Take charge of your OAuth ecosystem with these best practices
Reena Nadkarni
Group Product Manager, G Suite, G Suite
Use this refresher to manage your OAuth ecosystem.
Contact Google Workspace Sales Team
Learn more about how Google Workspace can give your teams a better way to connect, create, and collaborate.
CONTACT USProtecting your organization’s most sensitive data and assets is a constant effort. G Suite provides IT admins with full visibility and comprehensive controls to manage application access by vendors outside of Google to your domain’s data stored in Gmail, Drive or other G Suite apps. Here’s a refresher on how you can take charge.
1. Re-evaluate apps that have been granted domain-wide API access
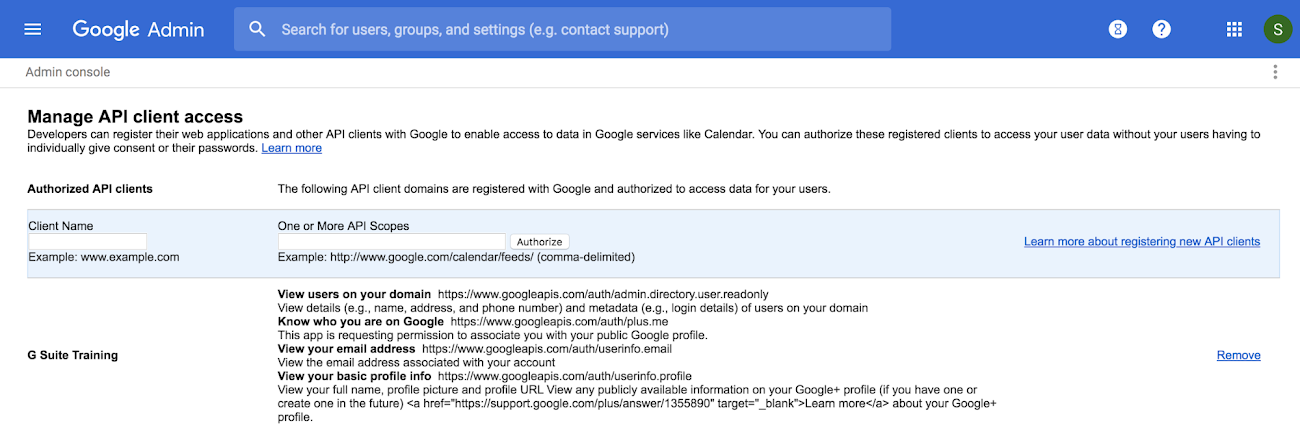
Developers must register their web applications and other API clients with Google to enable access to data in G Suite apps like Google Calendar. You authorize these registered apps to access user data within your domain from the Admin console. To strengthen your organization’s security posture, re-evaluate current access via the Admin console and revoke permissions if app access is no longer needed.

2. Enforce OAuth apps whitelisting
Speaking of, OAuth apps whitelisting gives IT admins the ability to control which third-party apps are allowed to access users’ G Suite data. This helps ensure that users can only grant permission to applications that are trusted by the administrator. Once the OAuth whitelisting settings are in place, access to third-party apps is enforced based on this policy and employees are automatically protected against unauthorized apps.
