We just released a new edition of our “VirusTotal Malware Trends Report” series, where we want to share VirusTotal’s visibility to help researchers, security practitioners and the general public better understand the nature of malicious attacks, this time focusing on “Emerging Formats and Delivery Techniques”. Here are some of the main ideas presented there:
Email attachments continue to be a popular way to spread malware.
Traditional file types (Excel, RTF, CAB and compressed formats) are becoming less popular. Although the use of PDFs slowly decreased for the last few months in June 2023 we observed the biggest peak for the last two years.
OneNote and JavaScript (distributed along HTML) are the most rapidly growing formats for malicious attachments in 2023.
OneNote emerged in 2023 as a reliable alternative for attackers to the traditional use of macros in other Office products.
ISO files for malware spreading are a flexible alternative for both widespread and targeted attacks. Distribution as heavily compressed attachments makes them difficult to scan by some security solutions.
ISO files are being disguised as legitimate installation packages for a variety of software, including Windows, Telegram, AnyDesk, and malicious CryptoNotepad, among others.
For full details, you can download the report here.
As we usually do, in this blog post we will focus on technical hunting ideas you can use to monitor malicious activity. We also provide additional technical details for some of the most interesting points discussed in the report.
Monitoring malicious attachments
Our data shows that there was an increase in the number of malicious files attached to emails between March and April of 2023. In terms of suspicious attachments, for the past two years, we have observed spikes in the number of suspicious PDF files linked to malicious campaigns. These files can be used for a variety of purposes, such as exploiting vulnerabilities (less usual) or phishing (most of the time).
OneNote is becoming a popular format for malware distributed as email attachments in 2023. We will describe the OneNote attack flow in the next section. In 2023, it became the fastest-growing format for malicious attachments, by percentage.
In 2023, we saw a significant increase in the use of JavaScript distributed alongside HTML, in sophisticated phishing attacks designed to steal victims' credentials. Excel, RTF, CAB, compressed formats, and Word all seem to be declining in popularity as malicious attachments.
OneNote to rule them all
Suspicious OneNote files uploaded to VirusTotal can we filtered using the following VTI query:
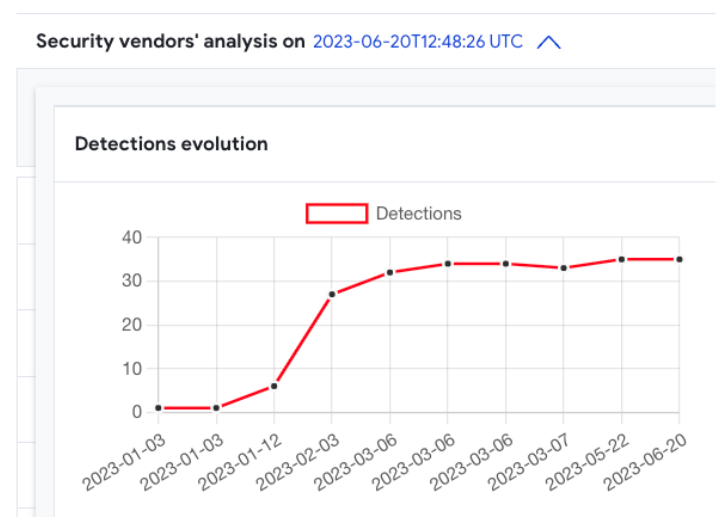
Most of the files in our collection were submitted in 2023. We can observe how AntiVirus detection during January and the first half of February was significantly lower than afterwards, when security vendors improved their detection for this format.
Malicious OneNote files usually embed a malicious file (vba, html+jscript, powershell, or any combination of them) and, as happens with malicious Office attachments, try to convince the victim to allow execution.
Commonalities for the files resulting the previous search offer some interesting data on who is currently using this format for distribution:
Many of them distribute QBot, RemcosRAT or AsyncRAT. We also found Emotet malware samples using Onenote for spreading.
Around 20% seem to distribute QakBot.
The Microsoft_OneNote_with_Suspicious_String Crowdsource Yara rule seems to provide good detection with a low false positive ratio.
Payloads vary from family to family, but many of them access external URLs to download a DLL file camouflaged as a PNG file. This is a very old trick used to bypass basic firewall rules or just look less suspicious to the eye.
We can find several examples of this, for example searching for BumbleBee malware samples reaching a remote "view.png" file or Qakbot samples contacting "01.png" in any network resource.
The most usual kill chain where OneNote format is involved is as follows:
The victim receives an email with a OneNote attachment. The mail body encourages the victim to click on a button to see a hidden/distorted image or document.
This button executes a script (VB script, HTA, powershell, etc,) that will launch a payload, either embedded into the same script or downloaded from an external resource.
The external payload might be yet another OneNote file, an image file renamed as a ".bat" file, a DLL file that's loaded into memory or even a Windows executable.
