Monitor your cloud-based assets as if they were in your LAN.
Advanced Cloud IDS >
harness the power of intelligence sharing.
Machine Learning Uncovers Hidden Patterns >
Analyze actionable incident reports rather than isolated alerts.
Advanced Intrusion Detection >
Create and analyze historical packet captures of your network traffic.
Ultimate Threat Hunting >
Advanced Intrusion Detection
Accurately identify and block malware, dangerous user behavior and data exfiltrations that would otherwise go unnoticed.
The MetaFlows Security System
Data Sources
The MetaFlows Security System (MSS) can be deployed in public clouds such as AWS, Azure or GCP, corporate networks and data centers.
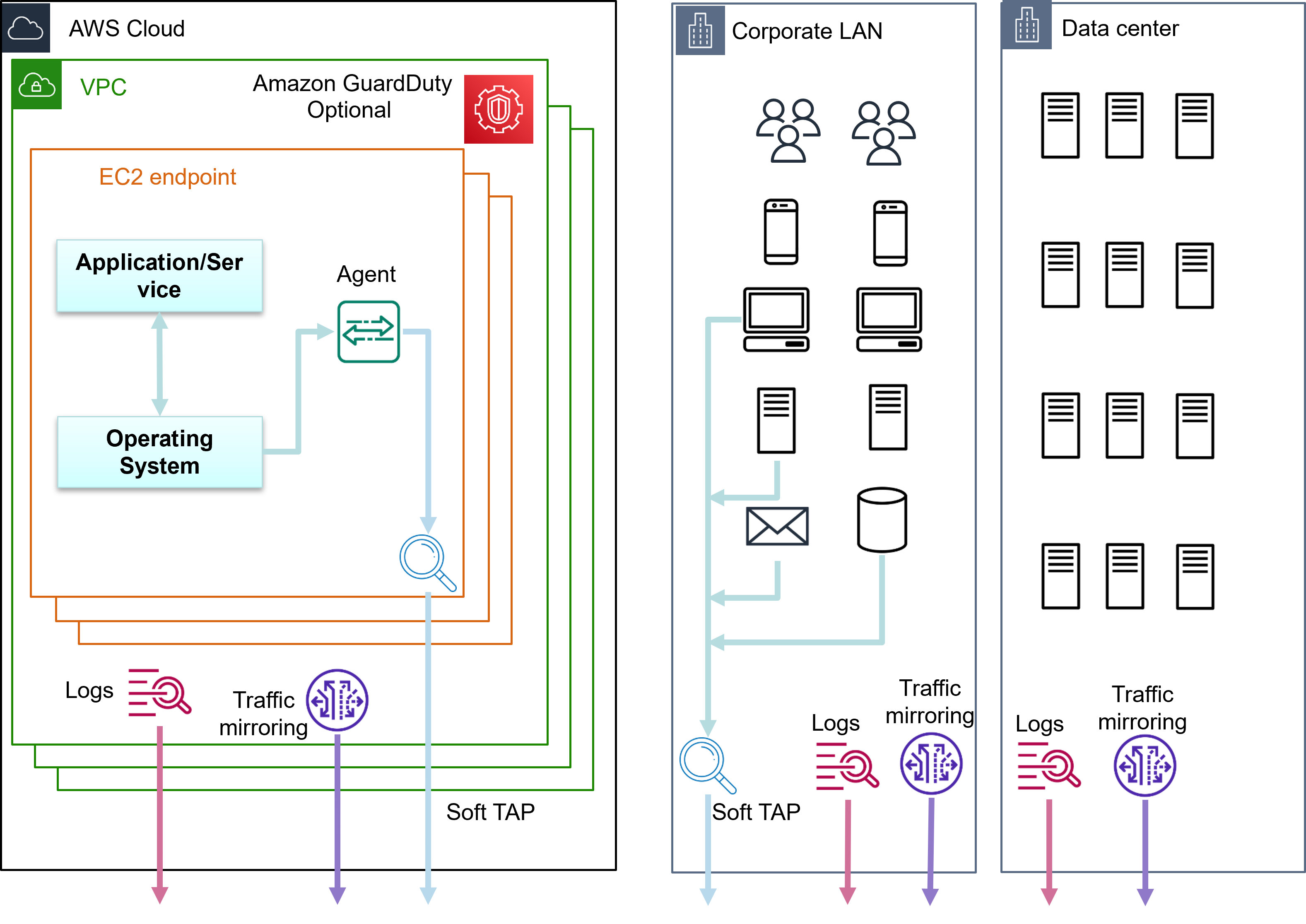
Besides leveraging cloud-specific services such as VPC mirroring and Amazon GuardDuty, the MSS can also be deployed in traditional on-premise environments to process up to 10 Gbps per sensor.