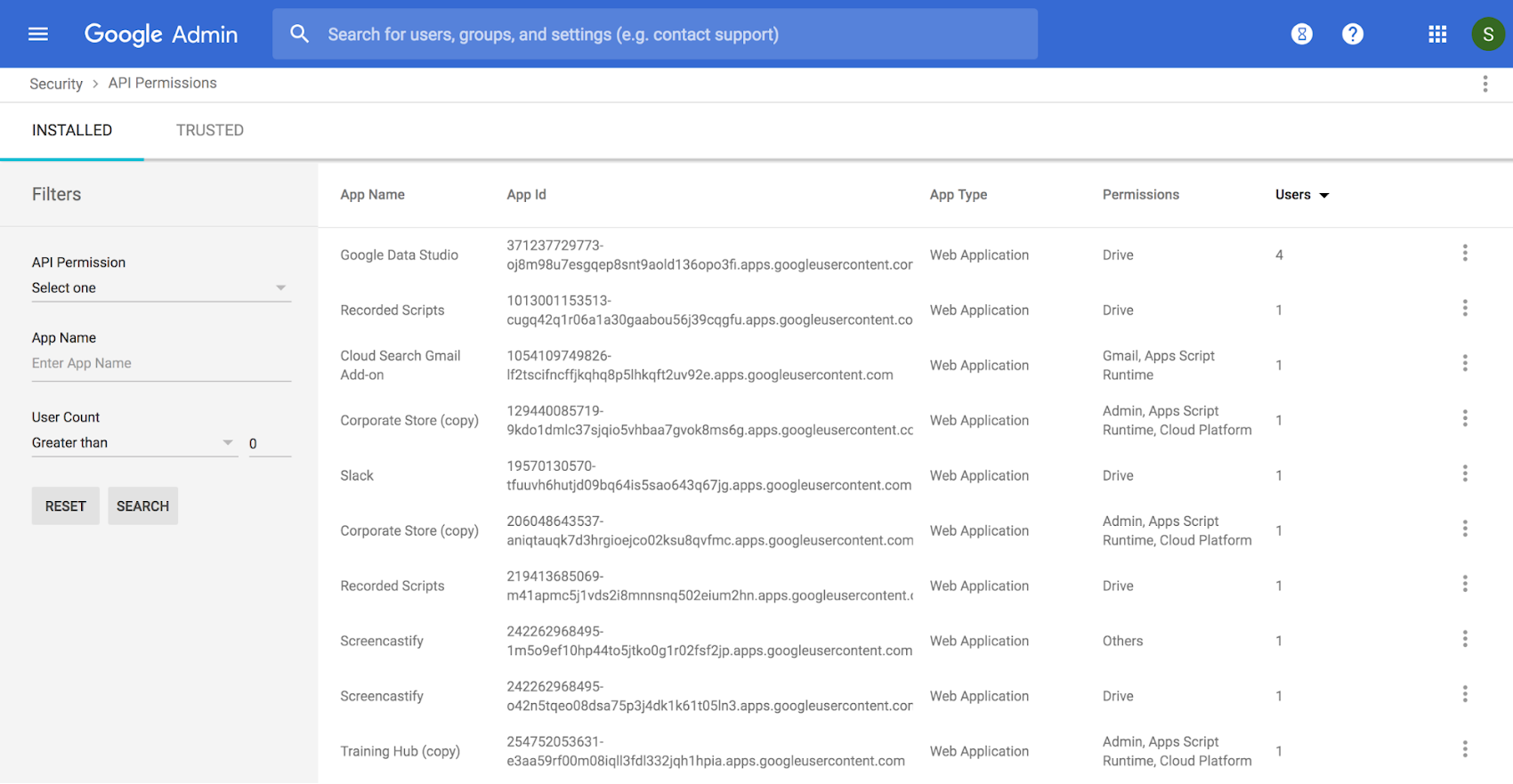

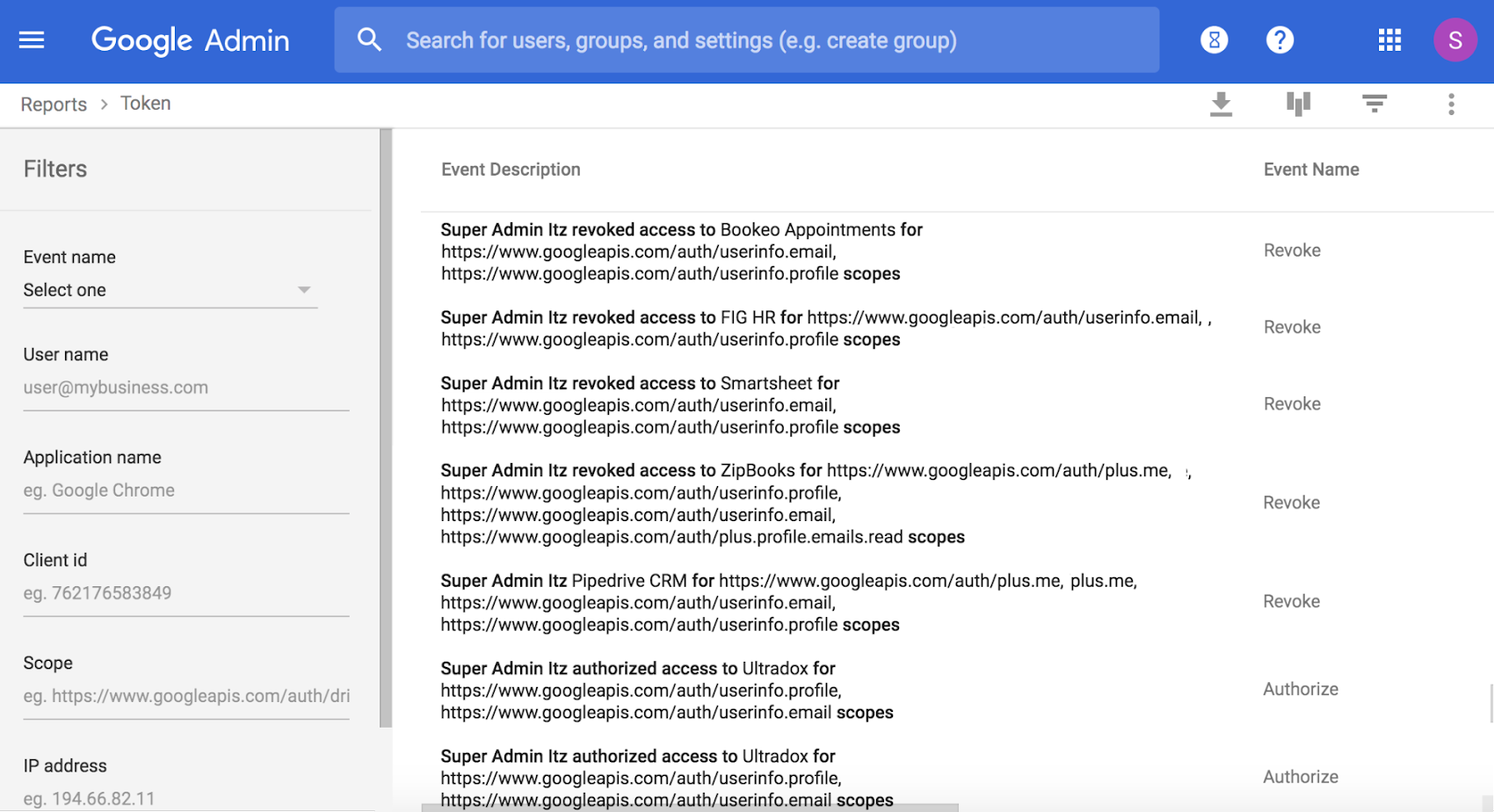
3. Examine user specific 3rd-party application usage
Use the OAuth Token audit log to understand which users are using which third-party mobile or web applications that are connected to G Suite in your domain. The audit log records the name of the app, the user, and the APIs it accesses when an app is granted access. Visibility into third-party data access can help you make informed decisions about limiting access to specific apps.