The following is an example of an obfuscated second stage .Net executable payload extracted from this powershell script:
ISO files as a flexible alternative
Windows-targeting malware bundled in ISO files is a highly popular delivery method used by threat actors these days. It is used on a large scale for crimeware distribution as well as high profile APT campaigns actors. You can use the “isoimage” tag to list ISO files in VTI:
You can be more specific to detect only those ISO files containing an executable:
Another interesting approach is to leverage Sandbox reports to get ISOs files interacting (drop/delete/open/execute) with specific file types during their execution:
Using this method you are not only no longer dependent on the “contains-pe” tag (that could be missed in some cases), but also you are able to discover ISOs with “hidden” executables, for example ISO containing archives that contain executables. It is also possible to detect cases when an ISO file contains only a non-binary file, like LNK or script, that drops and executes a malicious PE payload.
It is possible to identify ISO clusters for specific malware campaigns. For instance, you can get samples used in a ChromeLoader distribution campaign with the following name and size filters:
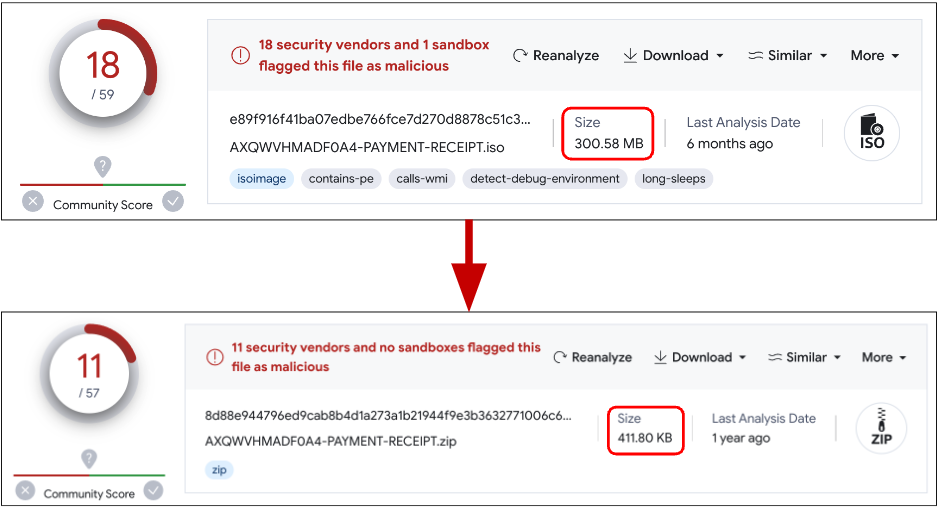
Another interesting ISO cluster contains artificially zero-byte inflated executables, allowing attackers to compress the resulting ISO file from 300Mb to 400Kb:
The following query will help you find some of these examples:
We also found something that appears to be a malware campaign distributing weaponized versions of legitimate software, including “Crypto Notepad”, within ISO files. Examining one of the samples, we can see that the bundled .NET executable is also inflated with zero-bytes up to 313Mb. The main purpose of the malicious injection in legit software is to download a remote binary file for execution:
It is also capable of fetching remotely hosted powershell code and execute it:
We found hundreds of samples related to this campaign related to the following C2 hosts:
Other than compressing artificially inflated files, another reason to distribute ISO files is mimicking legitimate installation software packages, which you usually expect to be sizable. The following example uses a well known browser to find suspicious cases:
The previous search results in a number of files with zero AV detections. However, further manual analysis reveals their maliciousness.
There are different ways to explore what are the main spreading vectors used to distribute malicious ISO files and their related infrastructure. For instance, the following query provides samples seen being hosted In-The-Wild:
You can refine the search to list samples seen being hosted in a specific host:
Email spreading can filtered using the “attachment” tag or “email_parents”, they both provide pretty much the same results:
Wrapping it up
Attackers are constantly rotating the file formats they use to deliver malware. This is done to increase the effectiveness of their campaigns and to avoid detection by security measures. The security community needs to be aware of the use of alternative file formats for malware delivery and to put more resources into stopping these new spreading methods. For example, although traditional file types, such as Word, Excel, and RTF, are still used for malware delivery, alternative formats, such as OneNote and ISO, are becoming increasingly popular.
As a proof of the effectiveness of format rotation for attackers, the simple fact of bundling a malicious sample inside of an ISO file seems to effectively decrease AV detections. We also observed poor detection in the first waves of OneNote malicious files, although improved with time.
We suggest monitoring malware spreading trends, and actively check how your security stack responds to proactively minimize infection risks, as well as including in your analysis all logs to/from allowed legitimate sites as they are regularly used for malware distribution, do not exclusively focus your anomaly detection on unknown traffic.
Happy hunting!

.png)