 |
Traffic mirroring can be achieved through VPC mirroring, hardware span/mirror ports, TAPs or agents installed on the endpoints. |
 |
System and event logs can be natively exported or gathered with Windows agents. |
| MetaFlows provides unique support to implement software TAPs (pcap over TLS) in any infrastructure. |
Sensors
Sensors are CentOS/RHEL systems dedicated to passively analyze network data. Our software scales with the amount of available hardware from a minimum of 1 CPU and 4 GB of RAM for processing up to 50 Mbps to multiple-core systems capable of processing up to 10 Gbps. The amount of disk storage indirectly affects the maximum time horizon for historical packet log queries. For most sensors 1 TB of total storage is sufficient. Sensors perform the following functions:
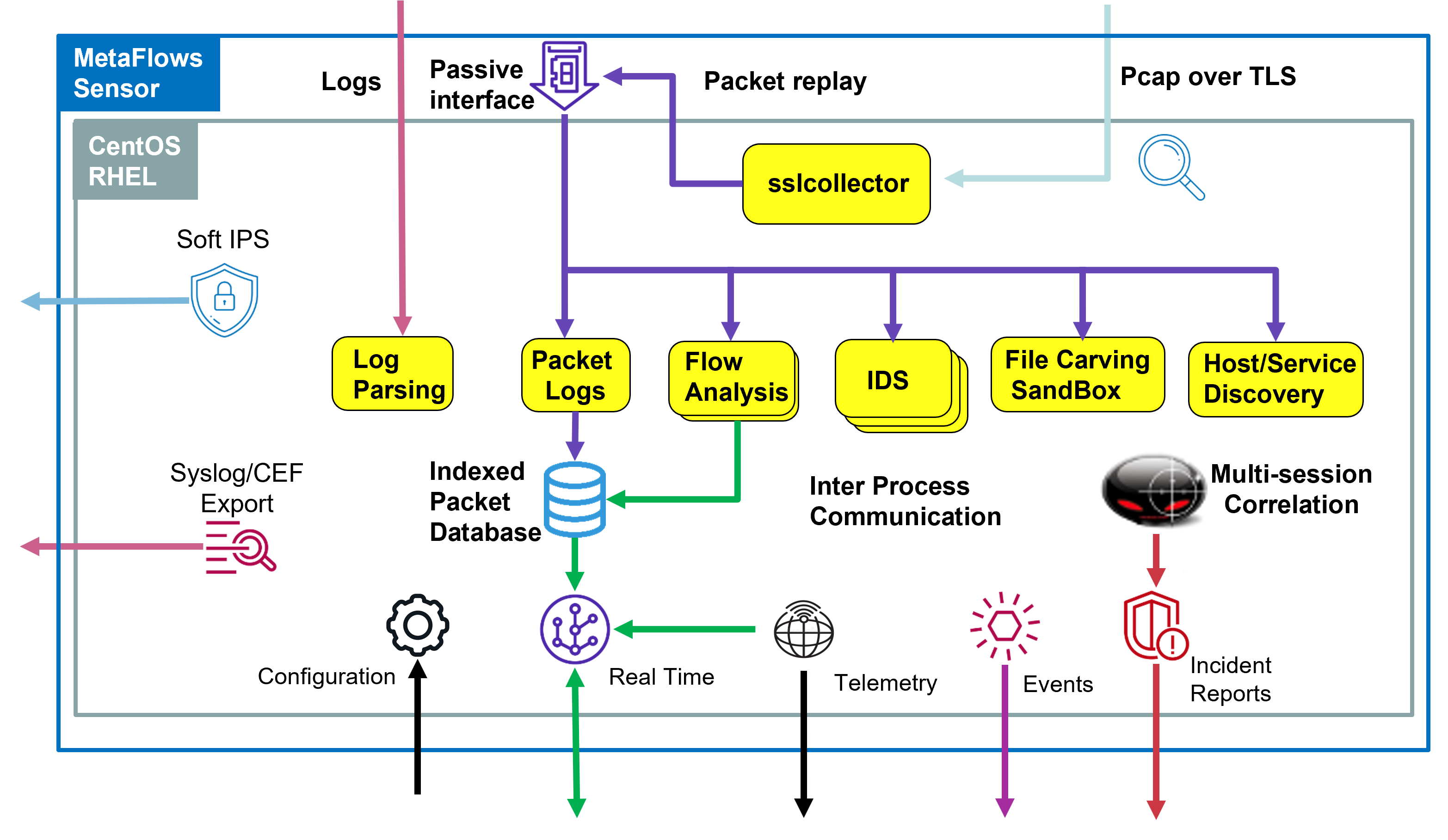
| Correlate IDS events, communication patterns, event logs and application downloads. | |
| Provide Intrusion Prevention through Soft IPS. | |
 | Store all packets in a local indexed database. |
 | Offer users real time flow data and access to the packet database using web sockets. |
| Optionally use software-based TAPs. | |
 | Optionally export alerts to third party SIEMs |
The Controller
The controller is at the heart of our SaaS technology. MetaFlows offers two publicly accessible controller systems; one in the commercial AWS EC2 cloud and one in the AWS Govcloud. Most users will just deploy sensors and use one of these two public SaaS services to monitor their networks. We can also license dedicated controllers to Government organizations or very large enterprises to implement an equivalent, self-managed SaaS platform for private use.