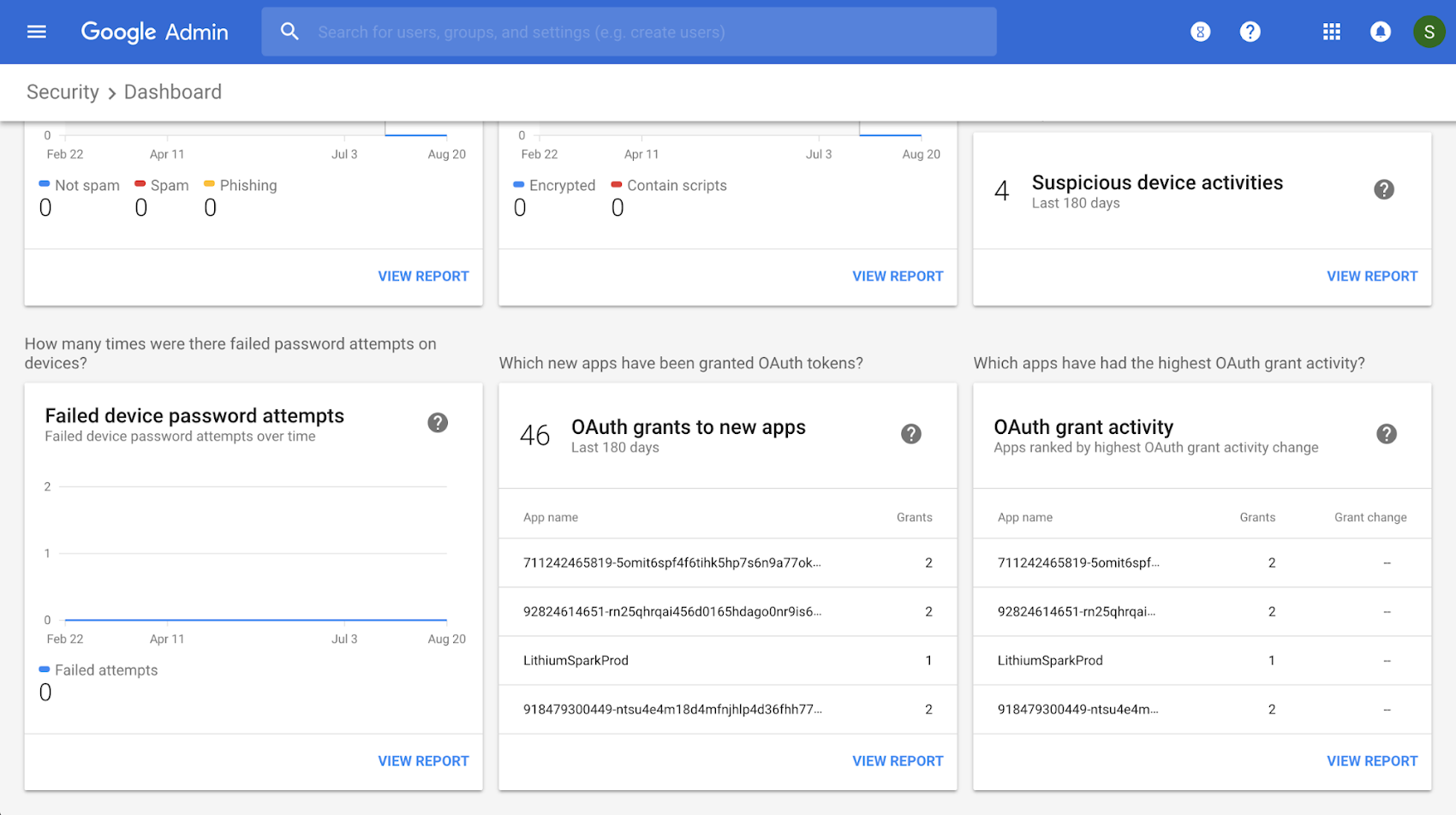
4. Monitor OAuth grants to new apps in the security center
Security dashboard, part of security center for G Suite, includes specific charts on OAuth grants to new apps. These charts highlight useful information for monitoring your domain’s OAuth use. For example, you can monitor which apps received the most new OAuth grants in the last few months from the dashboard.

With these controls and stricter limits on unverified apps, we’re creating a safer OAuth ecosystem and providing tools to help you control, assess and monitor apps that have access to data in your domain. Transparency and control have always been core data privacy principles, and we're constantly working to ensure these principles are reflected in our products. Keep an eye out for more fine-grained API permission controls and organizational unit controls to better manage risk.
If you’re interested in learning more, visit the G Suite Security page.