Improve your security posture with new Overly Permissive Firewall Rule Insights
Tracy Jiang
Product Manager
Try Google Cloud
Start building on Google Cloud with $300 in free credits and 20+ always free products.
Free trialAre you a network security engineer managing large shared VPCs with many projects and applications deployed, and struggling to clean up hundreds of firewall rules accumulated overtime in the VPC firewall rule set?
Are you a network admin setting up open firewall rules to accelerate cloud migration, but later struggling to close them down without worrying about causing outages?
Are you a security admin trying to get a realistic assessment of the quality of your firewall rule configuration, and to evaluate and improve your security posture?
If the answer to any of the questions above is a “Yes”, you’ve come to the right place!
Firewall Insights and What’s New?
In a previous blog post, we introduced the new tool Firewall Insights that provides visibility to firewall rule usage metrics and automatic analysis on firewall rule misconfigurations. Today we would like to introduce a new module within Firewall Insights called “Overly Permissive Firewall Rule Insights”.
Overly permissive firewall rules have been a major issue for many of our customers, both during cloud migration as well as the subsequent operational phase. In the past, some customers have attempted to address this pain point by writing their own scripts or manually reviewing large volumes of firewall rules to detect the problem. The results have not been successful.
With the “Overly Permissive Firewall Rule Insights”, customers can now rely on GCP to automatically analyze massive amounts of firewall logs and generate easy-to-understand insights and recommendations to help them optimize their firewall configurations and improve their network security posture.
Overly Permissive Firewall Rule Insights
The type of insights and recommendations that can be generated through the Overly Permissive Firewall Rule analysis include the following:
Unused firewall rules
Unused firewall rule attributes, such as IP ranges, port ranges, tags, service accounts, etc
Open IP and port ranges that are unnecessarily wide
In addition, using machine learning algorithms, the Firewall Insights engine can also look for similar firewall rules in the same organization and use its historical usage data to make predictions on the future usage for those unused rules and attributes, so that users could have additional datapoint to help them make better decisions during firewall rule optimization.
Now let’s take a look at how you can generate these insights for your projects.
Enable and configure the Overly Permissive Firewall Rule Insights
First you will need to enable the “Overly Permissive Rule Insights” module on the Firewall Insights page - Configuration:
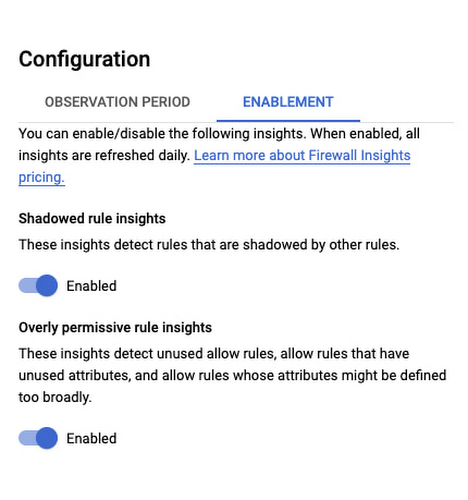

Once enabled, the system will start scanning the firewall logs for the project during the “Observation Window” and generate insight updates on a daily basis.
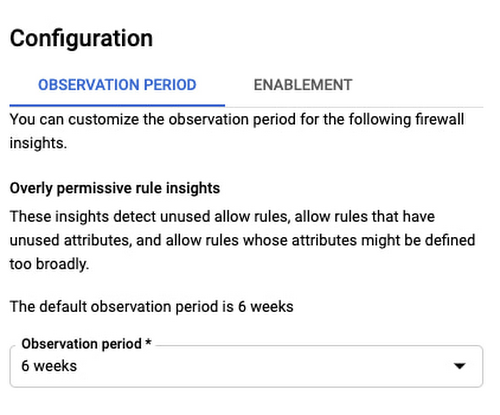
The default observation window for this analysis is 6 weeks, but you adjust it based on your traffic pattern by doing it in the “Observation Period” configuration tab:

Discover unused allow rules and attributes to clean up
If you are like most of the network and security admins working with complex cloud networks, you probably have accumulated a set of firewall rules that you know are not optimally configured, but don’t know where to start to clean them up.
With the Overly Permissive Firewall Rule Insights, you can rely on GCP to help give you the answer. Once you enable this module and firewall logging for the target project, the system will analyze all network logs to reveal the traffic pattern that is going through the firewall rules.
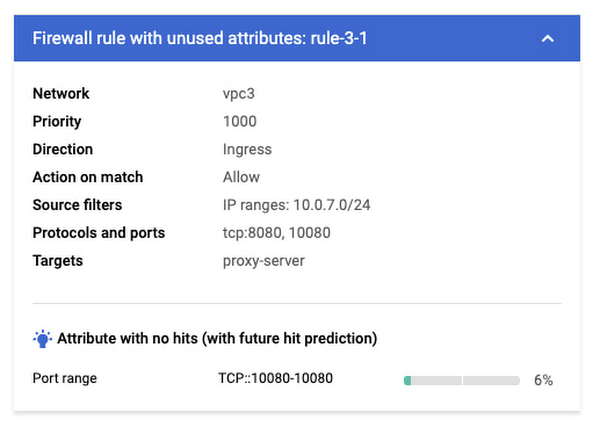
Firewall Rule Insights will automatically generate a list of allowed rules that has no hit, or specific IPs, ports or tags configured in an allow rule that did not have any hit, so you can focus your investigation on this group of rules and attributes for cleanup.
Meanwhile, the system will also look at the firewall rules similarly configured in your organization and their hit pattern to make a prediction whether or not the unused rules and attributes are likely to be hit in the near future, so that you can use this information as a reference to decide whether it is safe to remove a rule or attribute from your firewall rule configuration.
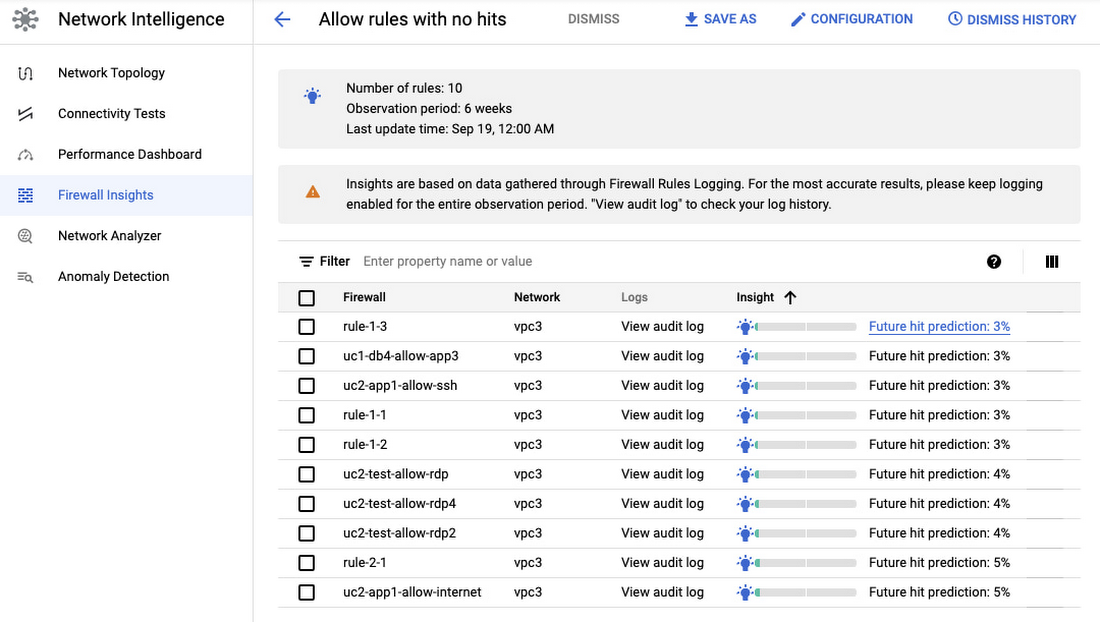