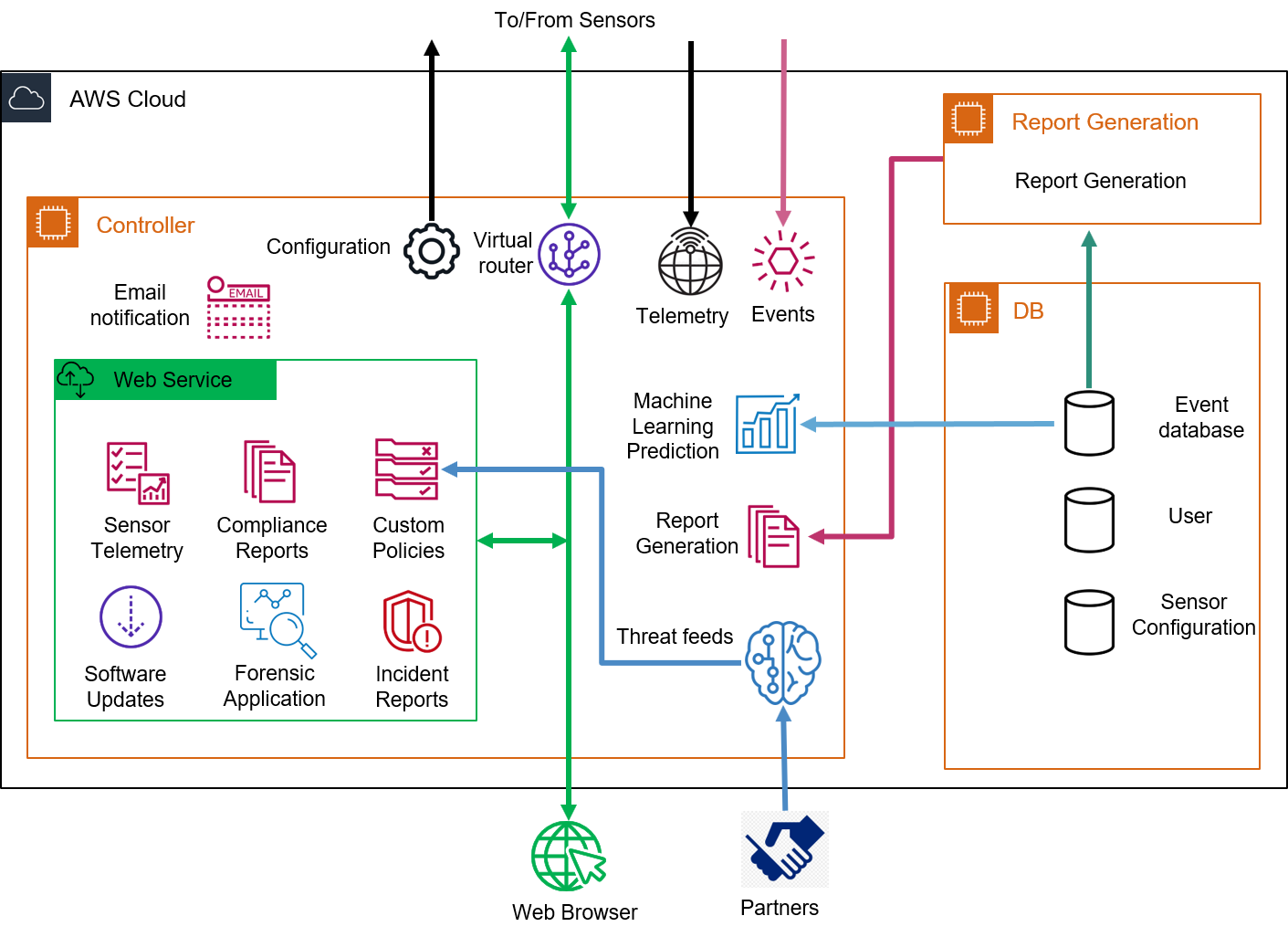
 | Receives and stores alerts and telemetry data from all Sensors |
 | Uses Machine Learning to dynamically assign event priorities. |
 | Ingests and normalizes threat feeds to be provided to the sensors. |
 | Provides a real time transport service for browser-to-sensor comminication. |
| Hosts a powerful web-based forensic application for viewing security events and reports | |
 | Provides configuration management of IDS rules, notification policies, IPS policies, filtering policies and customizable reports. |
Important advantages of our solution
Advanced Threat Hunting & Forensics
MetaFlows' network intrusion detection software provides indexed packet logging to easily reconstruct what happened in your network past. The time horizon is directly proportional to the storage to bandwidth ratio and can range from a few hours to a few weeks depending on the setup. The time horizon can be adjusted by sizing the storage capacity while leveraging our proprietary packet indexing technology to scale your forensic capabilities to a whole new level.
MORE >
Machine Learning uncovers hidden patterns
Our system compares and correlates event data gathered across all our customers. An algorithm mathematically similar to Google’s page ranking adjusts the priority of certain events to make sure important information stands out. Just as the first few web pages of a Google search yield the most relevant results, each customer's events are mathematically prioritized to highlight the most globally relevant information.
MORE >
Block Threats Without Impacting Reliability
Soft IPS is ground-breaking software-based Intrusion Prevention technology that shuts down threats with zero impact on performance and reliability. It uses powerful active response technology to block unwanted traffic and actively learns which flows need to be blocked by extracting invariants from your unwanted communication patterns.
MORE >
What customers say about us
Read our verified customer reviews on Gartner Peer Insights
MetaFlows Security System
Cost effective Malware detection Solution for Cloud
We were looking out for an IPS solution for AWS and came across through Metaflows Malware Detection Solution. Its Cost effective, bit difficult to deploy but easy to understand solution. Malware detection capability is great.

MetaFlows Security System
Great system, easy to setup, great support
Metaflows does a great job in intrusion detection and prevention, and has stopped many new infections on our network from getting outside of the network. The interface itself could use some work, as far as ease of use, but once you can get around in the system it's not bad at all and full-featured. Their support is FANTASTIC, and they will quickly answer your call (I have never had a wait time) and immediately assist you in whatever you need. They are very, very knowledgeable about their product, and will help you tune your sensors to however you see fit.

MetaFlows Security System
Excellent product backed up by a team of experts
They were extremely helpful with installation and have gone above and beyond in providing quick and accurate support.


