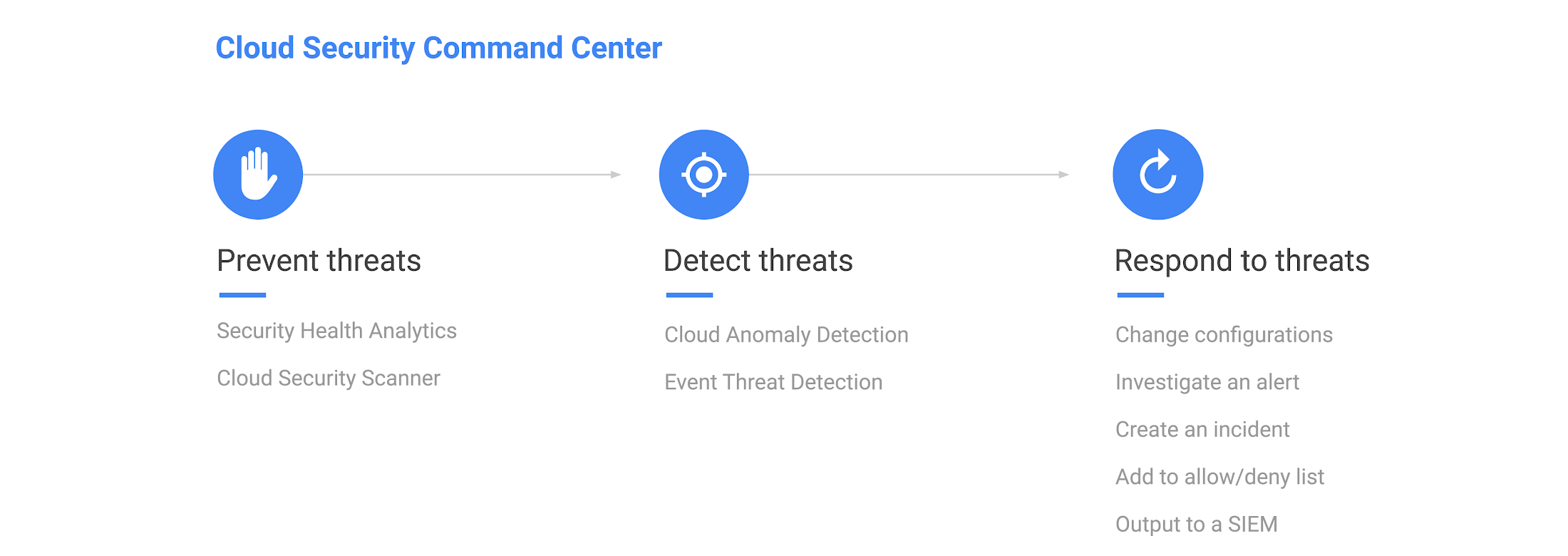
Last year, we introduced Cloud Security Command Center (Cloud SCC), a comprehensive security management and data risk platform for GCP. Cloud SCC is now generally available, offering a single pane of glass to help prevent, detect, and respond to threats across a broad swath of GCP services (App Engine, BigQuery, Cloud Storage, Compute Engine, Google Kubernetes Engine, and more).
As part of GA, we’re excited to announce the first set of prevention, detection, and response services that can help you uncover risky misconfigurations and malicious activity:
- Event Threat Detection leverages Google-proprietary intelligence models to quickly detect damaging threats such as malware, crypto mining, and outgoing DDoS attacks. It scans Stackdriver logs for suspicious activity in your GCP environment, distills findings, and flags them for remediation. Sign up for the beta program.
- Security Health Analytics automatically scans your GCP infrastructure to help surface configuration issues with public storage buckets, open firewall ports, stale encryption keys, deactivated security logging, and much more. Sign up for the alpha program.
- Cloud Security Scanner detects vulnerabilities such as cross-site-scripting (XSS), use of clear-text passwords, and outdated libraries in your GCP applications and displays results in Cloud SCC. Cloud Security Scanner is GA for App Engine and now available in beta for Google Kubernetes Engine (GKE) and Compute Engine.
- Security partner integrations with Capsule8, Cavirin, Chef, McAfee, Redlock, Stackrox, Tenable.io, and Twistlock consolidate findings and speed up response. Get started by viewing our partners on GCP Marketplace.
Cloud SCC also helps you respond to threats. You can work to remediate findings by exporting incidents to the SIEM of your choice or open and track an incident in the new Stackdriver Incident Response and Management tool, coming soon to beta.

Gain insights into the security status of your APIs
APIs exposed to developers inside and outside your organization are another target for attackers. Apigee, Google Cloud’s API management platform, includes new security reporting to help you gain a holistic view of the health and security status of your API programs. You can identify APIs that do not adhere to security protocols and user groups that are publishing the most sensitive APIs. Findings are accessible in the Apigee console and via API for integration with SIEM tools. Apigee API security reporting is in alpha. Learn more
https://cloud.google.com/apigee/api-management/secure-apis/
.Security throughout the software supply chain
With containers, you need to trust the images you are running. Today, we’re announcing the availability of several GKE services to help build confidence in your containerized software supply chain.