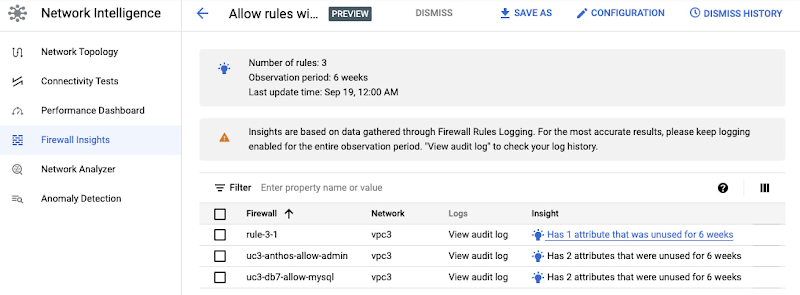


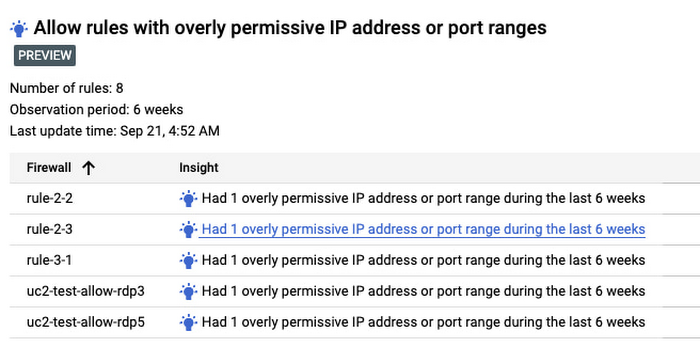
Get recommendations on how to minimize permitted IP & port ranges
Sometimes when you are in a hurry to get application connectivity established, you may open an overly wide IP or port range on your firewall thinking you will close that down later, but never really do it properly. This is a common problem that many network and security admins run into. A typical scenario where such a thing happens is during the cloud migration. If this is an issue you are struggling with, now you have a solution with the Overly Permissive Firewall Rule Insights.
With Overly Permissive Firewall Rule Insights, customer can rely on GCP to automatically scan the firewall logs for a VPC network, analyze its firewall rules and the patterns of the traffic coming in and out of this network, identify these overly permissive IP and port ranges in the allow rules, and make recommendations on how to replace these wide ranges with smaller ranges to close down portions in those ranges that are not needed for legitimate traffic.

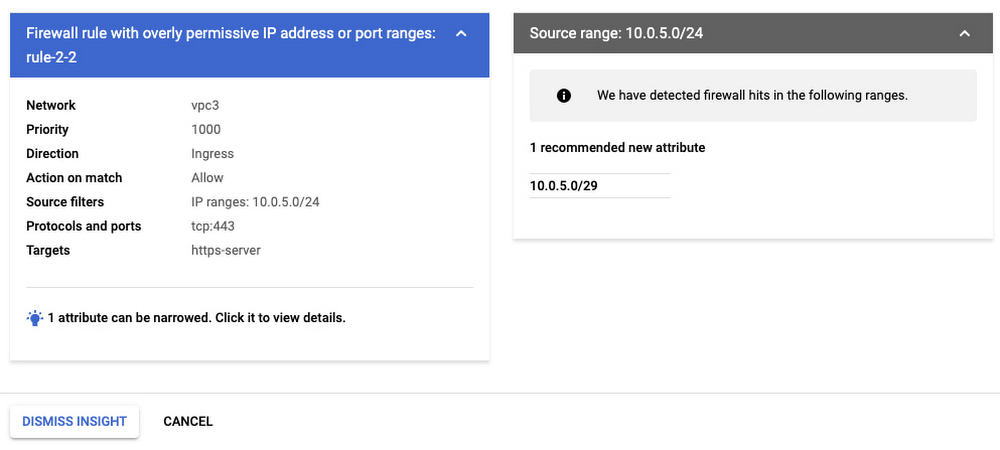

To ensure this function works properly and make accurate recommendations, you will need to enable firewall logging for all rules you are looking to optimize because the engine relies on Firewall Log as its data source for the analysis. The insights are updated on a daily basis based on incremental analysis done on new log entries processed for that day.
For more information on the Firewall Insights product, please refer to our public documentation.




