6 new device, data, and user controls to help G Suite customers stay secure
Brad Meador
Product Lead, Google Workspace Security
Learn about G Suite capabilities and features to simplify and secure remote workforces.
Contact Google Workspace Sales Team
Learn more about how Google Workspace can give your teams a better way to connect, create, and collaborate.
CONTACT USAt G Suite, we know that there’s a new reality facing many IT admins: with an increasingly remote workforce, you’re balancing priorities from business leaders focused on meeting business goals and your CISO focused on security, all while keeping your users online and productive. You’re doing your best, and we’re here to support you and help make remote collaboration easier and more secure.
Secure your organizations’ devices remotely
The dramatic increase in remote devices brought on by the move to remote work makes securing devices even more important. It's critical to ensure that all devices—no matter how they are sourced—are updated with the latest patches, have secure controls turned on, and are in compliance with organizational policies. Additionally, some users may need to buy their own devices or work on personal ones—and access sensitive corporate data on non-corporate devices. The following features can help you enable security at scale.
Fundamental desktop security and enhanced management & security for Windows 10 help to enable endpoint security for your organization, so you can protect your users wherever they’re working. With fundamental desktop security, when a user logs into G Suite in a browser on a Windows, Mac, Chrome, or Linux device, they will be automatically registered with endpoint management, and admins will get controls such as the ability to remotely sign out users if a device is lost or stolen. More than 110 million, 30-day-active devices licensed through G Suite, Cloud Identity, and Chrome Enterprise are managed by our endpoint management solution. Within G Suite and Cloud Identity, multiple devices per user can be managed at no additional cost.
IT admins can now manage and configure Windows 10 devices through the Admin console, just as you would for Android, iOS, Chrome, and Jamboard devices today. You can perform device actions like device wiping from the cloud. Users will also be able to use existing G Suite account credentials to login to Windows 10 devices and easily access apps and services with single sign-on (SSO).


Protect your organization’s data, no matter where your users are located
As an IT admin, you play a critical part in protecting your organization’s sensitive data. That’s why we’re launching data protection insights (Beta) to help you with insights such as “What are the top sensitive data types in your organization.” Insights like these can help you prioritize your security efforts and focus on the most relevant data types for your organization.
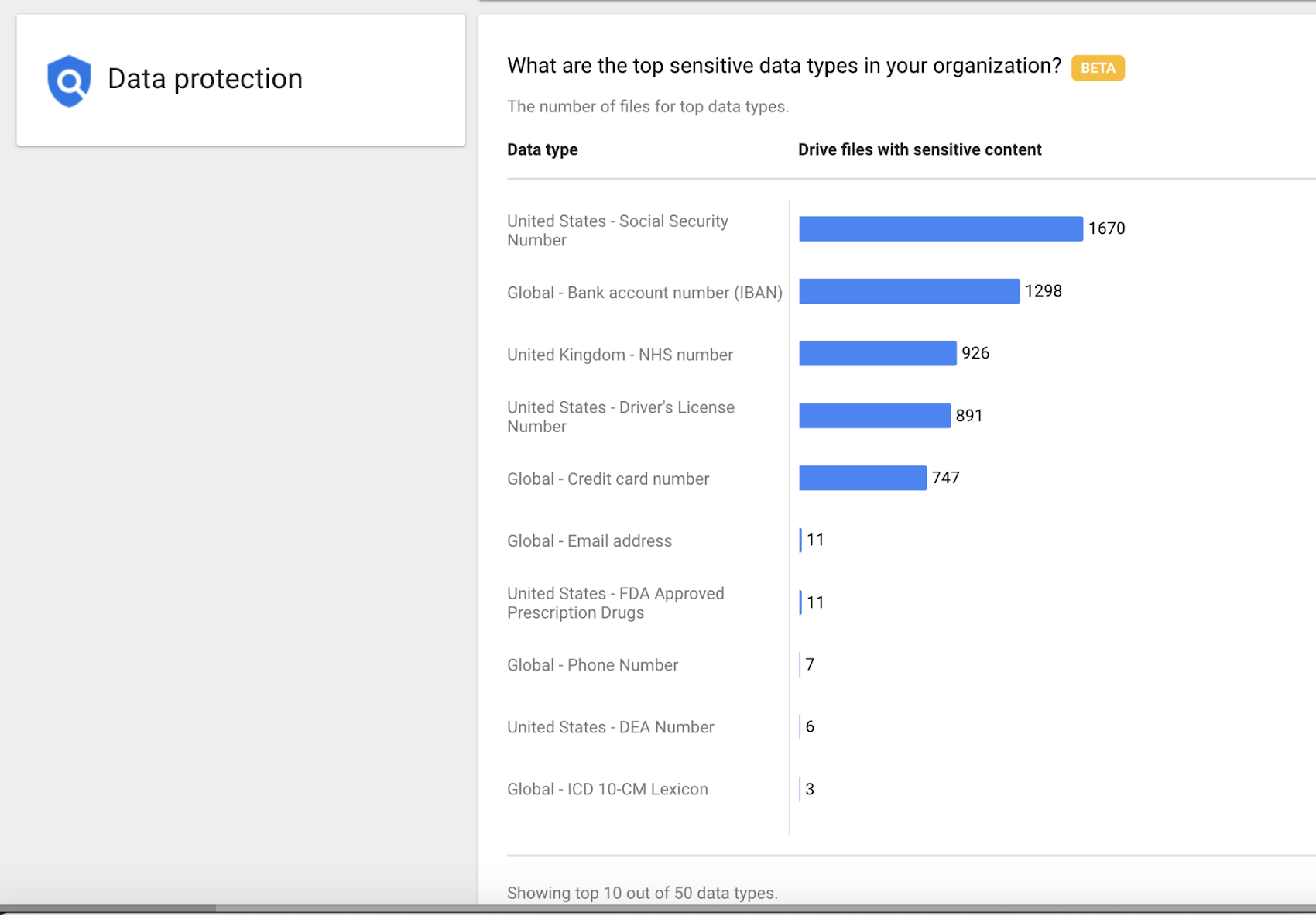