Finding vulnerabilities early in the deployment cycle avoids patching fire drills later on. Container Registry, our secure, private Docker registry, includes vulnerability scanning, a native integration for GKE that identifies package vulnerabilities for Ubuntu, Debian, and Alpine Linux, so you can find vulnerabilities before your containers are deployed. Originally announced in September, Container Registry vulnerability scanning will soon be generally available.
Before a container is deployed to a GKE cluster, you want to make sure it meets your organization’s deployment requirements. Binary Authorization is a deploy-time security control that integrates with your CI/CD system, gating images that do not meet your requirements from being deployed. In the forthcoming GA release, Binary Authorization can be integrated with Cloud Key Management Service and Cloud SCC, delivering deploy-time control that you can view from the same console that you use to manage other security operations.
Even when you’re working off a known-good foundation, sometimes you want an extra level of security. Coming soon to beta is GKE Sandbox, based on the open-source gVisor project. GKE Sandbox provides additional isolation for multi-tenant workloads, helping to prevent container escapes, and increasing workload security.
GKE also now offers Managed SSL certificates, giving you full lifecycle management (provisioning, deployment, renewal and deletion) of your GKE ingress certificates. Now in beta, Managed SSL certificates make it easier to deploy, manage and operate secure GKE-based applications at scale.
Finally, to harden VM-based workloads, Google Cloud offers Shielded VM, which provides verifiable integrity of your Compute Engine VM instances so you can be confident they haven't been compromised. Already, more than 21,000 Shielded VM instances are deployed on GCP, and starting today, Shielded VM is generally available, giving you a simple way to reduce the likelihood that anyone can tamper with your VMs.
Controlling and protecting G Suite data
We're also announcing new ways to help you protect, control, and remediate threats to the business data you create and store in G Suite.
Some organizations require their data to be stored in specific locations, and we’re committed to meeting that need. G Suite Business and Enterprise customers can designate the region in which covered data at rest is stored—globally, in the US, or in Europe. We’re enhancing data regions with coverage for backups.
We’re introducing new (beta) controls for advanced phishing and malware protection. These controls can help admins protect against anomalous attachments and inbound emails spoofing your domain in Google Groups. The security sandbox (available in beta for G Suite enterprise customers) helps provide better protection against ransomware, sophisticated malware and zero-day threats by executing email attachments in a sandbox environment to find out if they are malicious.
Security center and alert center for G Suite provide organizations with best practice recommendations, unified notifications and integrated remediation that help admins take action against threats. We want to help admins work collaboratively to assess their organization’s exposure to security issues. New beta functionality allows admins to save and share their investigations in the security investigation tool. Within the alert center beta, admins can now indicate alert status and severity and assign alerts to other admins. Admins can also create rules within the security center that perform automated actions or send notifications to the alert center, where teams of admins and analysts can work together to take ownership and update status as they work through security investigations. Sign up for the security center beta here and alert center beta here.
Putting it all together with ML
Keeping configurations in-step with your security policies can be a challenge. There are a lot of levers to pull and settings to tweak to get security right, and you may wonder if you’ve done everything you can to reduce your exposure. To help, today we’re unveiling Policy Intelligence. Initially available for Cloud IAM, Policy Intelligence offers three new tools to help you understand and manage your policies and reduce risk:
- IAM Recommender helps admins remove unwanted access to GCP resources using machine learning to make smart access control recommendations.
- Access Troubleshooter enables security administrators to understand why requests were denied and helps modify policies to grant the appropriate access.
- Validator lets admins set up governance and security guardrails that prevent them from granting overly-permissive access.
To get started, sign up for the Policy Intelligence alpha program.
New services to keep your users safe on the web
To protect your business, you need to protect your users. Last month at RSA Conference, we announced the beta of our Web Risk API and now we’re excited to introduce two brand new Google Cloud user protection services:
- Phishing protection. Phishing websites that use things like your name and logo put your users at risk and damage your business. With the Phishing Protection service, you can quickly report unsafe URLs to Google Safe Browsing and view status in Cloud SCC. Once URLs are populated into Safe Browsing lists, users on more than three billion devices will be warned before they click on infected links. Sign up for the beta.
- reCAPTCHA Enterprise. Security teams need to keep bad actors out of their websites, and ensure that their customers can always get in. reCAPTCHA has been defending millions of sites for almost a decade, and our new reCAPTCHA Enterprise service builds on this technology with capabilities designed specifically to address enterprise security needs. You can defend your website against fraudulent activity like scraping, credential stuffing, and automated account creation and help prevent costly exploits from automated software. Sign up for the beta.
Creating environments that are secure—and keeping them that way—is job number one for organizations that run in the cloud. At Google Cloud, we’re committed to ensuring advanced security is an enabler for businesses who need greater agility with improved governance. Visit Google Cloud Security for a complete overview of Google Cloud infrastructure, products, and transparency and trust policies. And be sure to read our identity and access management blog post about new ways to help you improve IT, developer, and end-user efficiency.