We're also making it easier to manage data proliferation with the ability to automate data classification for Drive files. Automated classification (Beta) enables admins to apply security labels to their data with data loss prevention rules. Coupled with advanced detection technologies, incident management tools, and enhanced alerts, these tools can help you better manage your sensitive data with a remote workforce. Data protection insights and automated classification are both available as part of G Suite Enterprise.
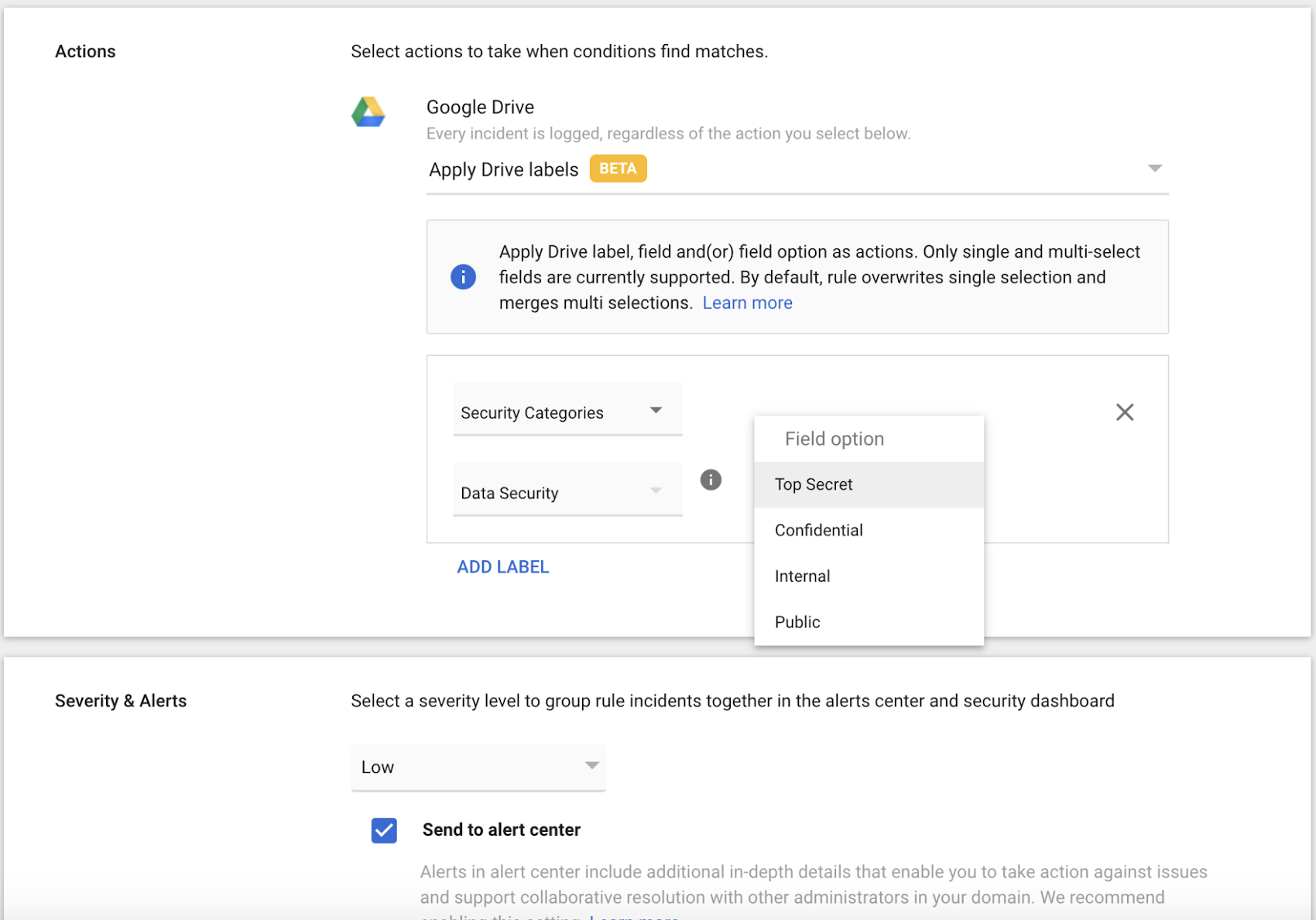

Next, we’re launching additional measures to help ensure that sensitive data does not leave your organization. The Android platform has always provided a clear separation between work and personal accounts in G Suite. We are launching the first of several capabilities that help bring the Android for Work experience to G Suite on iOS. With iOS copy/paste protection, you have the ability to prevent data leaks outside of Gmail, Drive, Docs, Sheets, and Slides for G Suite Enterprise, G Suite Enterprise for Education, and Cloud Identity Premium accounts.
Manage users across geographies with context-aware access
No matter where your users are in the world, it’s important that admins can scale security across different geographies. Based on the zero-trust security model and Google’s BeyondCorp implementation, context-aware access enables you to provide secure access for your users based on dynamic context such as IP, geolocation, and device status. We are now making it even easier to deploy context-aware access by enabling group-based policies as well as extending context-aware access controls to SAML applications. This level of control can be especially helpful to admins who manage teams working from different places globally, as well as those who manage a mix of full-time and part-time workers, as it enables the ability to enact policies for very specific groups of users, irrespective of organizational unit structure.
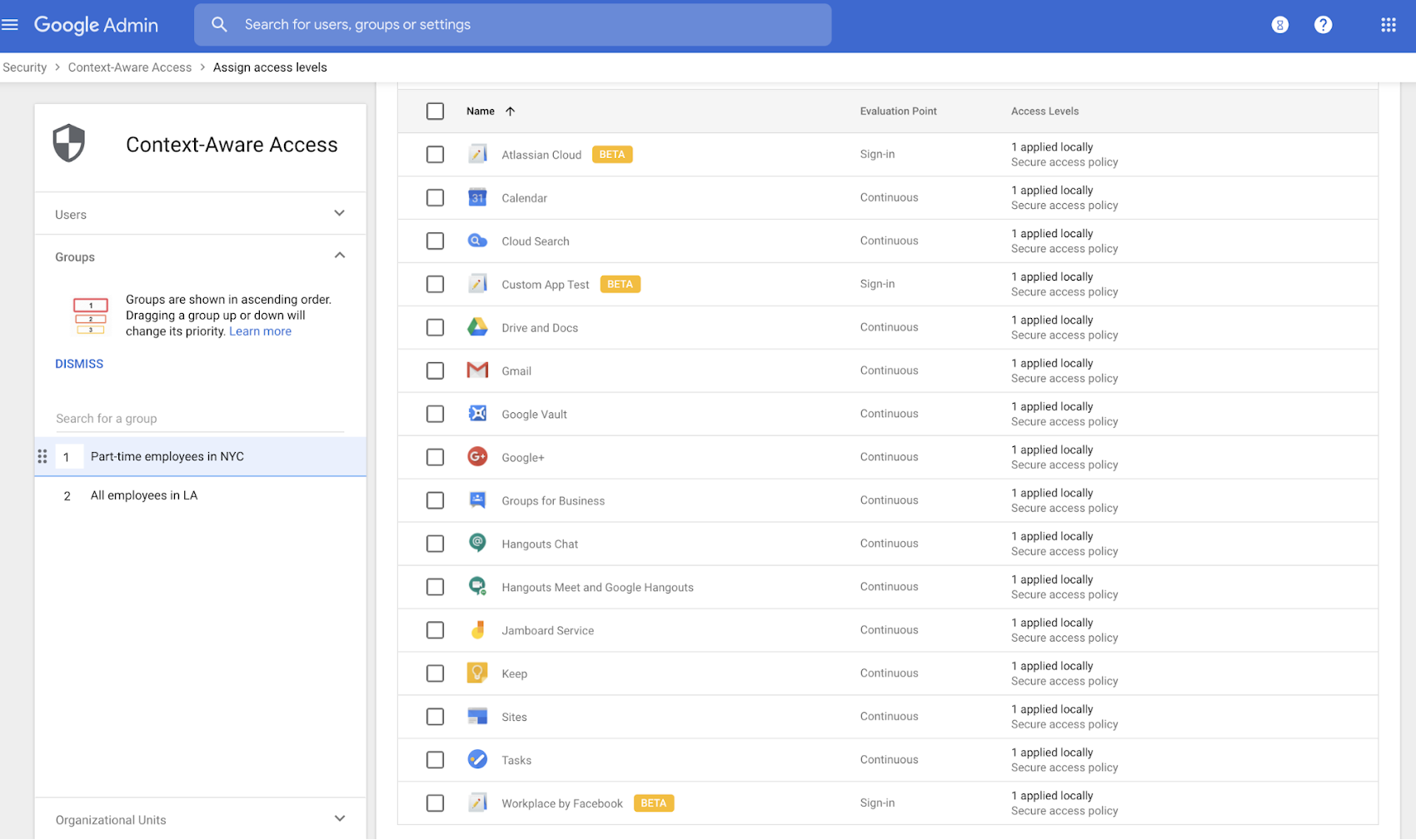

In addition to G Suite applications, your users can use Google sign-in to access critical SAML applications like Salesforce if you are using Google as your primary identity provider (IdP). With context-aware access for SAML applications (Beta), you can now ensure secure sign-in to SAML applications from wherever users are.
Monitor G Suite and Google Cloud Platform logs in one place
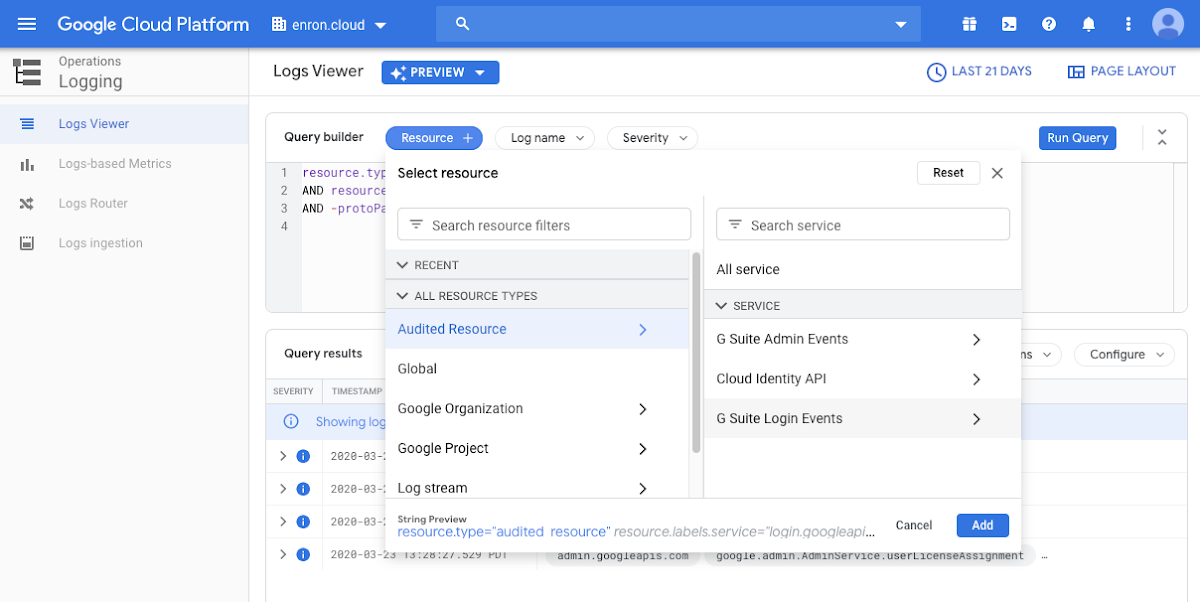
We are making it easier for security teams to monitor G Suite and Google Cloud Platform logs in a single console. G Suite customers can view their G Suite Admin logs directly on Log Viewer, track them with Cloud Monitoring, or export them to their preferred security information and event management provider, like Splunk. This feature is now available in Beta for all G Suite customers.

While you’re enabling your organization’s remote workforce, at G Suite, we will continue to support you with tools that help you protect your organization and users around the world.



